We may not have the course you’re looking for. If you enquire or give us a call on +91-181-5047001 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
In a world full of technology, there are some companies who don’t keep their Security Plans updated and develop their security policies. This is the main cause of data breaches at an average cost of 4.88 million in 2024 and 88% of these breaches are caused due to human error. It almost takes 194 days to identify a breach. So, to identify and get rid of these companies, they should implement SSP in their Security policies.
Table of Contents
1) What is a System Security Plan?
2) The Purpose of a System Security Plan
3) Key Components of an SSP for CMMC
4) How to Create a System Security Plan?
5) Standards and Best Practices for SSPs
6) Conclusion
What is a System Security Plan?
A System Security Plan (SSP) is a legal document that provides an overview of all the security controls, requirements and measures implemented within an information system. It’s a key requirement of any organisation for strengthening their cyber security. It includes all the system details like system boundaries, components, network diagrams, physical and logical access controls and all the incident response procedures.
The system description, control implementation, and system controls are the three main parts of the System Security Plan. The system description mainly highlights the system’s function, purpose and layout and also provides the system’s architecture, interconnectivity and interfaces.
System Security Plan helps the organisation in identifying the security risks to their information systems and business operations. By just having a SSP in the business it provides a comprehensive risk management framework.
The Purpose of a System Security Plan
A System Security Plan outlines the policies, procedures, and controls in place to protect an information system and ensure its security. The purpose of an SSP is to provide a comprehensive overview of the system's security posture, detailing how sensitive information is managed, protected, and accessed.
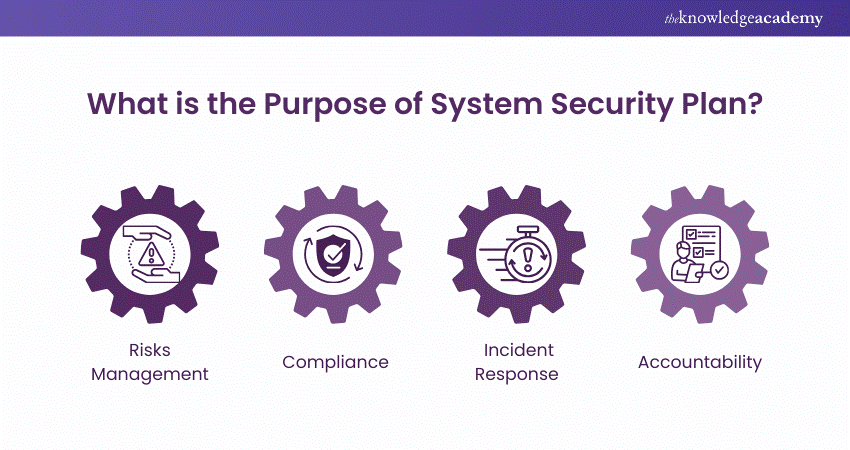
It serves as a blueprint for securing the system, identifying potential risks, and implementing measures to mitigate them. An SSP is crucial for ensuring compliance with security standards and demonstrating a commitment to safeguarding data, which is essential for both internal accountability and external regulatory requirements.
Key Components of an SSP for CMMC
The main key components of a System Security Plan for cyber security Maturity Model Certification (CMMC) are:
1) Security Requirement: It gives an outline of all the security requirements for the information Security System.
2) Risk Management: Deploying risk management teams and highlighting the strategies in the plan of System security.
3) Controls: The controls that are in place or planned to implement or defend the attacks to secure the information Systems. It also controls vulnerability and patch management.
4) Incident Response: In this the measures are outlined that should be taken during the data breach and the report that will be made in the response.
5) System Owner and System Details: It will contain all the details of the System and the details of the owner.
6) Interconnections: Details of the connections that are made there like System connects to the other System and how those connections are made and secured.
7) Security Team Roles and Responsibilities: The security team should know the key roles and responsibilities they have been assigned.
8) Access and Authentication Process: The access of the Systems and the process which is being used for the authentication of the System.
9) Frequency of Reviewing the SSP: The Security Plan should be reviewed and updated in time for the concern of security of the organisation.
10) Awareness and Training Activities: There should be awareness about the SSP, and the training should be there to understand the security policies and applications to be applied.
Get Certified in the Field of Security With our ISSAP Training & Certification Sign Up Now!
How to Create a System Security Plan?
Creating and maintaining the System Security Plan is a very complicated task as it requires professional expertise. Some of the primary steps when you are starting to prepare an SSP are:
1) Define the Scope of the SSP
In Defining a Scope of SSP the main step is to understand the requirements and the right framework according to the needs of the companies. The Security framework depends on the needs of the organisation it differs according to the needs of the customers. The assets and the Systems must be detailed and identified to understand the main focus point of the Security Plan.
2) Establish Security Objectives
Once the scope for an SSP is done then the next step is to Establish security Objectives. This will make a walk-through path for Security Plan and help in ensuring the best Security practices. It is essential to understand and identify all the vulnerable areas within or outside the scope of the Security Plan.
Establishing these Security Objectives helps the company in reducing the risks and ensuring secure Systems.
3) Identify Security Controls
System Security Plan should have detailed information on the Security policies, procedures and processes because the security controls are essential to effective security. These security policies and procedures will provide clear guidance for personnel.
4) Implement the SSP
This involves validating proper functioning of System security, access control, vulnerability management, training and awareness, and the incident report. The security protocols must be validated for Systems Security, and it should be monitored frequently.
Access control and vulnerability management should be implemented in the System Security Plan so that sensitive and important information is accessed only by the authorised persons only and it will be safe from breaches.
5) Provide Training and Education
Initially all the employees should receive training in cyber security and the implementation strategies of security like CMMC and NIST 800-171. It should include reporting and identifying vulnerable and malicious activities, familiarity with the latest threats, and good understanding of the company's security policies and Security Plan.
6) Enhance the SSP
It is essential to perform risk management strategies in order to identify security gaps, threats and vulnerabilities. Frequent System audits should be there to find the weaknesses, misconfigurations and other notes from which a system is vulnerable to get attacked.
7) Secure Business Partners
If the company is hiring any third-party organisation for the security that must make sure that the organisation ensures all the standards, regulations, requirements and the policies of the company. Frequent monitoring should be conducted for the third-party security policies and procedures.
8) Develop Maintenance Procedures
Develop proper Maintenance Procedures for the System Security Plan to ensure the System is working perfectly and efficiently. There should be proper documentation of all the changes that are made in the System related to any modification or incidents that occurred.
By implementing a review process the companies can make sure that their Systems are working effectively to protect and secure their information.
9) Document the System Security Plan
Documentation of the System Security Plan is essential as the execution of plan. It should be clear, to the point and comprehensive while writing and organising the Security Plan. The document also needs to be presented to the personnel so to make sure that the plan is followed and is understood.
Standards and Best Practices for SSPs
Some of the Standards and Best System Security Practices are mentioned below:
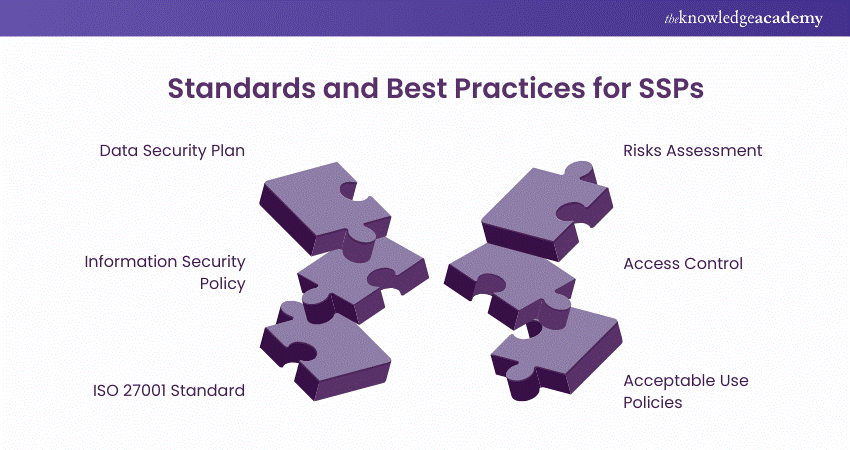
1) Data Security Plan: This security practice helps the cyber teams to understand the security risks and identify the data breaches. This will help the companies to overcome their financial and reputational losses.
2) Information Security Policy: It is the set of instructions and rules that basically describes how to manage, use and protect the resources and assets of the organisation. This policy is applicable to all the clients and the information stored digitally.
3) ISO 27001 Standard: The company which is providing third–party security to the Systems must have certified security standards.
4) Risks Assessment: A risks assessment plan should be there and implemented in all the functions of the business so to identify the potential risks and vulnerabilities in the System security.
5) Access Control: It regulates the authentication System that determines who can access the information, data and the resources in the company or organisation. It makes sure that the authorised person is allowed to access so to avoid data breaches and attacks.
6) Acceptable Use Policies: It defines the use of resources, equipment and services and the security measures according to the policies employees must take to protect the organisation’s information and resources.
Conclusion
In this era where security threats are increasing day by day, companies should give priority to the security Systems for protecting their Systems from attacks. A System Security Plan makes sure to maintain the secure environment from its tools and security practices. So, from this blog you got to know about how to implement and what is the need for implementing System Security Plan in the companies.
Want to know more about SSP? CISSP Training Course Register Now!
Frequently Asked Questions

System Security Plan mainly follows the three principles of information security which are integrity, availability, confidentiality. These three principles are crucial for protecting your company's information and data. These always make sure to protect your information and avoid the risks of attacks and cyber threats.

The objective of the System Security Plan is to document the security requirements and fulfil them what they have mentioned. They also fully describe the security posture of an information System including the system details and all the controls selected for the System.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various CISSP Training, including the CISSP Certification and ISSMP Training, and the ISSAP Training Certification Course. These courses cater to different skill levels, providing comprehensive insights into IT Security & Data Protection.
Our IT Security & Data Protection Blogs cover a range of topics related to CISSP, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Security Management skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 ISSMP Training
ISSMP Training
Mon 23rd Dec 2024
Mon 13th Jan 2025
Mon 10th Feb 2025
Mon 3rd Mar 2025
Mon 12th May 2025
Mon 9th Jun 2025
Mon 7th Jul 2025
Mon 4th Aug 2025
Mon 8th Sep 2025
Mon 6th Oct 2025
Mon 3rd Nov 2025
Mon 1st Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


