We may not have the course you’re looking for. If you enquire or give us a call on +800 312616 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Internet Protocol Security (IPSec) is a crucial technology that safeguards sensitive information exchanged across IP networks. As organisations and individuals rely on the Internet for data exchange, there’s an increasing need for robust Security measures. Given this context, IPSec steps in as a versatile and powerful solution. Additionally, it provides a suite of Protocols and mechanisms to encrypt, authenticate, and ensure the integrity of data packets.
To delve deep into the world of IPSec, you can read this blog. By the end this blog, you can better understand the IPSec’s benefits, drawbacks, and practical applications in today's digital landscape.
Table of Contents
1) What is IPSec?
2) Components of IP Security
3) How does IPSec work?
4) Benefits of Internet Protocol Security
5) Drawbacks of Internet Protocol Security
6) Conclusion
What is IPSec?
Internet Protocol Security (IPSec) comprises a collection of Protocols designed to safeguard Internet Protocol (IP) communications. It establishes a structure for encrypting and validating data packets transmitted over IP networks. IPSec guarantees the confidentiality, integrity, and legitimacy of the transmitted information. Essentially, it facilitates secure communication among devices, even over potentially vulnerable networks like the Internet.
Components of IP Security
IPsec comprises a collection of Protocols designed to safeguard Internet Protocol (IP) communications. Being positioned within the network layer, IPsec facilitates secure communication among devices. A few of its components are discussed below:
1) Encapsulating Security Payload (ESP)
Encapsulating Security Payload (ESP) is one of the core Protocols within IPsec. It provides confidentiality, integrity, and optional authentication for data packets. ESP also secures the content of the IP packet by encrypting its payload, safeguarding the transmitted data from unauthorised interception. Additionally, ESP can provide authentication to ensure that the data has not been tampered with in transit.
2) Authentication Header (AH)
The Authentication Header (AH) is another important component of IPsec. AH ensures the integrity of data and authenticates IP packets. Unlike ESP, AH does not encrypt the actual data but instead provides a cryptographic checksum of the entire packet. It further ensures that the contents have not been altered in transit. AH is particularly useful in situations where encryption is not necessary, but data integrity is critical.
3) Internet Key Exchange (IKE)
Internet Key Exchange (IKE) is the Protocol used to establish Security Associations (SAs) in IPsec. SAs specifically define the parameters for secure communication, such as encryption algorithms, authentication methods, and key lifetimes. IKE performs two main phases of negotiation. Those include the phase 1 for setting up a secure channel. Their phase 2 helps in establishing actual IPsec SAs for data transmission.
Secure your future in cybersecurity with our Online Internet Security Specialist Training
How does IPSec work?
Understanding the inner workings of IPsec is essential to grasp its functionality and benefits. To know about how this works, you can go through the following points:
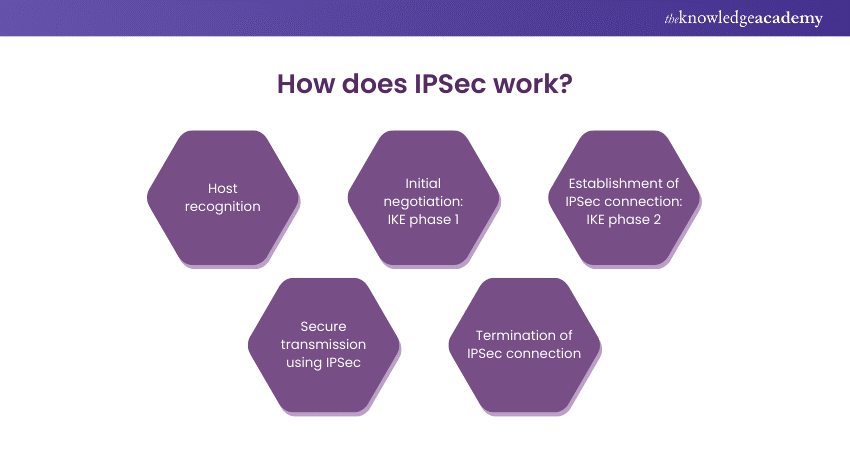
1) Host recognition
Before initiating any secure communication, IPsec-enabled devices must recognise each other. This recognition involves verifying the identity of the communicating hosts to ensure they are authorised to establish a secure connection.
2) Initial negotiation: IKE phase 1
The first phase of IKE involves negotiating a secure channel between the two devices. During this phase, they exchange encryption keys and establish a secure communication channel. This phase also ensures mutual authentication and sets the foundation for secure communication.
3) Establishment of IPSec connection: IKE phase 2
Once the secure channel is established, IKE phase 2 is initiated to negotiate the parameters of the IPsec SAs. This includes agreeing on encryption algorithms, integrity checks, and other Security parameters. Once completed, the devices have a secure tunnel through which they can transmit data.
4) Secure transmission using IPSec
With the IPsec SAs in place, data packets are encrypted and authenticated before being transmitted over the network. ESP or AH Protocols are used to protect the payload and ensure data integrity. They also provide a high level of Security for the transmitted information.
5) Termination of IPsec connection
When the secure communication is no longer needed, the IPsec connection can be terminated. This occurs either through manual intervention or automatically based on predefined criteria. Those criteria can include reaching a certain time limit or data threshold.
Transform your career with our Virtual Call Center Training – join us now!
Benefits of Internet Protocol Security
Internet Protocol Security (IPSec) stands as a crucial element in securing network communications and offers a multitude of benefits. Let's delve into those advantages:
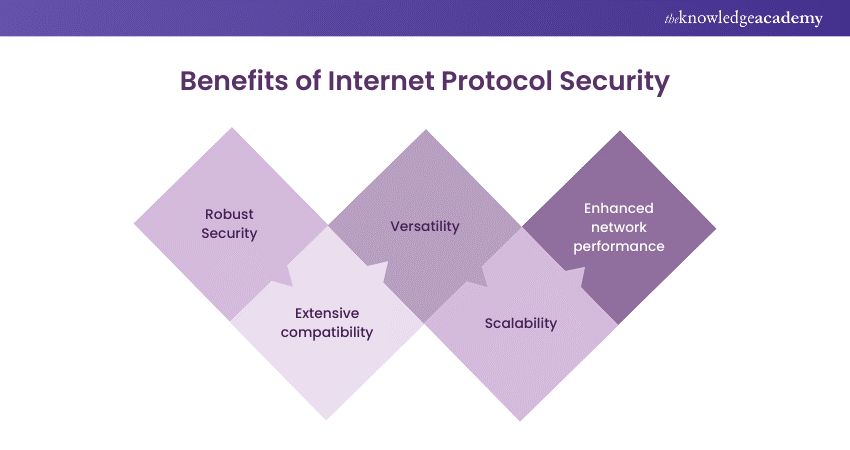
1) Robust Security
IPSec boasts robust Security features, which are one of its primary benefits. By encrypting data packets and providing authentication and integrity checks, it ensures that sensitive information remains secure during transmission. When data is sent over IP networks, IPsec works in the background to create a protective shield around it. This means that even if unauthorised users intercept the data packets, they would be unable to decipher the content. Additionally, authentication and integrity checks ensure that the data has not been tampered with during its journey across the network.
2) Extensive compatibility
A key advantage of IPsec is its wide support across various operating systems, devices, and network equipment. This extensive compatibility simplifies the implementation of IPsec in diverse environments without concerns about interoperability issues. Whether it's a Windows, macOS, Linux, or another operating system, IPsec can seamlessly integrate into the existing infrastructure. This compatibility extends to various network devices such as routers, and firewalls, making it a versatile choice for securing communications.
3) Versatility
IPsec offers multiple encryption and authentication options, giving users the freedom to choose the Security level as per their needs. This versatility is highly beneficial as different organisations and scenarios may require different Security configurations. For example, some may opt for Advanced Encryption Standard (AES) for encryption, while others may prefer RSA for authentication. IPsec's flexibility allows for customisation, ensuring that Security measures align closely with specific requirements.
4) Scalability
Whether it's a small office network or a large enterprise environment, IPsec scales effectively to accommodate different network sizes. This scalability also ensures that IPsec can be implemented across a few devices or an entire network infrastructure. Whether an organisation expands its network or undergoes changes in its size and structure, IPsec can adapt accordingly. Additionally, this scalability ensures that Security remains robust and consistent, regardless of the network's size or complexity.
5) Enhanced network performance
Contrary to common misconceptions, IPsec's impact on network performance is often minimal and can even improve performance in some cases. Efficient algorithms and hardware acceleration support contribute to this enhanced performance. IPsec ensures data integrity and reduces the risk of packet loss or retransmissions, thereby optimising network efficiency. It also prevents unnecessary retransmissions and ensures that data reaches its destination by securing the data at the packet level. This improvement in network performance is crucial for organisations that rely on efficient data transmission for their operations.
Drawbacks of Internet Protocol Security
Like any technology, IPSec also presents certain drawbacks that users should consider. To better understand those limitations, you can refer to the following points:
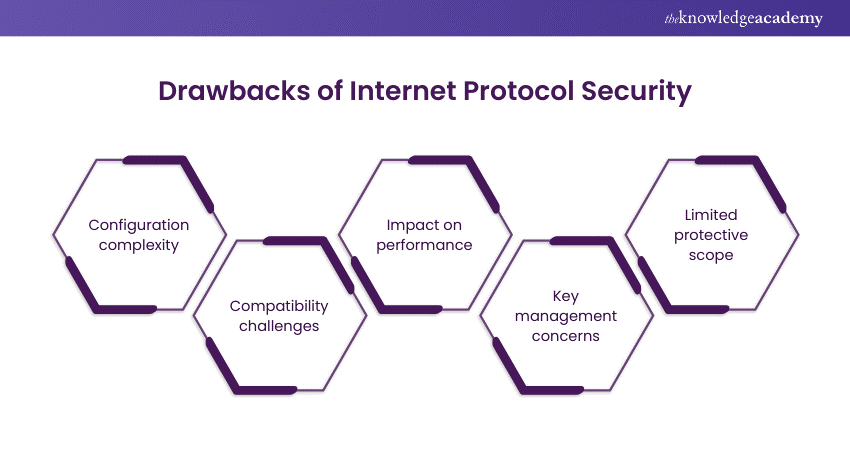
1) Configuration complexity
One significant drawback of IPsec is its configuration complexity. Setting up IPsec can be challenging, particularly for users who are not familiar with its intricate settings and parameters. Proper configuration involves decisions on encryption algorithms, key exchange methods, and various Security settings. Even small misconfigurations can lead to vulnerabilities or disruptions in secure communication.
2) Compatibility challenges
Despite its widespread support across different platforms and devices, IPsec may encounter compatibility challenges in heterogeneous network environments. Compatibility issues might arise while establishing secure connections between devices from different vendors or with varying implementations of IPsec. This can result in interoperability problems and require additional effort to ensure smooth communication across the network.
3) Impact on performance
While IPsec is designed to have minimal impact on network performance, there can be noticeable overhead due to encryption-decryption processes. In high-throughput environments where large volumes of data are transmitted, this overhead can become more pronounced. The encryption and decryption of data packets add processing overhead, which can lead to increased latency and reduced throughput. Organisations, thus, should consider the trade-off between enhanced Security and potential performance impact when implementing IPsec.
4) Key management concerns
Poor management practices can compromise the entire Security framework of IPsec. Therefore, organisations must implement robust key management practices to mitigate the risk of unauthorised access to sensitive data. They must establish policies for key generation, distribution, rotation, and revocation to ensure the integrity and confidentiality of encrypted communications.
5) Limited protective scope
While IPsec provides a strong Security for data transmission, it does not protect against all types of cyber threats. For instance, IPsec primarily focuses on securing the data during transmission and does not defend against attacks running on devices. Attacks such as malware infections, phishing, or social engineering can still compromise the Security of devices and networks. Therefore, organisations should complement IPsec with other Security measures to create a comprehensive Security posture.
Conclusion
In conclusion, Internet Protocol Security (IPSec) is a critical technology for securing IP communications. Essentially, IPsec ensures that data transmitted over IP networks remains confidential and secure. By understanding the aspects of IPSec, organisations and individuals can effectively secure their network communications.
Learn the latest social media strategies with our Virtual Social Media Manager Training
Frequently Asked Questions

IPsec is beneficial for both large enterprises and small businesses alike. It offers scalable Security solutions, ensuring data confidentiality and integrity for networks of all sizes and complexities.

No, IPsec can be implemented without specialised hardware. It operates at the network layer and is supported by most modern operating systems and network devices. Mostly, it is accessible for a wide range of setups.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Virtual Online Job Roles Training, including the Virtual Assistant Course, Online Internet Security Specialist Training, and Virtual Salesperson Training. These courses cater to different skill levels, providing comprehensive insights into How to Become an Online Teacher.
Our Business Skills Blogs cover a range of topics related to Internet Protocol Security, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Business skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming Business Skills Resources Batches & Dates
Date
 Online Internet Security Specialist Training
Online Internet Security Specialist Training
Fri 6th Dec 2024
Fri 14th Feb 2025
Fri 11th Apr 2025
Fri 13th Jun 2025
Fri 15th Aug 2025
Fri 10th Oct 2025
Fri 12th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


