We may not have the course you’re looking for. If you enquire or give us a call on 01344 203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

In today's cybersecurity world, organisations must remain alert against advanced threat tactics as cyberattacks have evolved to become increasingly sophisticated and clandestine. The term 'Advanced Persistent Threat' characterises a sequence of methodical cyber assaults that occur over an extended period. In this blog, we will discuss an Advanced Persistent Threat, a cyberattack where an unauthorised user gains access to a network.
Table of Contents
1) What is an Advanced Persistent Threat?
2) Key characteristics of an APT attack
3) Stages of an Advanced Persistent Threat
4) APT security measures
5) Types of Advanced Persistent Threats
6) Real-world examples
7) Conclusion
What is an Advanced Persistent Threat?
An Advanced Persistent Threat (APT) is a comprehensive term that describes a refined and prolonged cyberattack. Here, intruders, or sometimes organised teams of intruders, establish a covert and long-term presence within a network with the intention of accessing highly sensitive data. These planned attacks typically target large enterprises or government networks and can result in severe consequences, including:
1) Theft of intellectual property, such as trade secrets or patents.
2) Compromise of sensitive information, including employee and user private data.
3) Sabotaging critical organisational infrastructures, such as deleting databases.
4) Complete takeover of websites.
Executing an APT attack demands considerably more resources than a typical web application attack. Perpetrators are often well-funded and consist of experienced cybercriminals, sometimes even backed by government entities for cyber warfare purposes.
Enhance your organisation's cyber resilience with our comprehensive Cyber Security Awareness Training – stay ahead of evolving threats!
Key characteristics of an APT attack
Advanced Persistent Threat (APT) cyber security attacks exhibit several distinct characteristics that set them apart from other forms of cyberattacks:
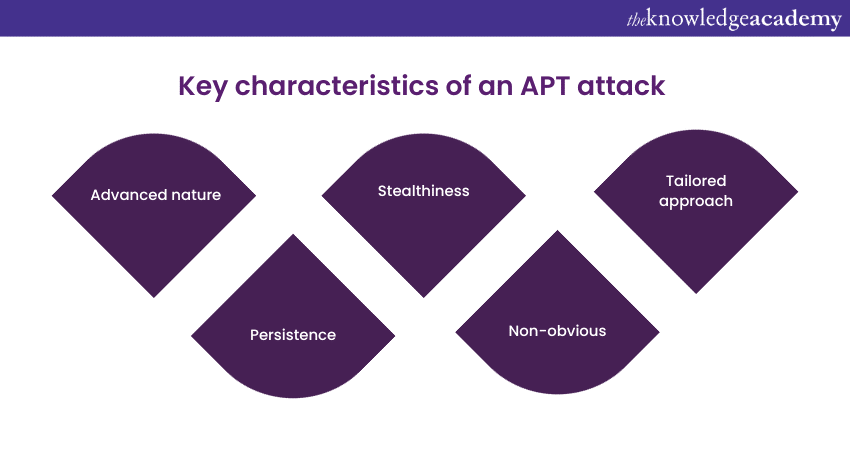
1) Advanced nature: Customising APTs can be expensive, with costs ranging from thousands to millions of dollars. These attacks are typically orchestrated by highly skilled and intelligent cybercriminals who invest significant time and resources in their development.
2) Persistence: APT attackers often exhibit a lower risk tolerance compared to more indiscriminate hackers. Their primary goal is to remain undetected for as long as possible, necessitating careful planning and the exploitation of the target's vulnerabilities.
3) Stealthiness: APT attacks are known for their highly sophisticated social engineering techniques, making them difficult to detect and prevent. Once they gain access, APTs maintain a persistent presence, carrying out their activities covertly.
4) Non-obvious: In addition to the tools mentioned, APTs employ a wide array of potential tools, including powerful Trojan viruses. These tools are carefully chosen to ensure that the attacker's presence remains concealed.
5) Tailored approach: APT attacks are far from the work of semi-technical script kiddies. They are highly targeted, taking into account the specific vulnerabilities of the organisation. Developing zero-day malware attacks falling within the APT category can be very costly work.
6) Specific purpose: APTs enable criminals to gather sensitive information over an extended period, maximising their gains. These objectives can be political, strategic, or espionage-related, with APTs persistently pursuing these goals.
7) Multiple entry points: APTs may launch multiple attempts to establish an initial presence in a network. These attempts are generally well-researched to succeed, with extensive research conducted to identify vulnerabilities within the organisation. It also includes human gatekeepers and network weaknesses.
8) Multiple stages: APTs are characterised by their multiphase nature, involving stages such as social engineering, phishing, and exploit kits. This process includes mapping the organisation's network, developing a precise approach, capturing data, and repeated exfiltration.
9) Distinct signs of detection: Although APTs are notoriously challenging to detect, organisations may observe signs following a compromise. These signs may include unusual activity on user accounts, the use of backdoor trojans for access, sudden increases in database operations, and data exfiltration techniques.
10) Knowledge sources: APT attacks are a concern for businesses of all sizes. Small and medium enterprises should not underestimate the threat, as APT attackers increasingly target smaller companies within the supply chain to gain access to larger organisations.
Stages of an Advanced Persistent Threat
An Advanced Persistent Threat (APT) attack is a carefully directed process that can be divided into three main stages. These stages are carried out with the primary objective of remaining undetected while infiltrating a network, expanding the attacker's presence, and extracting valuable data.
Stage 1 – Infiltration
At the initial stage of an APT attack, the attacker gains access to the targeted enterprise. This access is typically achieved through the compromise of one of three attack surfaces: web assets, network resources, or authorised human users. The methods used can involve antagonistic uploads, such as Remote File Inclusion (RFI) or SQL injection, or social engineering attacks like spear phishing. These are threats that large organisations routinely face.
Infiltrators may also use distraction tactics, such as Distributed Denial of Service (DDoS) attacks, simultaneously. DDoS attacks serve a dual purpose – they divert the attention of network personnel and weaken the security perimeter, making it easier for the attacker to breach.
Once initial access is secured, attackers install a backdoor shell, a form of malware that grants them access to the network and enables remote, stealthy operations. These backdoors can sometimes take the form of Trojans disguised as legitimate software.
Stage 2 – Expansion
With a foothold established, attackers proceed to expand their presence within the network. This involves moving up the organisational hierarchy and compromising staff members who have access to the most sensitive data. By doing so, they can access critical business information, including product line details, employee data, and financial records.
The collected data serves various purposes depending on the attacker's ultimate goal. It can be sold to a competitor, manipulated to sabotage a company's product line, or used to disrupt an entire organisation. In cases of sabotage, this phase is used to subtly gain control of critical functions and manipulate them in a specific sequence to maximise damage. For example, attackers might delete entire databases and disrupt network communications to prolong the recovery process.
Stage 3 – Extraction
During an ongoing APT attack, stolen information is typically stored in a secure location within the targeted network. When the attackers have gathered enough data, they need to extract it without raising suspicion.
To achieve this, they often employ diversionary tactics to distract the security team, enabling the information to be moved out without detection. This diversion can manifest as a DDoS attack once again, which ties up network personnel and weakens site defences, facilitating the extraction process.
Elevate your cybersecurity skills and protect your digital world with our leading Cyber Security Training – fortify your defence today!
APT security measures
Effective APT detection and protection necessitates a multi-faceted approach involving network administrators, security providers, and individual users.
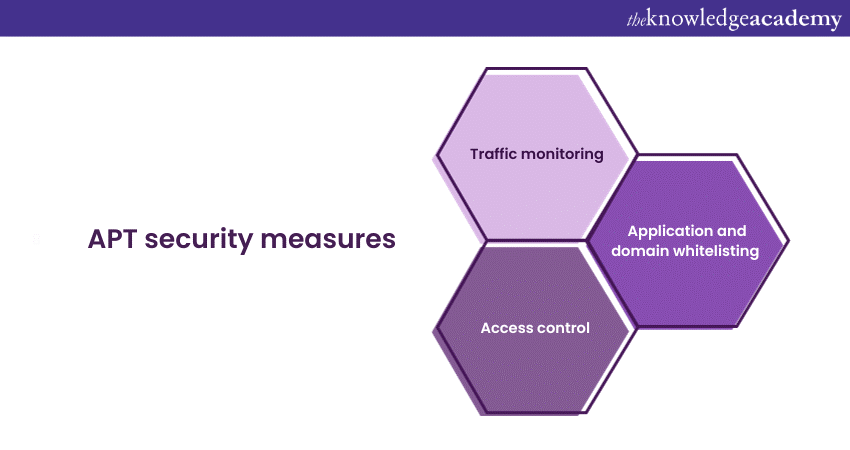
Traffic monitoring
One best practice to prevent the installation of backdoors and block data extraction is the continuous monitoring of ingress and egress traffic. This caution is essential to identifying and responding to any irregularities that may signal negative activity within your network. Implementing a web application firewall (WAF) at the network edge acts as a filter, safeguarding vulnerable attack surfaces and preventing application layer threats, including RFI and SQL injection attacks commonly utilised during APT infiltration phases.
Internal traffic monitoring services, like network firewalls, offer a fine view of user interactions within your network. They help in recognising internal traffic anomalies, such as unusual logins or large data transfers, which could be indicative of an APT attack. Monitoring access to file shares and system honeypots is another valuable practice. Additionally, incoming traffic monitoring services can be used to detect and remove backdoor shells by intercepting remote requests from operators.
Application and domain whitelisting
Whitelisting provides control over which domains are accessible from your network and which applications can be installed by users. This method reduces available attack surfaces, improving protection against APT attacks. While effective, whitelisting is not foolproof, as even trusted domains can be compromised, and negative files often masquerade as legitimate software. Enforcing strict update policies is crucial to ensure that users consistently run the latest versions of whitelisted applications.
Access control
Your employees are often the most vulnerable entry points within your security perimeter, making them prime targets for attackers seeking to infiltrate and expand their presence. These individuals typically fall into one of three categories: careless users who unintentionally grant access, harmful insiders who deliberately abuse their credentials, and compromised users whose privileges are exploited by attackers. Effective access control involves comprehensive reviews of all individuals in your organisation, especially concerning the information they can access. Implementing a need-to-know data classification system limits the potential for intruders to hijack low-level staff credentials for accessing sensitive materials.
Two-Factor authentication (2FA) should be implemented at key network access points to prevent unauthorised access and network traversal. 2FA typically requires a second form of verification, such as a passcode sent to the user's mobile device.
Additional measures
In addition to the practices, the following are essential best practices for securing your network:
1) Promptly patching network software and OS vulnerabilities.
2) Implementing encryption for remote connections to prevent intruders from exploiting them to infiltrate your network.
3) Filtering incoming emails to thwart spam and phishing attacks directed at your network.
4) Maintaining immediate event logging to enhance whitelists and other security policies.
Types of Advanced Persistent Threats
It's challenging to imagine a more concerning scenario than falling victim to a sophisticated Advanced Persistent Threat (APT). APT malware is a tool used for executing extended-duration APT attacks that operates differently from typical malware. Instead of causing immediate damage to a computer or network, APT malware specialises in secretly extracting data over an extended period. Here are some of the most common Advanced Persistent Threats seen in different Types of Attacks in Cyber Security:
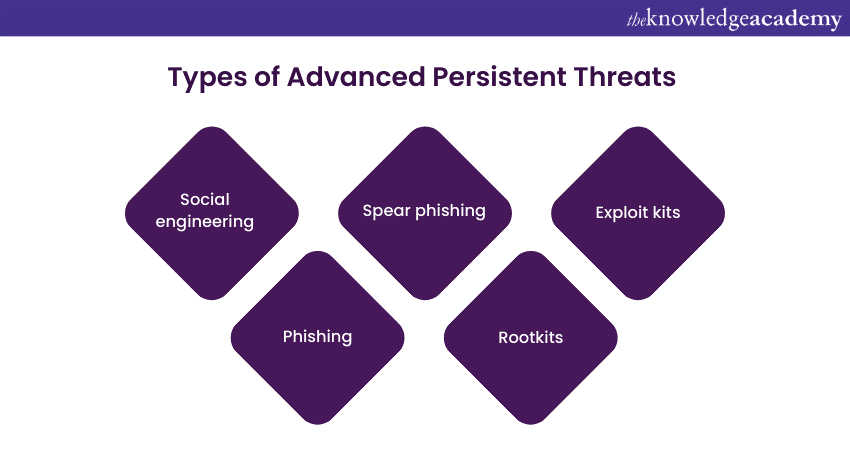
Social engineering
Unauthorised access to systems, networks, and physical locations can be achieved through the exploitation of social engineering techniques. Hackers adeptly hide their identities and intentions by assuming the guise of trusted individuals or sources of information. This method enables them to influence, manipulate, or deceive organisations into divulging sensitive information.
Phishing
APT phishing attacks involve deceptive websites that appear legitimate but are actually designed to steal sensitive data like credit card numbers, bank account information, or passwords. Typically, cybercriminals use a deceptive message containing a phishing website link, often masquerading as a reputable company, a friend, or an acquaintance.
Spear phishing
Spear phishing involves targeting specific individuals, companies, or organisations through email or electronic communications. While the primary goal may be data theft, cybercriminals sometimes use malware to compromise the targeted user's computer.
Rootkits
Malware like rootkits allows hackers to seize control of a targeted device. Some rootkits can infect both hardware and software components of a computer, compromising the operating system and software.
Exploit kits
Exploit kits target software vulnerabilities. When hackers discover outdated software with critical security vulnerabilities, they target such systems with malware to exploit their weaknesses. Commonly, malware payloads include shellcode, a small piece of malware that downloads additional malware from attacker-controlled networks. This approach allows for the infiltration and infection of organisations and devices.
Other techniques
A wide spectrum of additional APT attack methods exists, including computer worms, bots, spyware, adware, ransomware, remote execution, web shells, keyloggers, and many more.

Real-world examples
Here are some expanded real-world examples of Advanced Persistent Threats (APTs):
Stuxnet: A cyberweapon against Iran's nuclear program
Stuxnet is one of the most infamous APTs in history. It was designed to target Iran's nuclear facilities and disrupt their uranium enrichment program. Stuxnet specifically aimed to damage the centrifuges used for uranium enrichment by manipulating their control systems. The level of sophistication in Stuxnet was remarkable, as it not only compromised the facilities but also evaded detection for an extended period. This APT was believed to be a joint effort between nation-states and demonstrated the potential of APTs as cyberweapons in geopolitical conflicts.
Equifax data breach
In 2017, Equifax, one of the major credit reporting agencies in the United States, suffered a massive Data Breach due to an APT. The attackers exploited a vulnerability in Equifax's web application software to gain unauthorised access to sensitive personal and financial information of approximately 147 million individuals. This breach showcased the devastating impact APTs can have on both individuals and large organisations, leading to extensive financial and reputational damage.
Operation Aurora
Operation Aurora was a series of APTs targeting major technology and financial corporations in 2009. It was attributed to state-sponsored Chinese hackers. The attackers used spear-phishing emails to compromise employees' computers, eventually infiltrating corporate networks. This campaign highlighted the use of APTs for industrial espionage, with the attackers focusing on stealing intellectual property and source code from their targets.
APT28 (Fancy Bear): Alleged Russian state-sponsored APT
APT28, also known as Fancy Bear, is an APT group that has been attributed to the Russian government. It has been involved in various high-profile cyber espionage campaigns. A notable example is the likely interference in the 2016 United States presidential election. APT28 used sophisticated spear-phishing techniques to gain access to political organisations and leak sensitive information, underscoring the potential political and social impact of APTs.
APT29 (Cozy Bear): Another Russian state-linked APT
APT29, or Cozy Bear, is another Russian state-linked APT group. It gained notoriety for its involvement in the cyberattack on the Democratic National Committee (DNC) in 2016, a breach that stirred political controversy. Cozy Bear used spear-phishing emails to infiltrate the DNC's network, highlighting the persistence and precision with which APTs can target specific organisations for political purposes.
OceanBuffalo (APT30): Espionage in Southeast Asia
APT30, also known as OceanBuffalo, is an APT group believed to operate from China. It has been involved in a long-running cyber espionage campaign targeting Southeast Asian governments and organisations. This APT is an example of how APTs are used for intelligence gathering and surveillance to further political interests in the Asia-Pacific region.
Conclusion
Advanced Persistent Threat (APT) attacks present a grave danger to organisations, as they can lead to the compromise of vital information. To mitigate the risk of APT attacks, it's crucial to comprehend the tactics employed by cyber adversaries and their objectives within your network. The most effective strategy for thwarting APT attacks is to fortify your systems, making them impervious to unauthorised access.
Empower your organisation to navigate the digital landscape securely – explore our Cyber Security Risk Management Course and fortify your defences!
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 CISSP Certification
CISSP Certification
Mon 6th Jan 2025
Mon 24th Mar 2025
Mon 19th May 2025
Mon 14th Jul 2025
Mon 8th Sep 2025
Mon 17th Nov 2025







 Top Rated Course
Top Rated Course


 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


