We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Given that ISO 27001 oversees defining how an Information Security Management System (ISMS) should be implemented in corporate environments, it is a suitable standard for businesses seeking to obtain ISO certification.
The internationally recognised ISO 27001 standards were jointly published by the ISO and IEC in 2005, with further revision made in 2013 to address the security risks. In 2017, there were two more revisions made, and a large-scale study was conducted in 2020 to address the effectiveness of ISO 27001 certification.
Table of Contents
1) What is ISO 27001?
2) What is ISMS?
3) What Benefits can ISO 27001 Provide to Businesses?
4) List the Key Features of ISO 27001
5) What are the ISO 27001 Clauses?
6) What are the ISO 27001 Controls?
7) Conclusion
What is ISO 27001?
ISO/IEC 27001 is a certification standard recognised worldwide for its best practices indicating the alignment between information security and ISMS. By managing information security, ISO 27001 helps organisations to address people, processes, and technologies.
ISO 27001 Access Control Policy was established to manage the information security of the organisation in any given situation, ensuring the protection of sensitive information through structured security measures and controls.
What is ISMS?
An ISMS is a systematic approach to control and manage the information security of the organisation. The framework of ISMS (Information Security Management System) enables the organisation to monitor, review, manage, improve, and implement information security policies in a unified setup, ensuring compliance with standards like ISO 27001 vs SOC.
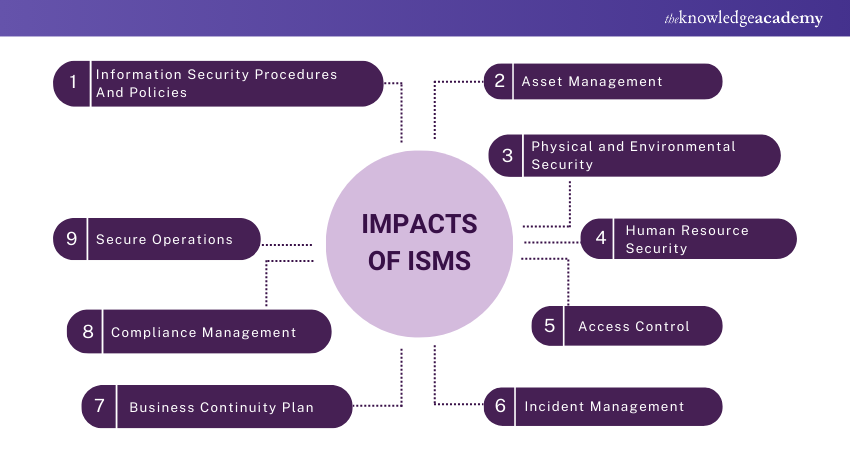
Following is the image depicting how ISMS can have an impact on your business.
People intending to lead audits in ISMS can join the ISO 27001 Lead Auditor Training.
What Benefits can ISO 27001 Provide to Businesses?
ISO 27001 is one of the most popular certifications related to information security standards recognised worldwide, as highlighted in the ISO 27001 Gap Analysis guide. The number of certification holders has grown widely, up to almost 450% growth in the last ten years. The demand for ISO 27001 certification holders underscores the value organizations place on information security. The benefits provided by ISO 27001, demonstrated through the ISO 27001 Audit, highlight the capability of these holders to meet the stringent requirements of the organization.
ISO 27001 Compliance information will help you with the risk management process and determine which security controls need to be maintained and implemented. By implementing strong ISO 27001 Physical and Environmental Security measures, organizations can significantly enhance their overall information security posture. Incorporating regular ISO 27001 Penetration Testing as part of the overall security framework strengthens the effectiveness of the ISMS
Let us have a look at the highlighted benefits of ISO 27001 mentioned below:
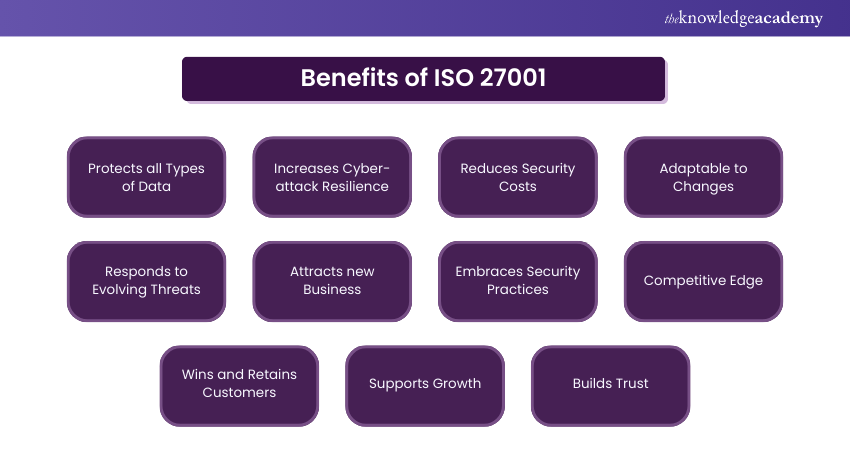
1) ISO 27001 requirements can help you protect all types of data and information, irrespective of whether the data is stored in digital or hard copy format or a cloud database.
2) Increased resilience to deal with cyber-attacks related to your organisation.
3) Helps you reduce the information security costs associated with data breaches.
4) Flexibility to adapt to organisational changes.
5) Respond to security threats evolving internally and externally in the organisation.
6) Organisations can bring in new business as the certification demonstrates high credibility and commitment to data security.
7) Understand the frequent risks and embrace security practices.
8) By ensuring frequent checks and regular internal audits you can gain an edge over the competitors.
9) Your commitment towards security by applying new and updated measures can win new business and retain new customers.
10) With low disruptions and security breaches, there will be an opportunity for the organisation to expand and grow steadily to reach its goals effectively.
11) Having obtained notable ISO certifications, the customers can trust your organisation to be safe and generate confidence among the associates.
Apply with ISO 27001 Certification to upgrade your career in Information Security Management now.
List the Key Features of ISO 27001
Following are the major features of ISO 27001
Risk Assessment and Analysis
The organisation must periodically complete a security risk analysis following the standards every time a significant change is proposed or implemented. Setting up risk acceptance criteria and defining how these risks will be measured is crucial for performing the appropriate analysis.
The possible effects of identified risks together with their likelihood and magnitude, should also be evaluated.
Commitment of Senior Management
The ISO 27001 Framework also stipulates that top management must show dedication to the ISMS and participate in the department within the business that oversees information security. Leaders have the duty to mentor staff members to make the system truly effective. The top management is accountable for ensuring all resources for system implementation are available and distributed appropriately.
Defining Goals and Strategies
The company must be transparent and sure during planning about the ISO 27001 Physical Security objectives it wants to achieve and the strategies it will establish to reach those goals. However, considering the safety needs of the organisation, the organisational goals must be specific and measurable.
Abilities and Resources
The organisation must also make sure that all the resources required for system maintenance and installation are on hand. Additionally, it is vital to determine the abilities that are required and to confirm that the people in charge are skilled enough.
Professionals involved in internal audits in ISMS can benefit from ISO 27001 Internal Auditor Training. Apply now!
What are the ISO 27001 Clauses?
The ISO standard has ten short management system clauses and a long Annex, which covers:
1) Standard Scope
2) Normative documental references
3) Terms and definitions in ISO/IEC 27000
4) Organisational Context
5) Leadership and support for policy
6) Planning an IS management, risk assessment, and risk treatment
7) Supporting an ISMS
8) Making ISMS Operational
9) Performance evaluation
10) Corrective action or improvement
Annex A: Objectives and a list of controls
If interested, this structure can help organisations comply with multiple other management standards.
Ready to boost your knowledge? Download the full ISO 27001 Standard PDF and enhance your understanding of information security!
|
Clause No. |
Clause Title |
Sub-clause No. |
Sub-clause Title |
|
1 |
SCOPE |
1.1 |
Define the scope of the information security management system |
|
2 |
NORMATIVE REFERENCES |
2.1 |
Identify and refer to relevant standards and documentation |
|
3 |
TERMS AND DEFINITIONS |
3.1 |
Clarify terms and definitions used within the standard |
|
4 |
CONTEXT |
4.1 |
Understand your organisation's Context |
|
|
|
4.2 |
Define the expectations of interested parties |
|
|
|
4.3 |
Clarify scope of Infosec management system |
|
|
|
4.4 |
Develop an Infosec management system |
|
5 |
LEADERSHIP |
5.1 |
Provide leadership and show that you support ISMS |
|
|
|
5.2 |
Establish an appropriate information security policy |
|
|
|
5.3 |
Assign ISMS roles, responsibilities, and authorities |
|
6 |
PLANNING |
6.1 |
Formulate actions to address risks and opportunities |
|
|
|
6.2 |
Assign ISMS roles, responsibilities, and authorities |
|
7 |
SUPPORT |
7.1 |
Support ISMS by providing resources |
|
|
|
7.2 |
Support ISMS by promoting competence |
|
|
|
7.3 |
Support ISMS by making people aware of duties |
|
|
|
7.4 |
Support ISMS by controlling ISMS communications |
|
|
|
7.5 |
Support ISMS by managing related information |
|
8 |
OPERATIONS |
8.1 |
Carry out planning and control your ISMS processes |
|
|
|
8.2 |
Conduct suitable information security risk assessments |
|
|
|
8.3 |
Implement information security risk treatment plans |
|
9 |
EVALUATION |
9.1 |
Monitor, Measure, and Analyze information security |
|
|
|
9.2 |
Set up audit program and use it to evaluate your ISMS |
|
|
|
9.3 |
Review your organization's ISMS at planned intervals |
|
10 |
IMPROVEMENT |
10.1 |
Identify nonconformities and take corrective action |
|
|
|
10.2 |
Improve information security management system |
Signup for our ISO 27001 Lead Implement Training courses and learn everything about the global standard for information security management systems
What are the ISO 27001 Controls?
A risk assessment needs to be performed to determine which controls are required and which can be excluded. It is not necessary to adopt all 114 controls in 14 groups and 35 categories. Ensuring the proper ownership and gaining a balance over risks and controls by performing risk assessments was one of the crucial factors for its ISO 27001 Latest Version.
Below is the list of 14 groups of control sets.
1) A.5 Information security policies
2) A.6 Organisation of information security
3) A.7 Human resource security
4) A.8 Asset management
5) A.9 Access control
6) A.10 Cryptography
7) A.11 Physical and environmental security
8) A.12 Operations security
9) A.13 Communications security
10) A.14 System acquisition, development, and maintenance
11) A.15 Supplier relationships
12) A.16 Information security incident management
13) A.17 Information security aspects of business continuity management
14) A.18 Compliance with internal and external requirements, such as policies and laws
Stay compliant with the ISO 27001 Policies and Procedures PDF—grab it now!
Conclusion
This blog helps you understand the ISO 27001 controls, features, benefits, clauses and other information which explains how an ISO 27001 certification can impact your business or an organisation. Acquiring a certification in ISO 27001 can boost your professional career and improve your overall skills to tackle various issues concerning IT-related threats.
Take the first step towards securing your organisation's information with our comprehensive ISO 27001 Foundation course – register now!
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 ISO 27001 Foundation
ISO 27001 Foundation
Mon 24th Mar 2025
Tue 22nd Apr 2025
Mon 23rd Jun 2025
Mon 28th Jul 2025
Mon 25th Aug 2025
Mon 22nd Sep 2025
Mon 27th Oct 2025
Mon 24th Nov 2025
Mon 15th Dec 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


