We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203 999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Picture this: your organisation is facing a surge of cyber threats, and your security team is overwhelmed. Given this scenario, you must stay ahead of the evolving dangers, but how can you do that? The answer lies in utilising the right Threat Intelligence Tools. These tools are structured to provide actionable insights, helping you figure out and mitigate potential threats before they cause significant damage.
But with so many options available, which ones should you choose? In this blog, we will explore the 12 Best Threat Intelligence Tools that can transform your security strategy. Let’s dive in and find out which tools are best suited for your needs.
Table of Contents
1) What are Threat Intelligence Tools?
2) Importance of Threat Intelligence Tools
3) 12 Best Threat Intelligence Tools
4) Best Practices for Implementing Threat Intelligence Tools
5) Conclusion
What are Threat Intelligence Tools?
Threat Intelligence Tools encompass modelling frameworks, intelligence feeds, databases, utilities, and software platforms utilised by Cyber Security experts to collect, develop, share, and analyse Threat Intelligence.
Some Threat Intelligence Tools, such as modelling frameworks, specialised databases, and certain intelligence feeds, are available at no cost. However, enterprise organisations typically provide software solutions and access to comprehensive threat data lakes on a subscription basis.
Importance of Threat Intelligence Tools
Implementing Threat Intelligence Tools is crucial for maintaining a robust security posture. Here are some key points determining their significance:
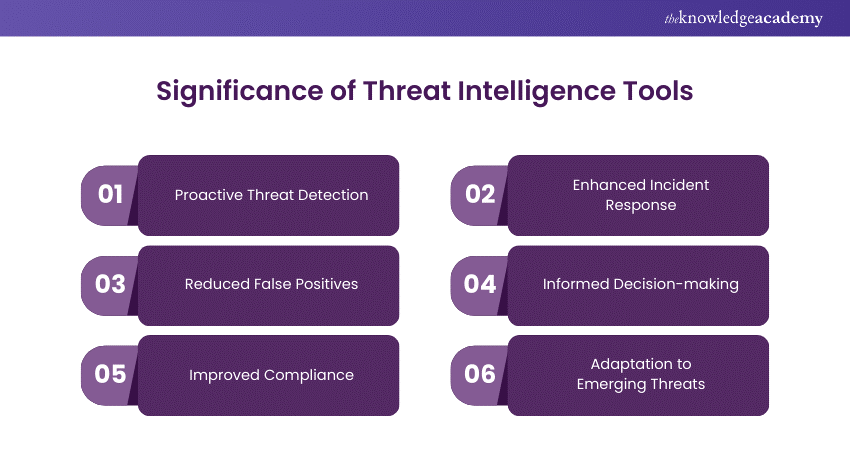
a) These tools help identify potential threats before they can exploit vulnerabilities, allowing for proactive measures.
b) By providing contextual data and prioritising alerts, Threat Intelligence Tools enable faster and more effective incident response.
c) They help filter out false positives and ensure that security teams focus on genuine threats.
d) Threat intelligence provides valuable insights that guide strategic decisions regarding security investments and policies.
e) Utilising Threat Intelligence can help organisations meet regulatory requirements and industry standards.
f) These tools keep security teams updated on the latest threat trends and tactics, ensuring they are prepared for new and evolving threats.
12 Best Threat Intelligence Tools
Choosing the proper Threat Intelligence Tools is critical for boosting your organisation’s safety posture. These tools assist in perceiving, analysing, and mitigating ability threats earlier than they cause big harm. Here are some of those essential tools:
1) ThreatConnect
ThreatConnect is a prominent provider of Threat Intelligence services. The company offers numerous tools and services, including a Threat Intelligence platform, an incident response platform, and a Malware Analysis tool. Additionally, ThreatConnect provides numerous resources for security professionals, such as training materials and a blog.
Earn internationally recognised qualifications with our EC-Council Certifications – register now!
2) BitDefender
BitDefender is a global provider of security solutions for agencies and people. The company gives various services and products, such as antivirus software, internet protection, Malware removal, and risk modelling tools. BitDefender also provides several Threat Intelligence offerings, such as a real-time global threat map and an internet risk scanner.
3) CrowdStrike
This tool offers organisations immediate visibility into all activities on their network. It assists them in identifying and responding to threats swiftly and effectively. By providing real-time insights, it enables proactive threat management. Furthermore, it enhances overall network security by ensuring continuous monitoring and rapid incident response.
4) Recorded Future Fusion
This tool gives users instant access to the latest Threat Intelligence globally. It aids firms in making more informed choices about their safety through handing over real-time records at the most recent threats. Providing up-to-date information complements the ability to expect and counteract rising risks. Furthermore, it supports a proactive protection approach, ensuring continuous vigilance towards ability threats.
5) SolarWinds
This tool provides a comprehensive view of an organisation’s security posture. It enables users to identify all potential threats and take appropriate measures to mitigate them. Offering detailed insights supports proactive risk management. Additionally, it enhances overall security by ensuring continuous monitoring and timely threat response.
6) OpenPhish
OpenPhish feeds deliver phishing intelligence, offering information about ongoing phishing attacks, including the targeted brand, phishing URL, and time. Its Global Phishing Activity page provides real-time insights with data on live phishing pages observed by the service.
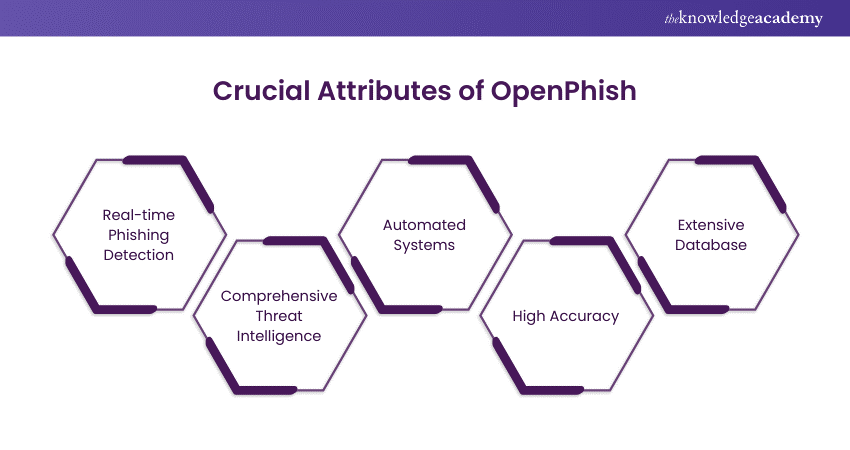
Updated every five minutes with data from the previous twenty-four hours, the page offers insights into the top 10 targeted brands, top 10 sectors, and top 10 ASNs.
7) ClamAV
This open-source antivirus engine is designed to detect trojans, viruses, malware, and other malicious threats. While it can be utilised in various ways, it is commonly employed for email and web scanning or endpoint security.
ClamAV updates its signature database multiple times daily, providing built-in support for standard mail file formats, various archive formats, Executable and Linkable Format (ELF) executables, Portable Executable files, and other popular document formats such as MS Office and Portable Document Format (PDF). The project distributes a collection of signatures in its ClamAV Virus Database (CVD) file format, which is maintained by Cisco Talos.
8) DataGuidance
Owned by OneTrust, DataGuidance offers information on global privacy laws. The news section provides updates on case law, legislation, official decisions, and guidelines. Daily updates cover various topics, including the status of new laws at state and federal levels, agency actions against companies, and announcements on regulatory agency draft rules.
9) ImmuniWeb
ImmuniWeb, an application security company, provides a free tool for organisations to monitor and measure their dark web exposure. With this tool, you can scan a URL, monitor up to three domains, integrate the free command line toolkit into your Continuous Integration/Continuous Delivery (CI/CD) pipelines and DevOps, and use the free Application Programming (API) to conduct up to four dark web exposure tests per day.
10) Google
Users with a Google One account can establish monitoring profiles to scan the dark web for their personal information. The dark web monitoring reports can scan for various details, including one name, one address, ten phone numbers, ten emails, and one social security number. These reports inform you of the number of data breaches for each category, the names of the data breaches, and the dates they occurred.
Develop the essential skills to safeguard cloud environments – join our Certified Cloud Security Engineer Certification today!
11) MISP Threat Sharing
Previously known as the Malware Information Sharing Platform, MISP is an open-source threat-sharing platform that allows you to correlate Indicators of Compromise (IoC) in its database with attributes and indicators from malware, attacks, or campaigns. The default configuration includes 63 distinct feeds with minimal overlap between them.
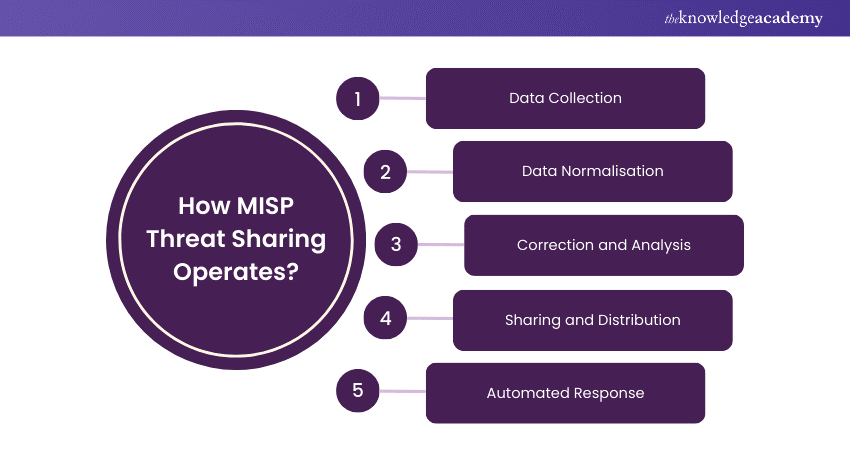
By recognising that Threat Intelligence encompasses more than just IoCs, MISP employs open protocols and data formats, enabling integration with other tools while also offering metadata tagging, feeds, and visualisations.
12) BlockList.de
BlockList.de reports over 70,000 attacks every twelve hours, allowing you to search for known malicious IP addresses. Operated by volunteers, the service aims to report all attacks to fraud and abuse departments, enabling providers to inform their customers about infections and potentially disable the attacker. To facilitate automatic parsing of reports, BlockList.de uses the open standard X-ray Fluorescence Software (XARF) for data sharing.
Best Practices for Implementing Threat Intelligence Tools
Implementing Threat Intelligence Tools effectively is essential for maximising their benefits and enhancing your organisation’s security posture. By following best practices, you can ensure that these tools are integrated seamlessly into your existing security infrastructure, providing timely and actionable insights. Here are some best practices for implementing these tools:
1) Seamless Integration with Existing Security Tools
Threat intelligence, while not particularly effective on its own, becomes highly valuable when integrated with other security technologies. Incorporate Threat Intelligence into automated security systems to enhance their ability to detect suspicious events and behavioural patterns.
Threat intelligence is often integrated with Security Information and Event Management (SIEM) systems, facilitating proactive alerting, prioritisation, and providing contextual data for alerts to simplify investigations. Numerous other security systems can also benefit from Threat Intelligence data, including endpoint security solutions, Next-Generation Firewalls (NGFW), and Web Application Firewalls (WAF).
2) Enhance Alert Accuracy
Alert fatigue is a common issue among security teams. It happens when security teams cannot review and respond to all the alerts they receive because of the overwhelming volume or low quality of alerts. When a significant number of alerts are false positives or demand extensive investigation to decipher, security analysts often end up disregarding them.
Threat intelligence aids in categorising and prioritising alerts and eliminating false positives by correlating alert data with Threat Intelligence feeds and databases. This ensures that higher-priority issues are addressed first, mitigating alert fatigue and ensuring that security teams never miss important notifications.
3) Proactive Use of Intelligence
Threat intelligence should serve as a guide to identify vulnerabilities and threats before an attack occurs. You can utilise Threat Intelligence data to inform the deployment of security tools that address significant threat vectors, restrict permissions or access controls to prevent known attacks and identify patches or updates needed for vulnerable systems.
Threat intelligence aids in classifying risky activities and incidents, guiding early detection and more effective responses. Integrating it into automated response processes is especially advantageous, as it aids in forecasting attack patterns and recommending the most effective countermeasures. Automated response is another approach to ensure early detection and swift reaction to attacks.
Conclusion
Incorporating the right Threat Intelligence Tools into your security method is obligatory for staying ahead of cyber threats. Such tools boost your capability to hit upon and reply to ability attacks. By leveraging these top 12 tools, you can guarantee a strong defence against the ever-evolving landscape of cyber threats.
Advance your career by signing up for our Certified SOC Analyst Certification today!
Frequently Asked Questions

Targeted Threat Intelligence is the process of gathering and analysing specific information related to cyber threats aimed at an organisation or sector. It provides actionable insights into potential risks, enabling tailored defensive measures against particular attacks.

Yes, Threat Intelligence is a valuable skill. It involves understanding, collecting, and analysing data to anticipate and respond to emerging cyber threats.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various EC- Council Certifications, including the Certified Ethical Hacker Certification, Certified DevSecOps Engineer Certification, and Certified Threat Intelligence Analyst Certification. These courses cater to different skill levels, providing comprehensive insights into Types of Computer Viruses.
Our IT Security & Data Protection Blogs cover a range of topics related to Cyber Threats and Security, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Information Technology (IT) and Data Protection skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Threat Intelligence Analyst Certification
Certified Threat Intelligence Analyst Certification
Mon 27th Jan 2025
Mon 24th Feb 2025
Mon 17th Mar 2025
Mon 26th May 2025
Mon 23rd Jun 2025
Mon 28th Jul 2025
Mon 18th Aug 2025
Mon 22nd Sep 2025
Mon 20th Oct 2025
Mon 17th Nov 2025
Mon 15th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


