We may not have the course you’re looking for. If you enquire or give us a call on +60 1800812339 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Today, the safety of our digital world is paramount. Ethical hacking stands at the forefront of this defence, wielding hacking for good. But What is Ethical Hacking; Ethical Hacking, in essence, is the practice of breaking into systems - but with a twist. It’s all about finding and fixing weaknesses before the bad guys can get in. These digital knights, known as White Hat Hackers, use their powers for good, fortifying our cyber walls.
With cyberthreats on the rise, organisations are pouring more funds into Cyber Security than ever before. To give you an idea, in 2023, UK companies set aside a whopping 21.17 million GBP on average for Cyber Security. This hefty sum highlights just how critical it is to stay ahead of threats, safeguarding precious data and preserving trust.
In our blog, we’re going to unpack What is Ethical Hacking. From the ABCs of Cyber Security to the spectrum of hackers, and the ethical dilemmas they navigate - we’ve got it all. Plus, we’ll weigh in on the pros and cons of Ethical Hacking. So, are you ready to jump in? Let’s get started!
Table of Contents
1) Understanding Ethical Hacking
2) The process of Ethical Hacking
3) Common Ethical Hacking techniques
4) Benefits and challenges of Ethical Hacking
5) Conclusion
Understanding Ethical Hacking
Ethical Hacking is the authorised attempt to bypass security systems and identify vulnerabilities in computer systems, networks, or applications. Its scope extends to testing and enhancing security measures, protecting against potential cyber threats, and assuring the integrity of digital assets.
Understanding the definition, scope, and various types of hackers, along with the legal and moral aspects, offers a foundation for comprehending the role of legalised hacking in Cyber Security.
Types of Hackers
The concept of Hacking is quite simple, but it isn’t limited to one role or category. There are various roles in Ethical and Non-ethical Hacking. The three most prominent categories of Hackers are the following:

a) White Hat Hackers: These Ethical Hackers work with the proper legal methods and guide organisations by detecting the weaknesses in their systems and enhancing security.
They are usually the ones to whom the bug testing of the applications and website is assigned before releasing them to the public. All Types of Ethical Hacking come under White Hat Hacking.
b) Black Hat Hackers: These hackers are Considered the most notorious cyber-criminals. They are also known as Malicious Hackers who perform illegal activities using the vulnerabilities for malicious purposes or personal benefit.
They are usually the ones responsible for the Cyber Security breaches and stolen data that cause huge losses to the organisation.
c) Grey Hat Hackers: This group operates in a morally ambiguous space, exploiting vulnerabilities without explicit permission but intending to notify organisations about the weaknesses discovered.
As a result, Grey Hat Hackers are often unpredictable, as the intent behind their actions tends to be unknown.
Legal aspects of Ethical Hacking
White Hat Hacking operates under strict legal and ethical guidelines, requiring proper authorisation before conducting any security assessments. Once they Become an Ethical Hacker, they must adhere to these principles, respect privacy, and ensure their actions do not disrupt systems or networks or cause harm.
Once certified, they are expected to follow these standards diligently.
Key skills and knowledge required for Ethical Hackers
White Hat Hackers require a diverse skill set to identify vulnerabilities and secure systems effectively. The key skills include programming languages, network protocols, and Operating Systems proficiency. They must know hacking techniques, security tools, risk assessment, and strong problem-solving abilities.
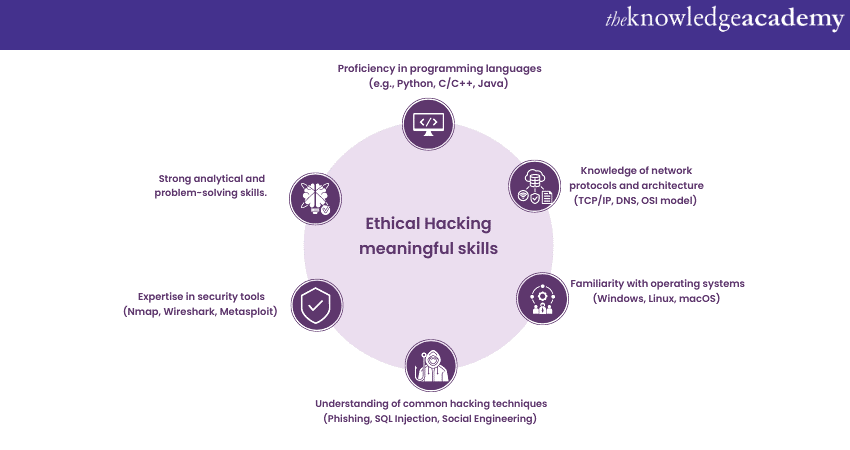
White Hat Hackers should also possess excellent communication skills to report findings and collaborate with stakeholders effectively. Furthermore, recognising the essential skills and knowledge needed for Ethical Hacking highlights the expertise and dedication needed to contribute effectively to maintaining digital security.
Learn the fundamentals of Ethical Hacking with our Ethical Hacking Professional Course!
The process of Ethical Hacking
White Hat Hacking process follows a systematic approach divided into multiple phases. Each phase plays an important role in identifying and addressing security weaknesses. These phases enhance the overall security posture of the target system or network.
Pre-engagement phase
In the pre-engagement phase, the White Hat Hacker establishes clear communication with clients to understand their objectives, scope, and specific requirements. This includes specifying the rules of engagement, obtaining proper authorisation, and signing necessary agreements. Gathering relevant information about the target system or network is necessary before proceeding.
Reconnaissance
Reconnaissance is also known as footprinting or information gathering. This preparatory phase aims to collect as much information as possible about the target. Before attempting any attack, Ethical Hackers gather essential details like passwords and employee information.
They might use tools like HTTPTrack to download entire websites or search engines like Maltego to research individuals through various links, job profiles, and news. Reconnaissance is a critical phase in Ethical Hacking. It helps identify potential attacks and assesses how vulnerable the organisation’s systems might be to those attacks.
Vulnerability assessment
During the vulnerability assessment phase, the White Hat Hacker uses various tools and techniques to identify weaknesses in the target system or network. This includes conducting vulnerability scans, analysing configuration weaknesses, and evaluating the effectiveness of security controls. The goal is to find potential vulnerabilities that attackers could exploit.
Exploitation
In the exploitation phase, the White Hat Hacker leverages identified vulnerabilities to gain unauthorised access or escalate privileges within the target system or network. This involves using various hacking techniques and tools to breach defences and assess the impact of the vulnerabilities. The objective is to understand the potential damage an attacker could cause.
Post-exploitation
After successfully gaining access to the target system or network, the White Hat Hacker focuses on maintaining persistence and exploring the compromised environment further. This stage involves lateral movement, privilege escalation, data extraction, and potentially gaining control over critical systems or sensitive information. It aims to simulate real-world scenarios and analyse the extent of harm that an attacker could cause.
Reporting
The reporting phase is essential for effective communication between the White Hat Hackers and the client. A comprehensive report detailing the findings, vulnerabilities, potential risks, and recommended countermeasures is generated. The report should be clear, concise, and actionable, providing the client with a roadmap to address and mitigate the recognised vulnerabilities.
Try our Ethical Hacking Training and learn to bypass the security of systems legally!
Common Ethical Hacking techniques
White Hat Hackers use various methods to assess the security of systems, networks, and applications. Here are some techniques they use to help organisations identify vulnerabilities, strengthen defences, and ensure the integrity and confidentiality of digital assets.
Network scanning and enumeration
Network scanning includes systematically exploring a target network to collect information about active hosts, open ports, and services running on them. Enumeration further extracts details like user accounts, shares, and network resources. These techniques help White Hat Hackers identify potential entry points and vulnerabilities in the network infrastructure.
Social engineering
Social engineering is a strategy that exploits human psychology to manipulate individuals into performing certain actions or revealing sensitive information. It involves tactics like phishing emails, pretexting, baiting, or impersonation. Ethical Hackers utilise social engineering to test an organisation’s awareness and educate employees about the risks associated with such attacks.
Password cracking
Password cracking involves discovering passwords by systematically trying combinations or using specialised tools. Ethical Hackers use this strategy to test the strength of user passwords and identify weak or easily guessable passwords. This helps organisations enforce stronger password policies and improve authentication security.
Denial of Service (DoS)
Denial of Service attacks aims to disrupt the availability of a system or network by jamming it with a flood of traffic or exploiting vulnerabilities to exhaust system resources. Ethical Hackers perform DoS attacks to test the resilience and responsiveness of the target infrastructure, allowing organisations to implement appropriate mitigation measures.
Wireless Hacking
Wireless hacking is the exploitation of vulnerabilities in wireless networks, such as Wi-Fi, to gain unauthorised access or intercept network traffic. Ethical Hackers use tools and techniques like brute-forcing Wi-Fi passwords, exploiting weak encryption, or conducting Man-in-the-Middle attacks to identify security weaknesses and enhance wireless network security.
Web Application Hacking
Web Application Hacking focuses on identifying vulnerabilities and weaknesses in web applications, including websites and web services. Ethical Hackers use techniques like SQL Injection, Cross-Site Scripting (XSS), and Session Hijacking to assess the security of web applications. This helps organisations address potential risks and protect sensitive data.
Try our Mastering Metasploit Framework Course and use Metasploit in Penetration Testing!
Benefits and challenges of Ethical Hacking
Understanding the benefits and challenges most White Hat Hackers face helps business firms make informed decisions about implementing proactive security measures. Ethical Hacking is a valuable tool in safeguarding organisations against cyber threats and strengthening their overall security posture.
Benefits of Ethical Hacking for organisations:
White Hat Hackers are important in most organisations to keep them safe from external attacks and cyber threats. Some of the Benefits of Ethical Hacking are the following:
1) Proactive vulnerability assessment: Ethical Hackers identify vulnerabilities, enhancing security.
2) Improved incident response: Simulated attacks refine incident response capabilities.
3) Enhanced security awareness: Educates employees, reducing successful attacks.
4) Compliance and regulatory requirements: Meets data protection and Cyber Security standards.
5) Safeguarding reputational and financial risks: Prevents damage, maintains trust, and protects the brand.
Challenges and limitations of Ethical Hacking
White Hat Hacking has many benefits, and it also has an equal number of challenges, some of them being as follows:
1) Scope limitations: Define assessment scope accurately to maximise coverage
2) Evolving threat landscape: Continuous learning to keep up with emerging threats
3) False positives negatives: Skilled hackers needed to interpret findings accurately
4) Legal considerations: Compliance with laws and ethical guidelines is essential
Balancing security and privacy concerns
Ethical Hacking requires a delicate balance between security and privacy concerns. Organisations must ensure that White Hat Hackers do not violate privacy laws or compromise sensitive data. Strong ethical frameworks, strict data protection measures, and transparent communication with stakeholders are essential to maintain this balance.
Conclusion
Through this blog, now we know What is Ethical Hacking? It’s a vital part of robust Cyber Security, involving proactive vulnerability assessments, enhancing incident responses, and ensuring regulation compliance. Skilled White Hat Hackers are indispensable in addressing the constantly evolving threats. We invite you to consider hacking as a fulfilling career path and to develop this invaluable skill set in our ever-evolving digital landscape.
Frequently Asked Questions

Ethical Hacking aims to identify and fix security vulnerabilities in systems, networks, or applications before malicious Hackers can exploit them. Ethical Hackers, also known as white-hat hackers, use their skills to enhance security, protect sensitive data, and assure the safety and integrity of digital assets.

Hackers use various programming languages, each suited for different tasks. Python is popular for its ease of use and powerful libraries, making it great for scripting and automation. JavaScript is often used for web hacking, while C and C++ are useful for system hacking. SQL is crucial for database attacks like SQL injection.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Ethical Hacking Courses, including the Ethical Hacking Professional Course and Mastering Metasploit Framework Course. These courses cater to different skill levels, providing comprehensive insights into What is Ethical Hacking?
Our IT Security & Data Protection Blogs cover a range of topics related to Ethical Hacking, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Ethical Hacking skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Ethical Hacking Professional
Ethical Hacking Professional
Thu 16th Jan 2025
Thu 6th Mar 2025
Thu 22nd May 2025
Thu 24th Jul 2025
Thu 4th Sep 2025
Thu 20th Nov 2025
Thu 18th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


