We may not have the course you’re looking for. If you enquire or give us a call on +39 800580270 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Ever wonder how the internet delivers your urgent messages, favourite videos, and data across the globe in seconds? It's almost like there's a common language that connects every device across the web. The answer lies in Network Protocols. Whether it’s TCP/IP directing traffic, HTTPS securing transactions, or DHCP assigning IP addresses, protocols keep the digital world running smoothly. This blog explores these protocols in detail, outlining popular examples, types, how they work and more. So read on and learn how these tools keep the fabric of modern modern digital connectivity stitched together!
Table of Contents
1) What is a Network Protocol?
2) Who Uses Network Protocols?
3) Types of Network Protocols
4) How do Network Protocols work?
5) Network Protocols Examples
6) What are the 4 Layers of Network Protocols?
7) What is the Most Widely Used Network Protocol?
8) Conclusion
What is a Network Protocol?
A Network protocol is a set of standards governing how data is exchanged between devices in a network. These Protocols define various aspects of communication, including:
1) Format of data packets
2) Order of transmission
3) Error handling
These standardised Protocols are necessary for devices to understand each other, leading to chaos in the digital realm. Here are some key points to remember about Network Protocols:
1) Network Protocols define the format and structure of data packets.
2) Data is broken into smaller units called packets for transmission.
3) Packets include source and destination addresses, sequence numbers, and error-checking codes.
4) Protocols ensure packet formatting consistency and compatibility across devices.
5) They establish rules for sending, receiving, and ordering packets.
6) Handle errors, retransmissions, and flow control to prevent congestion.
7) Optimise communication efficiency and reliability between networked devices.
Who Uses Network Protocols?
A wide range of individuals and systems including the following uses Network Protocols:

Types of Network Protocols
Network Protocols are the cornerstone of modern communication, providing the framework for data exchange across interconnected devices. Understanding the different types of Network Protocols is essential for comprehending how information flows within a network infrastructure.
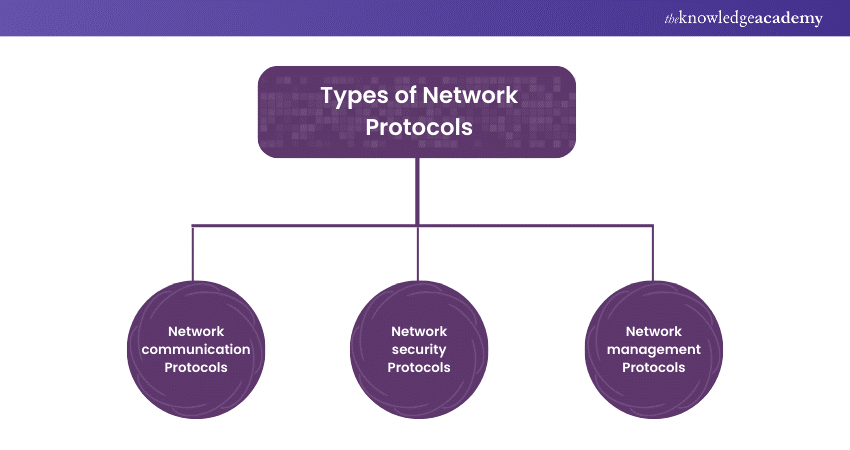
1) Network Communication Protocols
a) Examples of communication protocols include TCP/IP (Transmission Control Protocol/Internet Protocol), UDP (User Datagram Protocol), HTTP (Hypertext Transfer Protocol), and SMTP (Simple Mail Transfer Protocol).
b) These protocols ensure data travels efficiently and reliably across the network, enabling seamless communication between devices.
c) One of the primary functions of communication protocols is addressing.
d) They establish rules for identifying the source and destination of data packets, enabling devices to communicate effectively.
e) Through mechanisms like IP addressing, communication protocols facilitate the routing of packets through the network, directing them along the most efficient path to their destination.
Master domain management, hosting services, and website deployment in our Introduction to Domain Names and Web Hosting Training - Register now!
2) Network Security Protocols
Network security protocols constitute a critical aspect of modern networking infrastructure, primarily dedicated to fortifying networks against a plethora of cyber threats; however, understanding the disadvantages of using VPN is essential, as certain VPN protocols may introduce security vulnerabilities.
a) With the proliferation of interconnected devices and the increasing dependency on digital communication, robust security measures are crucial.
b) These protocols include diverse mechanisms to safeguard sensitive data, prevent unauthorised access, and mitigate security breaches.
c) Encryption protocols, such as SSL/TLS and IPsec, play a key role in securing data transmissions.
d) These protocols encode information so that only authorised parties can decipher it, ensuring confidentiality.
3) Network Management Protocols
Managing a complex network infrastructure requires meticulous oversight and control, which is where Network Management protocols come into play. These Protocols facilitate device configuration, monitoring, troubleshooting, and performance optimisation.
a) Examples of Network Management protocols include SNMP (Simple Network Management Protocol), ICMP (Internet Control Message Protocol), and DHCP (Dynamic Host Configuration Protocol).
b) These protocols provide administrators with the tools needed to manage network resources efficiently, including network troubleshooting tools that help quickly identify and resolve network issues.
c) Network Management protocols serve as the administrative backbone of complex network infrastructures.
d) They facilitate efficient oversight, control, and optimisation of network resources.
e) These protocols enable Administrators to perform a wide range of tasks remotely, ensuring the smooth operation of networks.

Learn about security-based and layer-based VPN architectures in our comprehensive VPN Training - Sign up now!
How do Network Protocols Work?
Understanding how Network Protocols function is crucial to grasping the intricacies of communication in modern computer networks. Let's explore deeper into the inner workings of Network Protocols to gain a comprehensive understanding of their operation.
1) Standardisation and Protocols: Network Protocols rely on standardised rules and conventions to ensure seamless communication between devices.
a) These standards are set by organisations like the Internet Engineering Task Force (IETF) and the Institute of Electrical & Electronics Engineers (IEEE).
b) Aligning with these standards ensures seamless communication between devices from different Manufacturers.
c) Such standardisation enables compatibility, regardless of hardware or software differences.
2) Packetisation: One of the fundamental concepts of Network Protocols is packetisation. Data is fragmented into smaller chunks called packets before transmission. Each packet contains:
a) Data
b) Sequence numbers
c) Source and destination addresses
d) error-checking codes
The benefits of packetisation include the following:
a) It enables efficient transmission over the network
b) it allows data to be sent in smaller chunks instead of a continuous stream
3) Addressing and Routing: Network Protocols handle addressing and routing to ensure that packets reach their intended destination. Each device in a specific network is assigned a unique identifier, like an IP address, which is used to route packets. Routing Protocols include the following:
a) Border Gateway Protocol (BGP)
b) Open Shortest Path First (OSPF)
They determine the optimal path for packet transmission based on network topology, congestion levels, and quality of service requirements.
4)Transmission Control: Transmission control is another crucial aspect of Network Protocols. Protocols like TCP (Transmission Control Protocol) provide reliable, connection-oriented communication by implementing acknowledgement, retransmission, and flow control mechanisms.

5) Error Detection and Correction: Network Protocols incorporate mechanisms for error detection and correction to maintain data integrity during transmission. For example, Protocols like TCP use checksums to detect errors in transmitted data packets. If an error is found, the protocol can request retransmission of the corrupted packet to ensure the data arrives intact.
6) Protocol Stack: Network Protocols are often organised in a hierarchical structure known as a protocol stack. The most commonly used protocol stack in modern Networking is the TCP/IP stack, which consists of multiple layers, including the following:.
a) Application layer
b) Transport layer
c) Network layer
d) Link layer
7) Interoperability and Compatibility: Interoperability and compatibility are essential considerations in Network Protocol design. Protocols must be interoperable with existing infrastructure and compatible with various devices to ensure seamless communication across heterogeneous networks. Standardisation efforts help address these concerns by establishing Protocols and ensuring widespread adoption.
8) Evolution and Adaptation: Network Protocols continuously evolve to meet the changing demands of modern Networking environments. New Protocols are developed to address emerging technologies and challenges, while existing Protocols are updated to incorporate improvements and address vulnerabilities. This evolution ensures Network Protocols remain robust, efficient, and secure despite threats and technological advancements.
Gain in-depth knowledge about the workings of Cloudflare with our Cloudflare Training – Sign up today!
Network Protocols Examples
Network Protocols are the unsung heroes of modern communication, enabling seamless data exchange and facilitating the smooth operation of interconnected devices. Let's delve deeper into some prominent examples of Network Protocols and explore their roles and applications in the digital realm.
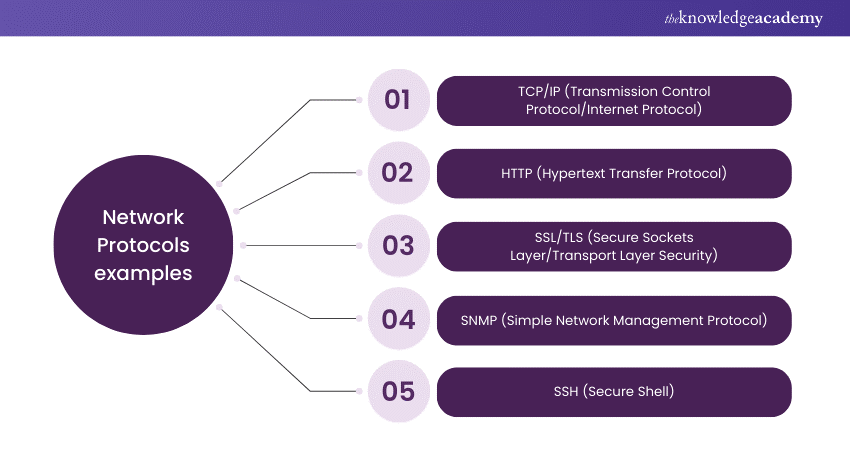
1) Transmission Control Protocol/Internet Protocol (TCP/IP):
TCP/IP stands as the cornerstone of modern Networking, serving as the primary protocol suite for transmitting data across the Internet. It comprises two main Protocols: TCP and IP. TCP ensures the trustworthy delivery of data by establishing connections, breaking data into packets, and reassembling them at the destination.
2) Hypertext Transfer Protocol (HTTP):
As the protocol behind the World Wide Web, HTTP facilitates the retrieval and display of web pages in browsers. It works on a client-server model, where a client, which can be a web server, sends requests to a server (hosting a website), and the server responds with the requested content. HTTP dictates the format of these requests and responses, enabling seamless browsing experiences for users worldwide.

3) Secure Sockets Layer/Transport Layer Security (SSL/TLS):
SSL/TLS Protocols are instrumental in securing communications over the Internet. They establish encrypted connections between clients and servers, safeguarding sensitive data from eavesdropping and tampering. SSL/TLS Protocols are commonly used in secure browsing (HTTPS), email encryption (SMTPS, POP3S, IMAPS), and virtual private Networks (VPN).
4) Simple Network Management Protocol (SNMP):
SNMP facilitates the remote management and monitoring of network devices. It enables Network administrators to gather information regarding the status and performance of switches, routers, servers, and other network components. SNMP operates on a Manager-agent model, where a central management station (Manager) communicates with network devices (agents) to retrieve data, configure settings, and detect faults.
5) Secure Shell (SSH):
SSH or Secure Shell is a cryptographic network protocol used for secure and remote access to network devices and servers. It provides a secure alternative to traditional remote login methods (e.g., Telnet) by encrypting communication sessions between clients and servers. SSH supports various authentication methods, including passwords, public-key cryptography, and multi-factor authentication, ensuring secure access to sensitive systems and data.
Stay at the forefront of IT skills and fundamentals with our IT Fundamentals Training – Join today!
What are the 4 Layers of Network Protocols?
The four layers of network protocols are:
1) Application Layer: Includes HTTP and FTP.
2) Transport Layer: Includes TCP and UDP.
3) Internet Layer: Includes IP and ICMP.
4) Link Layer: Includes Ethernet and Wi-Fi.
What is the Most Widely Used Network Protocol?
TCP/IP are the two most commonly used network communication protocols.
Conclusion
Network Protocols have become the foundation of modern communication systems, enabling seamless data exchange across interconnected devices. Whether facilitating communication, ensuring security, or streamlining Network Management, these Protocols are pivotal in shaping the digital landscape. By adhering to standardised rules and conventions, Network Protocols ensure interoperability and reliability, laying the groundwork for today's interconnected world.
Gain insights into Networking with our Introduction to Networking Training– Join today!
Frequently Asked Questions
How to Check Network Protocol?

Follow these steps:
a) Click on the 'Start menu' and go to 'Settings', then choose 'Control Panel'.
b) In the 'Control Panel', double-click 'Network' to open the 'Network control panel'.
c) Navigate to the 'Protocols tab' to view the installed Network Protocols.
d) Check for NetBIOS, NetBEUI, TCP/IP, or LANBIOS (if using a LANtastic network).
What is the Fastest Network Protocol?

User Datagram Protocol (UDP), Fast and Secure Protocol (FASP) and HTTP/3 are among the fastest Network Protocols.
What are the Other Resources and Offers Provided by The Knowledge Academy?

The Knowledge Academy takes global learning to new heights, offering over 3,000 online courses across 490+ locations in 190+ countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.
What is Knowledge Pass, and How Does It Work?

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.
What are the related IT Support and Solution courses and blogs provided by The Knowledge Academy?

The Knowledge Academy offers various IT Support and Solution Training including VPN Training, Snort Training, and IT Fundamentals training. These courses cater to different skill levels, providing comprehensive insights into the Escalation Matrix.
Our IT Infrastructure & Networking Blogs cover a range of topics related to IT Businesses, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your IT skills, The Knowledge Academy's diverse courses and informative blogs have you covered.
Upcoming IT Infrastructure & Networking Resources Batches & Dates
Date
 Introduction to Networking Training
Introduction to Networking Training
Fri 4th Apr 2025
Fri 6th Jun 2025
Fri 8th Aug 2025
Fri 3rd Oct 2025
Fri 5th Dec 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


