We may not have the course you’re looking for. If you enquire or give us a call on +31 208081674 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Every year, we hear news about some organisations or individuals who went through huge losses because they were hacked. However, hacking is not limited to breaking into a computer system for committing malicious acts. Some hackers work to figure out loopholes and weak areas in a system to make it less vulnerable to outside threats. These cyberpunks possess the Skills of Ethical Hackers, and they save thousands of cyber-attacks every year.
Ethical Hackers are the wall of safety to many organisations, allowing them to grow and evolve without the risk of being attacked. So, by learning about the skills they possess, you, too, can save your organisation’s valuable data. Read this blog to uncover the top 10 Skills of Ethical Hackers necessary for beginners and professionals that allow them to deal with outside threats on a regular basis.
Table of Contents
1) Who is an Ethical Hacker?
2) Top Skills of Ethical Hackers
a) Networking skills
b) Computer skills
c) Linux skills
d) Programming skills
e) SQL skills
f) Hardware knowledge
g) Knowledge in reverse engineering
h) Cryptography knowledge
i) Database skills
j) Problem solving skills
3) Conclusion
Who is an Ethical Hacker?
An Ethical Hacker is a professional who protects organisations or individuals against potential cyber threats. These Hackers are also referred to as "White Hat Hackers." They usually have the necessary background of a normal hacker, but they work under certain restrictions and boundaries provided by the organisation that hired them. They purposely stimulate an attack on the systems with the help of various techniques and tools to find out the vulnerabilities of the system.
Once the weak areas are spotted, Ethical Hackers work with the organisation to implement security improvements. These Hackers always remain up to date with technological advancements to understand all the important threats that can weaken an organisation. Many Ethical Hackers even carry certifications like Certified Information Systems Security Professional (CISSP) or Offensive Security Certified Professional. This certification validates their expertise in certain areas of Ethical Hacking.
Top Skills of Ethical Hackers
Ethical Hacking is a big concept, and Ethical Hackers require many different skills in order to prevent an organisation from various kinds of attacks. Let us uncover the most essential skills that Ethical Hackers should possess to do their job effectively. The following are some Skills of Ethical Hackers:
Networking skills
Networking essentially means building a network of multiple hosts using different paths for sending and receiving messages and data. An Ethical Hacker needs to understand networking because organisations can face many cyber-attacks when their devices containing essential information are connected to other machines. Here are some important networking skills that an Ethical Hacker should have:
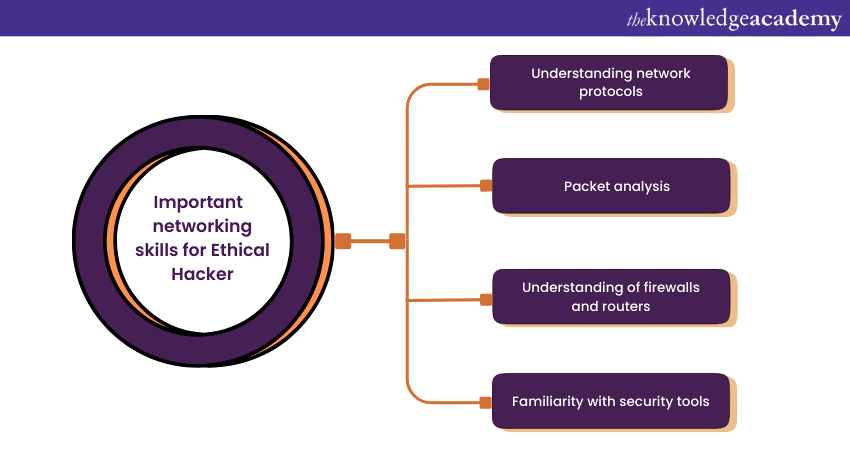
a) Understanding network protocols: Understanding network protocols helps an Ethical Hacker find areas generally prone to cyber-attacks. Suppose these vulnerabilities are not fixed; it's an open invitation to people looking to infiltrate the organisation. Therefore, an Ethical Hacker should possess deep knowledge of networking protocols, such as User Datagram Protocol (UDP), Hypertext Transfer Protocol (HTTP), and Domain Name System (DNS).
b) Packet analysis: In terms of data analysis, a packet is a small portion of data travelling through a computer network. Ethical Hackers should know how to analyse these packets to find potential security issues.
c) Firewalls and routers: A firewall is software that acts as a barrier against an untrusted network. Having an understanding of how firewalls work, if it has vulnerabilities, and the understanding of the difference between hardware and software firewalls allows an Ethical Hacker to gain control over security threats.
d) Security tools: Different security tools serve different purposes of securing a network. Having the knowledge of which tools can be used for scenarios gives Ethical Hackers the upper hand on potential threats.
Computer skills
Having expertise in computers makes a person capable enough to sense potential threats. This is the reason why having a firm hand on the computer is essential for an Ethical Hacker. Let us understand some of the critical computer Skills of Ethical Hacker that they should possess:
a) Operating Systems (OSs): Ethical Hackers work with various types of OSs to find loopholes and inefficiencies in the system. Having a basic as well as in-depth understanding of these Operating Systems allows them to accelerate at preventing organisations and individuals from various kinds of attacks.
b) Programming and scripting: Ethical Hackers write various codes using programming and scripting languages that help prevent cyber-attacks. Having a proper understanding of languages like Python, Bash, Ruby, and PowerShell allows Ethical Hackers to write different types of codes based on specific requirements.
c) Database Management: Sometimes, cyber-attacks happen because SQL Developers leave vulnerabilities in Database Management. This is the reason why an Ethical Hacker should be an expert in Database Management in order to find these loopholes and fix them.
d) Cloud Computing: As the technological industry keeps moving towards Cloud Computing, loopholes become more frequent, and organisations become more prone towards attacks. Having an understanding of Cloud Computing keeps Ethical Hackers in tune with technological advancements and threats.
Linux skills
Linux is free and open source, which makes it a great tool but also a security threat to organisations. Let us understand the importance of Linux Skills for Ethical Hackers:
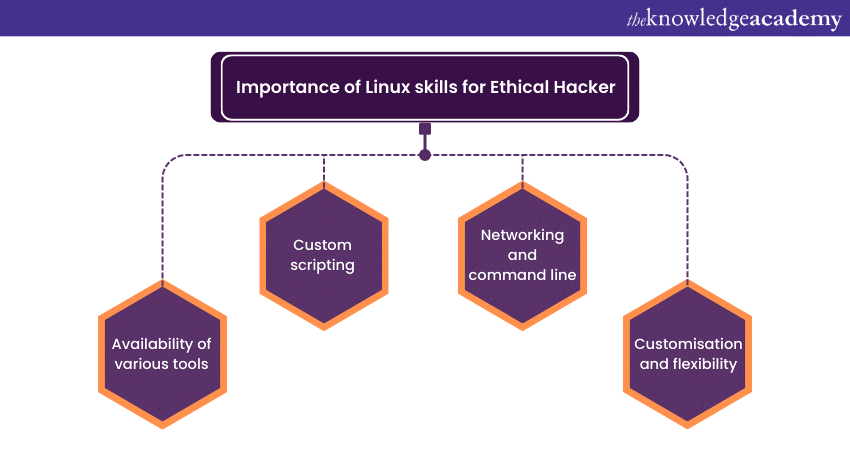
a) Availability of various tools: The most widely used tools for security and hacking these days are devised to run on Linux distribution. Ethical Hacking Tools like Nmap, Wireshark, and Metasploit are incredible for detecting cyber threats, and they work efficiently on Linux platforms.
b) Custom scripting: Mostly, Ethical Hackers have to write custom scripts to figure out the loopholes in a system automatically. Linux offers a friendly user base to write such scripts and also offers many languages like Python, Bash, Ruby, and Per.
c) Networking and command line: Linux has the best networking capabilities in the market today. It is widely used to manipulate network traffic and configurations. On the other hand, Ethical Hackers also use command line tools for tasks such as analysing logos, configuring network settings, and so on.
d) Customisation and flexibility: Linux systems are highly customisable, which gives the upper hand to an Ethical Hacker to build a stronger firewall and tailor their specific needs. This flexibility also comes in handy during testing the security.
Uncover the dimensions of Ethical Hacking and learn to reveal security flaws – join our Ethical Hacking Training today!
Programming skills
Programming skills are the most essential component of Ethical Hacking. Without having a strong grasp of various programming languages like Python, SQL, C++, and so on, an Ethical Hacker cannot write necessary codes and build strong firewalls to stop cyber-attacks. Programming Skills of Ethical Hackers also help them view the problem with a unique point of view, which makes it easy to find solutions. Here's how programming skills can help Ethical Hackers:
a) Tool development: Sometimes, Ethical Hackers need to develop customised tools and scripts to automate tasks, analyse vulnerabilities, and exploit security weaknesses. Strong programming skills help them to create these tools effectively.
b) Control development: Understanding programming languages is important for gaining control to take advantage of vulnerabilities in software or systems.
c) Reverse engineering: Ethical Hackers now and then need to reverse engineer software to understand how it works and how to defend it. This requires knowledge of programming languages.
d) Web application security: One can easily find many security vulnerabilities in web applications. This is the reason why Ethical Hackers evaluate the safety of web apps, including finding and exploiting vulnerabilities like SQL injection, cross-site scripting, and cross-site request forgery.
SQL skills
SQL skills are necessary for Ethical Hackers because they offer them identity, manipulate and demonstrate database and web application vulnerabilities. Let us understand these skills in detail:
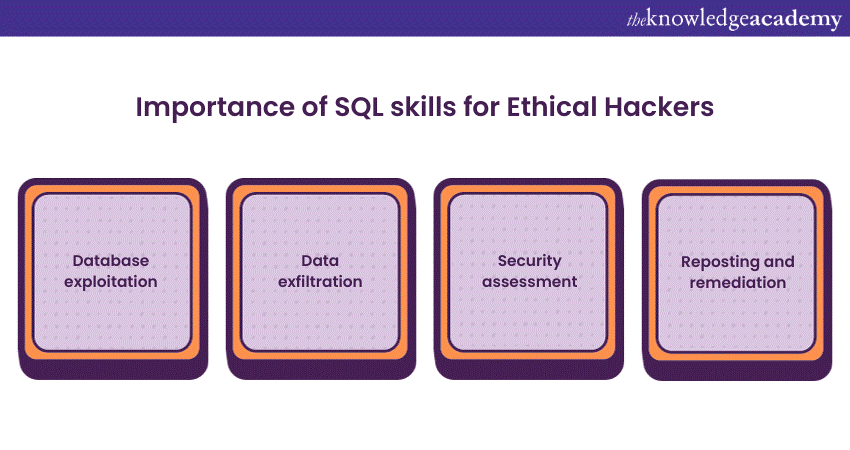
a) Database exploitation: Many web applications rely on databases to store and retrieve data, which makes them exposed to SQL injection attacks. By having knowledge of SQL, Ethical Hackers can detect and exploit these vulnerabilities to demonstrate security weaknesses to organisations and, therefore, help them improve their defences.
b) Data exfiltration: Ethical Hackers demonstrate how an attacker could steal data from a database. SQL Ethical Hacker Skills are important at these points for crafting queries that can extract data from a database without authorisation.
c) Security assessment: Ethical Hackers also conduct security checks and penetration tests on various applications to identify vulnerabilities. They use SQL for tests and assessing their security.
d) Reporting and remediation: After discovering SQL-related vulnerabilities, ethical document their findings and provide advice on remediation. A solid understanding of SQL becomes essential to explain the issues clearly to developers and administrators and assist them in fixing the weaknesses.
Hardware knowledge
Hardware knowledge is valuable for Ethical Hackers because it allows them to thoroughly assess and secure systems, identify exposures, and understand the full range of attack vectors. Let us understand these essential skills in more detail:
a) Understanding attack vectors: Hardware vulnerabilities are the flaws in the physical components of a device. These vulnerabilities might be unintentional, such as design flaws or manufacturing defects, or they can be intentional, like backdoor insertion during production. If these flaws are intentional, they can open paths for attack vectors that can compromise a system. Ethical Hackers explore these attack vectors to assess a system's security.
b) Physical security inspections: Ethical Hackers frequently conduct physical security inspections, which involve assessing the security of hardware components such as access control systems, surveillance cameras, and biometrics devices.
c) Signal manipulation: Hardware knowledge is important when dealing with wireless networks and combination protocols. For these instances, Ethical Hackers manipulate signals, intercept data, and launch attacks against hardware components involved in wireless communication.
d) Physical attacks: A solid understanding of hardware is essential to execute these attacks effectively. Ethical Hackers use physical attacks, such as hardware tampering or device cloning, to compromise a system's security.
Knowledge in reverse engineering
Reverse engineering is a systemic process used to analyse a product's code in order to decode its underlying architecture. This includes examining the code, data structures, algorithms and interactions between different components. By understanding the essence of reverse engineering, they can gain knowledge of how the product works internally.
In some cases, the original source code of a product might be incomplete. Reverse engineering helps in recovering the product's requirements and features by studying the codebase. This is useful for legacy systems where documentation is lost over time.
Learn the basics and master the phases of Hacking by registering for our Ethical Hacking Professional Course!
Cryptography knowledge
Cryptography is the knowledge of securing communication and data in the presence of competitors. Ethical Hackers should understand this because secure communication is a fundamental aspect of information security. Cryptographic techniques also allow sensitive information to remain confidential and cannot be intercepted or tampered with by hostile third parties during transmission.
Ethical Hacker's expertise in cryptographic algorithms and protocols protects data from eavesdropping. This is particularly important when assessing the security of communication channels like email, instant messaging, or data transfer. Cryptography not only increases confidentiality but also data integrity. Ethical Hackers understand cryptographic hash functions like digital signatures, which help them verify that data has not been altered during transmission or storage.
Database skills
Database Management is responsible for storing, organising, and managing data, making it a prime target for attackers. It also has security vulnerabilities that can be influenced by someone looking to attack the database. Ethical Hackers should be able to identify and exploit these flaws before other hackers. This includes understanding the complexities of database security, such as SQL injection, privilege escalation, and authentication flaws.
Databases store valuable and sensitive information such as customer data, financial records and business data. Ethical Hackers need to assess security controls in place to protect this data from unauthorised access, disclosure or modification. They even perform risk assessments on database systems to figure out the potential impact of a security breach by identifying weaknesses that could lead to data breaches, financial losses, or reputational damage.
Problem solving skills
Ethical Hackers sometimes encounter complex security challenges. These challenges involve intricate systems, multiple layers of security, and evolving attack vectors. These Ethical Hacker Skills help analyse these issues, understand their underlying causes, and create effective strategies to address them.
Cyberattacks also evolve constantly, so Ethical Hackers need to think creatively to anticipate new attack vectors and vulnerabilities. Analytical Skills of Ethical Hacker also help them assess various aspects of a system to form a broad understanding of the security landscape.
Conclusion
All the Skills of Ethical Hackers that we discussed above are important to uncover the liabilities of an organisation and find permanent solutions for them. With a proper set of skills, an Ethical Hacker can save time, capital and sensitive information of a company or individual and prevent them from harm.
Understand the importance of using Metasploit in Penetration Testing and learn how to restore Metasploit data – Sign up for our Mastering Metasploit Framework Course today!
Frequently Asked Questions
Upcoming Batches & Dates
Date








 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


