We may not have the course you’re looking for. If you enquire or give us a call on +39 800580270 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
In today’s technological and interconnected world, maintaining robust Cybersecurity measures is no longer a choice—it's an absolute necessity. As businesses expand their digital footprint and individuals share sensitive information online, the need to safeguard data from prying eyes and malicious attacks has never been more pressing. This is where the Microsoft Security Account Manager (SAM) steps onto the stage.
However, many organisations are still unaware of the many benefits that this database provides. Read this blog to explore how Microsoft Security Account Manager boosts digital security and its significance and harness the power of SAM.
Table of Contents
1) Delving deeper into the Security Account Manager (SAM)
2) How Microsoft Security Account Manager works?
3) Significance of SAM in Microsoft environments
4) Security concerns and best practices for SAM
5) Conclusion
Delving deeper into the Security Account Manager (SAM)
SAM is a cornerstone of Microsoft's security framework. It safeguards user account information diligently, providing Windows users peace of mind. Every Windows installation contains a SAM database, which is present even in personal computers, simplifying tracking and authentication processes. This results in efficient system administration.
One might ask, "Why not store actual passwords?" Storing raw passwords presents significant risks. Cyberattacks can expose or steal them. With hashing, even if hackers access Microsoft Security Account Manager, deciphering passwords remains a challenge. SAM's hashing process is unique. It uses a specific algorithm proprietary to Microsoft. This ensures distinct password representations.
Periodic updates have bolstered SAM's defences. Microsoft constantly refines its encryption techniques. Users are thus shielded from emerging cyber threats. It's also worth noting SAM's adaptability; while it's an older tool, it's not obsolete. Microsoft ensures it complements newer technologies. Furthermore, SAM is not an isolated entity. It collaborates with other system components. This synergy fortifies overall system security.
Secure your future in tech by registering for our Microsoft Security Operations Analyst SC-200 Training now!
How Microsoft Security Account Manager works?
Understanding SAM's operations requires a detailed understanding. Its processes are intricate, yet they ensure smooth user authentication. Let's break down its functions step-by-step:
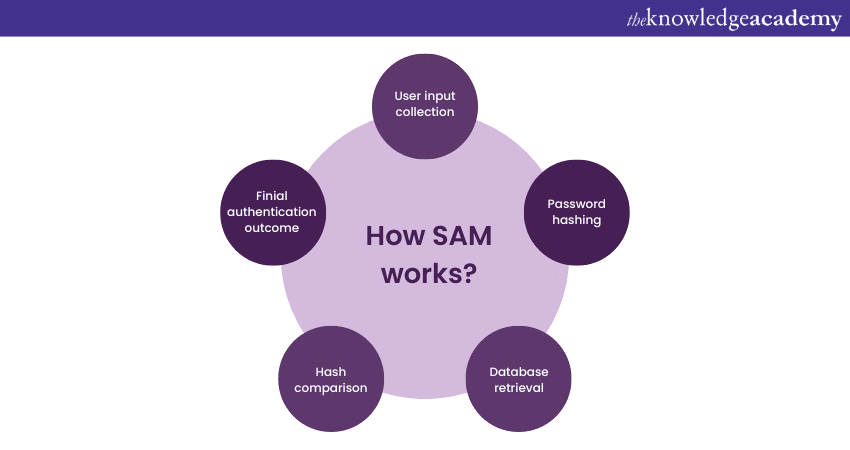
The Windows login screen is user-friendly. It prompts for essential credentials like username and password. These credentials are the user's unique identity. Microsoft Security Account Manager uses them to determine system access.
Password hashing
Hashing isn't just a random transformation. It's a sophisticated cryptographic process. When users enter a raw password, the result is a complex hash, almost indecipherable. This ensures the original password remains confidential and security is maintained. It guarantees a unique output for every distinct password.
Database retrieval
The Microsoft Security Account Manager database is a secure vault. Each registered Windows user has an entry here, containing a username and its associated hash. When a user attempts to log in, SAM accesses this database. It retrieves the stored hash for the entered username. This stored hash is vital for the next authentication step.
Elevate your cybersecurity skills by registering for our Microsoft Security Engineer Training today!
Hash comparison
This step is a delicate balancing act. SAM holds the user's hash in one hand and the database's hash in the other. The two are then placed side by side. A match confirms the password's authenticity. At the same time, a mismatch indicates an incorrect password entry.
Final authentication outcome
The outcome depends on the hash comparison. A successful match leads to a welcome screen. The user gains full access to their Windows environment. A mismatch results in an error message. The system prompts the re-entry of credentials. Multiple unsuccessful attempts may lead to a temporary lockout. This is an added security measure against unauthorised access.
Significance of SAM in Microsoft environments
The Microsoft Security Account Manager isn't just another system component. It holds pivotal importance within its environment. Its multifaceted role ensures security, efficiency, and integration. Here's why Microsoft’s SAM is of great significance:
Centralised user management
At the heart of Windows systems lies SAM. It offers a central hub for managing user data. Administrators gain a unified view of user credentials. They can oversee, modify, or delete accounts seamlessly. This centralisation eases the administrative burden. It ensures consistent user data across multiple services.
Robust security layer
SAM is more than a database. It's a shield against unauthorised access. By storing hashed passwords, it thwarts potential breaches. Cybercriminals can't easily decipher these hashes. Thus, even in security incidents, raw password data remains protected. SAM's design inherently prioritises user security.
Seamless integration with Microsoft services
Microsoft offers a suite of services and tools. SAM is designed to blend effortlessly within this ecosystem. One notable example is its integration with Active Directory, which facilitates large-scale user management. SAM's adaptability ensures it remains relevant. It complements newer technologies and systems within Microsoft's fold.
Scalability for growing networks
Organisations grow, so do their IT needs. Microsoft System Account Manager is equipped to handle this growth. From a small business to a large enterprise, SAM is scalable. It can accommodate increasing user numbers. Its design ensures performance doesn't lag, irrespective of the network's size.
Endorsing best practices
SAM doesn't just operate in isolation. It encourages the best security practices. By necessitating strong passwords and secure storage, it sets a standard. Organisations that use SAM are nudged towards better security habits. It's a silent guide towards more secure IT environments.
Security concerns and best practices for SAM
Even the most robust systems have vulnerabilities. While SAM is secure, it's essential to understand its concerns and follow best practices for optimum safety. Let's explore these concerns and best practices in detail:
a) Password hash extraction threat: Among the most pressing concerns is hash extraction. If attackers access SAM's hashes, they might attempt password cracking. This involves using tools to guess the password corresponding to a hash.
b) Limiting SAM file accessibility: Directly accessing the SAM file is a potential threat. Unauthorised access can lead to data breaches. Ensuring only privileged users can reach it is crucial. Thus, permissions should be strictly controlled and audited.
c) Embracing strong password policies: The strength of a password influences SAM's efficacy. Simple passwords can be cracked faster. Encourage users to adopt complex passwords, like mixtures of characters, numbers, and symbols, to enhance security.
d) Regular backups and monitoring: Frequent backups of the SAM database are essential. They provide a safety net in case of corruption or breaches. Additionally, monitoring for unauthorised access attempts ensures timely threat detection.
e) Employee training and awareness: Often, human error can be a weak link. Training staff on security protocols reduces risks. Moreover, awareness campaigns about phishing or suspicious activities can safeguard against indirect SAM threats.
Conclusion
Today, Microsoft Security Account Manager stands as a testament to Microsoft's forward-thinking approach and commitment to user security. Its evolution has mirrored the changing needs of users, ensuring that from individual consumers to multinational corporations, user authentication remains robust, secure, and efficient. Over the years, through consistent refinement and adaptation, SAM has proven its worth, underlining its role as a cornerstone in the Microsoft security framework.
Master the basics of security and compliance. Register for our Microsoft Security, Compliance, And Identity Fundamentals SC900 Course today!
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Microsoft Cybersecurity Architect SC100
Microsoft Cybersecurity Architect SC100
Thu 1st Jan 1970







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


