We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203 999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
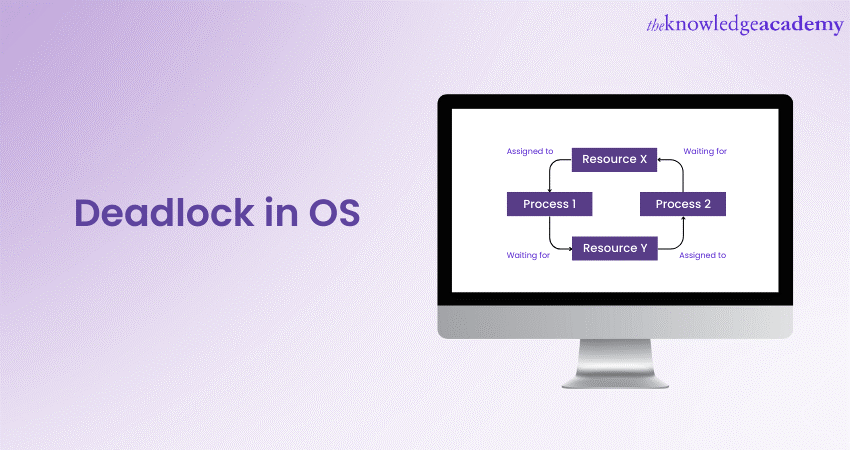
In any system, every process needs to utilise resources to be implemented. These resources could take the form of plugged-in devices like standard input and output devices or a system's CPU. Once the process is finished , the resource being used is released. However, when multiple processes occur simultaneously, they may compete for resources, leading to a Deadlock in the Operating System (OS). Tech experts have identified this situation of Deadlock in OS as a common issue.
Deadlock in Operating System happens when two or more processes cannot complete their execution because each is waiting for a resource held by the other. In this blog, we will delve into what Deadlock is, with detailed examples to help you understand it better. We will also cover various methods for handling Deadlock.
Table of Contents
1) What is Deadlock in Operating System (OS)?
2) Necessary Conditions for Deadlock
3) Example of Deadlock in OS
4) What is Deadlock Detection?
5) Methods of Handling Deadlock
6) Benefits of Deadlock Method
7) Limitations of Deadlock Method
8) Differences between Deadlock and Starvation
9) Conclusion
What is Deadlock in Operating System (OS)?
Deadlock in OS refers to a situation where more than one or two processes or threads are not able to proceed because each is waiting for the other to release a resource. In other words, it’s a state where a group of processes become stuck in a way that they can’t make any progress. Deadlock usually occurs in systems where multiple processes compete for limited resources such as CPU time, memory or input or output devices.
Learn to build iOS applications and debug apps with our IOS App Development Training – Join now!
Necessary Conditions for Deadlock
There are four necessary conditions for a Deadlock to occur, often referred to as Deadlock conditions. Here are the following essential conditions for Deadlock:
1) Mutual Exclusion: In this condition, only one method must be non-shareable. This means that only one process can be used at a time. This condition ensures that a resource cannot be simultaneously accessed or modified by multiple processes.
2) Hold and Wait: The process must hold at least one resource while waiting to acquire additional resources. This condition can lead to a situation where processes hold some resources and wait indefinitely for others.
3) No Pre-emption: Resources cannot be pre-empted or forcibly taken away from a process. This means that a resource can only be released voluntarily by the process holding it. If a process is holding a resource and cannot complete its task due to waiting for another resource, it will not release its current resource, contributing to a potential Deadlock.
4) Circular Wait: There must be a circular chain of one or more processes, each of which is waiting for a resource held by another process in the chain. This circular waiting pattern means that no process in the cycle can make progress because another process blocks it.
Example of Deadlock in OS
Here's a simple example of a Deadlock involving two processes, Process A and Process B, competing for two resources, Resource X and Resource Y:
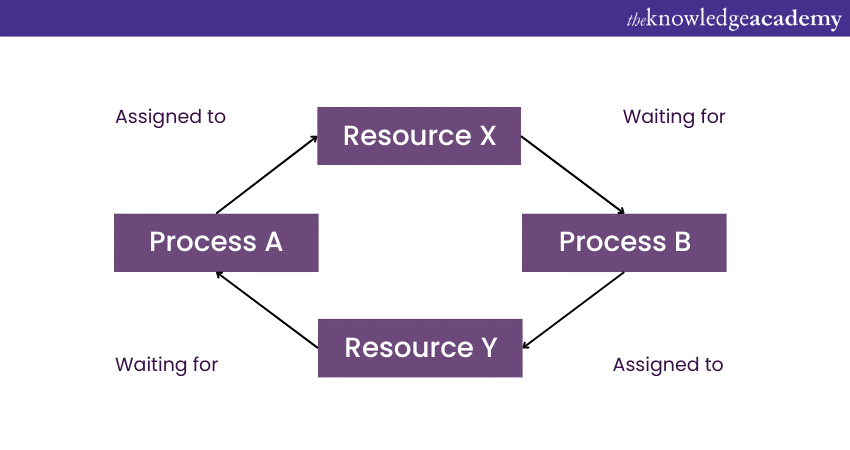
1) Initial Stage
1) Process A holds Resource X and requests Resource Y
2) Process B holds Resource Y and requests Resource X
2) Execution Sequence
1) Process A starts and acquires Resource X
2) Process B starts and acquires Resource Y
3) Stalemate
1) Process A requires Resource Y to complete its task, but it can’t proceed because Process B is holding it.
2) Process B requires Resource X to complete its task but can’t proceed because Process A is holding it.
Neither Process A nor Process B can release their held resource because they are still waiting for another resource to be released. This circular waiting condition fulfils one of the necessary conditions for Deadlock, leading to a Deadlock situation.
Get familiar with Android Architecture with our Android App Development Training now!
What is Deadlock Detection?
Identifying Deadlocks is essential for efficient resolution. Detecting Deadlock requires continuously checking the system's condition to identify any occurrence of Deadlock. Different algorithms, like the resource-allocation graph and the banker's algorithm, can assist in this procedure.
The system's resources and processes are visually depicted in the resource-allocation graph. It contains nodes representing processes and resources, connected by edges that show resource requests and allocations. By studying the diagram of loops, we can pinpoint possible Deadlocks.
The banker's algorithm functions as both a method for allocating resources and preventing Deadlocks. It evaluates system safety by running process simulations to ensure all processes can finish without getting stuck in a Deadlock. If it is not possible to reach a safe state, a Deadlock is established.
When a Deadlock is identified, steps can be implemented to solve it, allowing processes to continue running. Detecting Deadlocks is a crucial part of managing Deadlocks, providing important information about the system's status and helping to make well-informed choices for solving them.
Methods of Handling Deadlock
The following are the methods of handling Deadlocks.
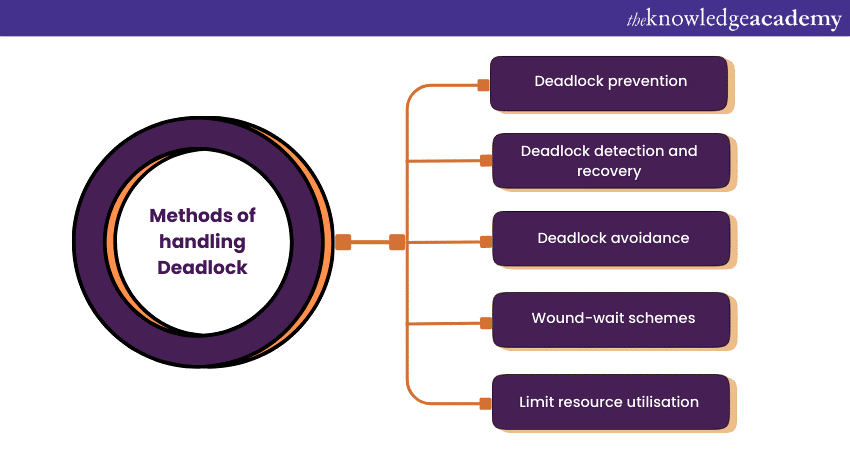
1) Deadlock Prevention: Deadlock prevention is focused on removing the chance of Deadlocks by making sure that one of the required conditions for Deadlock is always avoided. This can be done by managing resource distribution and enforcing protocols to prevent circular wait, hold and wait, and no preemption.
2) Deadlock Detection and Recovery: In this approach, the system regularly looks for Deadlocks. If a Deadlock is found, the system can resolve it by either ending or undoing one or multiple processes in order to eliminate the Deadlock loop and enable other processes to proceed.
3) Deadlock Avoidance: This method involves the system making real-time resource allocation decisions to maintain its safety. The banker's algorithm assesses resource requests and only approves them if they do not result in possible Deadlocks.
4) Wound-wait Schemes: Wound-wait schemes give preference to process execution according to their length of time waiting. If a younger process is holding a resource and an older process requests it, the younger process is interrupted to allow the older one to continue. This method reduces the risk of Deadlocks by making sure that older processes are not deprived.
5) Limit Resource Utilisation: By limiting the total resources a process can ask for, the system can decrease the chances of Deadlocks. This technique imposes more strict restrictions on resource allocation, reducing the likelihood of processes reaching a state where they could potentially hinder each other.
Benefits of Deadlock Method
The following are the benefits of the Deadlock method:
1) Proactive Approach: The Deadlock Method ensure that Deadlock cannot occur by eliminating one or more necessary conditions.
2) Resource Reclamation: The recovery method can potentially free up resources, allowing another process to continue execution. This can minimise the impact of Deadlock on system performance.
3) Risk Reduction: By restricting the maximum number of resources that can be allocated to the process, this method reduces the risk of Deadlock. It provides a very easy way to make sure that processes do not consume an excessive number of resources.
4) Resource Guarantees: It can provide resource guarantees to critical processes and ensure that certain resources remain available for essential tasks.
5) Detection and Resolution: Deadlock detection and recovery methods allow systems to detect and resolve Deadlocks when they do occur. This capability ensures that the system can continue functioning even in Deadlocks, improving system robustness.
Limitations of Deadlock Method
Here are some of the limitations of the Deadlock Method:
1) Complexity and Overhead: Many deadlock handling methods add complexity to the system. Implementing and maintaining these methods can be resource-intensive.
2) Process Interruption: Deadlock resolution methods such as process termination can hinder the process of the execution or transaction. This disruption can disrupt critical tasks and ultimately lead to inconsistency.
3) Complex Decision-Making: The Deadlock Handling Method involves complex decision-making to determine which process to abort or wait for. This decision makes the handling of Deadlock more intricate.
4) Performance Impact: The mechanisms used for Deadlock handling can introduce performance overhead. For example, frequent Deadlock deduction and recovery processes can affect the CPU cycle and system resources.
5) Increased Latency: In some cases, deadlock handling methods can introduce latency into system operations. This latency can impact real-time or time-sensitive applications where responsiveness is critical.
Unlock your web design potential: Join our Website Design Course today!
Differences Between Deadlock and Starvation
There is often confusion between deadlocks and starvation in Operating Systems. However, these two concepts are actually quite different. Deadlocks occur when two or more processes are blocked, waiting for each other to release resources. In contrast, starvation occurs when a process is unable to access resources due to competition from other processes.
|
Basis |
Deadlock |
Starvation |
|
Definition |
A situation where two or more processes are blocked, each waiting for resources held by the other | A process is unable to access the resources it needs, despite continuous attempts |
|
Cause |
Conflicts over resource allocation and synchronisation |
Resource allocation policies or scheduling algorithms favoring certain processes |
|
Resolution |
Resolved through methods like process termination, resource preemption, or rollback and re-execution | Addressed by improving scheduling algorithms or resource allocation policies |
|
Ways to Handle |
Handled by addressing any of the four deadlock conditions | Handled through aging techniques to ensure all processes receive fair resource access over time |
|
Other Names |
Handled by addressing any of the four deadlock conditions | Also referred to as a lived lock |
Conclusion
This is all about Deadlock in the Operating System. In this blog, we have discussed what Deadlock in OS is, examples to understand Deadlock more clearly, methods of handling Deadlock, benefits and limitations of the Deadlock Method and the difference between Deadlock and Starvation in OS.
Interested in Web Development? Check out our App & Web Development Training now!
Frequently Asked Questions

The Deadlock is managed by the Operating System using approaches such as prevention, detection, recovery, or avoidance. It makes sure resources are used efficiently, addressing Deadlocks by methods like ending processes or taking back resources when needed.

Yes, Deadlock can occur in multi-threaded applications when multiple threads compete for limited resources. If they hold resources while waiting for others, a circular wait condition may arise, resulting in a Deadlock scenario that halts execution.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various App & Web Development Training, including the Web Development Training, Mobile App Development Course, and Website Design Course. These courses cater to different skill levels, providing comprehensive insights into What is Operating System.
Our Programming & DevOps Blogs cover a range of topics related to Operating Systems, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Programming & DevOps skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming Programming & DevOps Resources Batches & Dates
Date
 Introduction to HTML
Introduction to HTML
Fri 17th Jan 2025
Fri 7th Mar 2025
Fri 23rd May 2025
Fri 12th Sep 2025
Fri 14th Nov 2025
Fri 12th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


