We may not have the course you’re looking for. If you enquire or give us a call on + 1-866 272 8822 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Ensuring the security of your company's assets starts by having a clear understanding of what you possess and where is it. How can this be accomplished? That is when an Asset Inventory for ISO 27001 steps in. This isn't just a basic list; rather, it's a tactical instrument created to protect your business.
An Asset Inventory extends beyond just listing hardware and software items. It consists of essential details, important staff members, and all critical resources in your company. Every asset is given a specific owner who oversees its safety and quality. This stockpile acts as your primary defence, allowing you to efficiently control risks and safeguard confidential information.
This inventory serves as the cornerstone of a strong Information Security Management System (ISMS), going beyond just a form of protection. It assists in guaranteeing that your company complies with regulations and maintains a robust, secure defence against possible dangers.
Are you prepared to improve your company's security measures? Begin by creating a detailed Asset Inventory. This blog will walk you through the required steps to guard your assets and ensure the security of your business.
Table of Contents
1) What are Assets According to ISO 27001?
2) What is an Asset Inventory in ISO 27001?
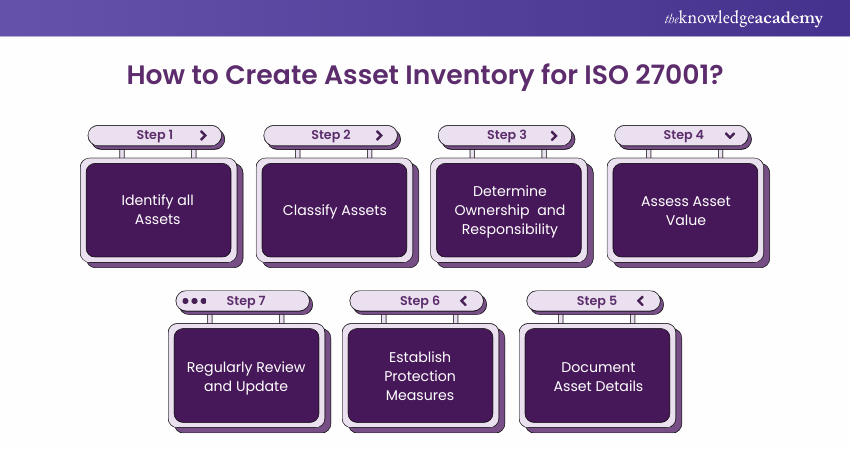
3) Steps to Create an Asset Inventory for ISO 27001
a) Step 1: Identify all Assets
b) Step 2: Classify Assets
c) Step 3: Determine Ownership and Responsibility
d) Step 4: Assess Asset Value
e) Step 5: Document Asset Details
f) Step 6: Establish Protection Measures
g) Step 7: Regularly Review and Update
4) Conclusion
What are Assets According to ISO 27001?
In accordance with ISO 27001, Assets extend far beyond traditional physical items like computers and servers. ISO 27001 defines Assets as encompassing anything of value to an organisation, creating a broader and more holistic perspective. These Assets include but are not limited to, digital Assets such as databases, software, and intellectual property, as well as personnel and the physical infrastructure.
In essence, anything that holds value for the organisation, whether tangible or intangible, is considered an Asset under ISO 27001. This comprehensive definition underscores the importance of recognising the full spectrum of Assets that must be identified, assessed, and protected to ensure robust Information Security Management.
What is an Asset Inventory in ISO 27001?
In ISO 27001, an Asset Inventory serves as a foundational element of Information Security Management (ISM). It is a systematic and comprehensive record-keeping system that catalogues all assets within an organisation. These assets extend beyond traditional notions of hardware and software to encompass everything of value, including data, intellectual property, personnel, and physical infrastructure.
The purpose of an Asset Inventory is multi-fold: it facilitates risk assessment, vulnerability analysis, and the development of security controls. Categorising and valuing Assets helps organisations make the right decisions concerning the allocation of resources to protect their most critical components. Essentially, an Asset Inventory is the bedrock upon which effective Information Security Management is built.
Another important factor of Asset Inventory is its function in distributing resources. Organisations can make strategic security decisions by categorising assets and assigning value to each one. This guarantees efficient allocation of resources, prioritising the highest levels of protection for the most critical assets. Valuing assets aids in emphasising their significance within the organisation, leading to improved prioritisation in security planning and management. The Asset Inventory contributes directly to the overall effectiveness of Information Security Management (ISM).
In brief, the Asset Inventory is the foundation on which successful Information Security Management is constructed. It offers a methodical way to recognise, classify, and safeguard assets, establishing the basis for all future security actions. Organisations would find it difficult to protect their information if they do not have a thorough and regularly updated Asset Inventory. Therefore, the Asset Inventory serves as more than just a tool; it is an essential element of a strong and resilient security plan for any organisation following ISO 27001 guidelines.
Unlock the Secrets to ISO 27001 Success with our ISO 27001 Foundation Course – Register now!
Steps to Create an Asset Inventory for ISO 27001
Let's dive deeper into the steps involved in creating an Asset Inventory for ISO 27001, focusing on the specific actions and considerations at each stage:
Step 1: Identify all Assets
To build a robust Asset Inventory for ISO 27001 compliance, start by conducting a comprehensive assessment. Form a cross-functional team involving IT, operations, finance, legal, and other relevant departments to ensure all Assets are accounted for. Interviews with key personnel are vital, including IT staff, department heads, and end-users who utilise Assets. Review existing records, contracts, and documentation like invoices and procurement records.
Additionally, perform physical inspections to identify hardware Assets not documented elsewhere. Leverage Asset Management software and tools to scan and recognise digital Assets such as software, databases, and configurations. This holistic approach ensures no Asset is overlooked.
Step 2: Classify Assets
Once you've compiled a comprehensive list of Assets, the next step is classification. ISO 27001 suggests categorising Assets into types such as hardware, software, data, personnel, and facilities. Each Asset should be designated with a unique identifier to facilitate tracking and management. This classification is instrumental in prioritising Assets for security measures and resource allocation.
By distinguishing between hardware, software, data, and other Asset types, organisations can tailor their security measures to address the specific vulnerabilities and threats associated with each category. This step lays the foundation for effective Asset Management and protection.
Step 3: Determine Ownership and Responsibility
Assigning ownership and responsibility is pivotal to establishing accountability for Asset security and maintenance. Clearly identify individuals or departments responsible for owning each Asset. Ownership implies the authority to make decisions regarding the Asset. Beyond ownership, define specific roles and responsibilities associated with each Asset.
IT staff may be responsible for maintenance, while security teams oversee data protection. End-users may have responsibilities related to adhering to security policies. This step ensures that everyone involved in Asset Management understands their role, fostering a culture of responsibility and accountability. Effective Asset ownership and responsibility enhance the security posture of the organisation.
Boost your organisation's cybersecurity with your choice from our extensive ISO 27001 Courses - sign up now!
Step 4: Assess Asset Value
Assessing the value of Assets to the organisation is vital for prioritisation and resource allocation. Asset value encompasses financial, reputational, legal, and operational dimensions. Financially, calculate the Asset's cost, replacement value, and potential repair expenses. Consider how the loss of an Asset could impact the organisation's reputation and brand.
Evaluate whether Assets are subject to legal requirements or industry regulations, as non-compliance may result in fines and legal issues. Additionally, gauge the operational importance of Assets. Some Assets are critical for business continuity, making them top priorities for protection. Understanding Asset value guides effective decision-making in security measures and risk management.
Step 5: Document Asset Details
Creating detailed records for each Asset is essential for comprehensive Asset Management. Documentation should be accurate, up-to-date, and easily accessible to relevant stakeholders. Each Asset should have a unique identifier, such as a serial number or Asset tag. Descriptions should be detailed, encompassing make, model, configuration, and specifications.
Physical location must be documented to facilitate Asset tracking. Version or configuration details are crucial, especially for software and hardware. Note down the security controls in place for each Asset, including access controls, encryption, and monitoring. This comprehensive documentation ensures that all stakeholders have access to the essential information required for Asset Management and protection.
Step 6: Establish Protection Measures
These measures should align with the organisation's overarching security policy. They may encompass various aspects of security, including access controls, encryption, regular backups, security patching, and monitoring systems.
Tailor security measures to the unique attributes and importance of each Asset. Critical Assets may require more robust protection, while less critical ones may need lighter controls. The goal is to create a layered security approach that adequately safeguards Assets against potential threats and vulnerabilities. Adequate protection measures are crucial for maintaining the confidentiality, integrity, and availability of Assets.
Step 7: Regularly review and update
An Asset Inventory is a document that requires continuous attention and maintenance. It should undergo regular reviews and updates to remain accurate and effective. Document any changes or additions to Assets as they occur. This could include acquiring new Assets, decommissioning old ones, or modifying existing configurations.
Conduct periodic assessments of Asset value and the effectiveness of security controls to ensure they remain accurate and appropriate. Regular security testing, like vulnerability assessments and penetration testing, helps identify and mitigate vulnerabilities promptly. These ongoing efforts ensure that the Asset Inventory remains a valuable tool in protecting the organisation's Assets and maintaining information security compliance.
Conclusion
In conclusion, developing an Asset Inventory for ISO 27001 is more than a compliance requirement; it is a vital step in protecting your organisation’s most valuable assets. By meticulously identifying, classifying, and valuing these assets, your organisation can implement robust security measures, effectively mitigating potential threats and vulnerabilities. This proactive strategy ensures your organisation remains resilient and well-protected in an increasingly complex security landscape.
Elevate your cybersecurity skills with our ISO 27001 Lead Auditor Course – Join now!
Frequently Asked Questions

Creating an Asset Inventory is vital for ISO 27001 Compliance. It helps identify, classify, and secure information assets, ensuring effective risk management. This inventory forms the foundation for implementing security controls and maintaining a robust Information Security Management System (ISMS).

To create an effective Asset Inventory for ISO 27001, follow these best practices:
a) Clearly define asset categories
b) Regularly update the inventory
c) Involve relevant stakeholders
d) Use automated tracking tools
e) Link all assets to specific security controls

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various ISO 27001 Training, including the ISO 27001 Foundation Course, ISO 27001 Lead Auditor Course, and ISO 27001 Internal Auditor. These courses cater to different skill levels, providing comprehensive insights into the Benefits of Compliance.
Our ISO & Compliance Blogs cover a range of topics related to ISO, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your ISO & Compliance skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 ISO 27001 Foundation
ISO 27001 Foundation
Mon 6th Jan 2025
Mon 10th Feb 2025
Mon 17th Mar 2025
Mon 7th Apr 2025
Mon 12th May 2025
Mon 23rd Jun 2025
Mon 7th Jul 2025
Mon 18th Aug 2025
Mon 1st Sep 2025
Mon 13th Oct 2025
Mon 10th Nov 2025
Mon 1st Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


