We may not have the course you’re looking for. If you enquire or give us a call on +64 98874342 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

In a world dominated by data, hackers circle around like a hungry shark waiting to pounce on any weaknesses. Once they sniff out potential weaknesses, they will rip out the prey of every bytes of data. In order to protect against such a formidable foe, organisations need equally strong warriors; they need Ethical Hackers. Ethical Hackers are knights in shining armour who can safeguard organisations and individuals from such dark forces. If you are curious about How to Become an Ethical Hacker, then this blog is for you!
Table of Contents
1) What is Ethical Hacking?
2) Steps to Become an Ethical Hacker?
3) Necessary Skills for Ethical Hackers
4) Ethical Hacking tools
5) Conclusion
What is Ethical Hacking?
Ethical Hacking involves the authorised and proactive discovery of vulnerabilities in a computer system, application, or data using the strategies and actions of malicious attackers. This practice helps identify security vulnerabilities that can then be resolved before a malicious attacker has the opportunity to exploit them.
What Does an Ethical Hacker Do?
Ethical Hackers work to find, rectify, and test an organisation's systems for vulnerabilities. To perform this effectively, they follow some guidelines and obtain permission from the organisation to simulate real cyberattacks. Let's explore some of their tasks and responsibilities:
a) Conducting System Assessments: They assess how someone might potentially breach the organisation’s system.
b) Performing Penetration Testing: They employ various techniques to demonstrate how hackers could execute a cyberattack.
c) Reporting Security Breaches: They notify the organisation about any security issues they discover.
d) Maintaining Confidentiality: They ensure that all findings remain confidential between themselves and the client or company.
e) Examining Technology Infrastructure: They analyse the organisation’s operating systems and networks for weaknesses.
Steps to Become an Ethical Hacker
The following are the steps to become an Ethical Hacker:
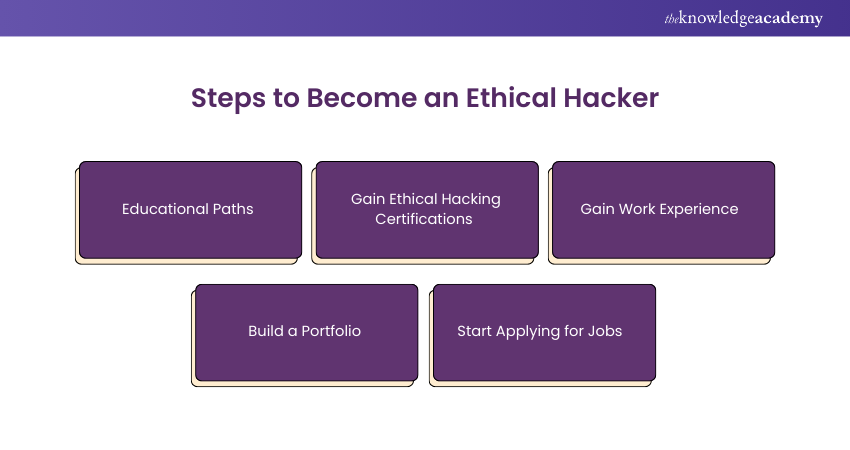
Educational Paths
1) Obtain a Degree:
a) A bachelor’s degree in information technology, computer science, or a related field is beneficial.
b) Offers a solid foundation in computing principles and Cyber Security.
2) Learn Programming:
a) Knowing programming languages such as Python, C++, and JavaScript is crucial.
b) It helps in understanding how software and systems operate, which is essential for identifying vulnerabilities.
Gain Ethical Hacking Certifications
Earning Certifications such as:
a) Certified Ethical Hacker Certification
b) Ethical Hacking Essentials Certification
c) CompTIA Security+ Certification
These certifications are recognised by employers and can enhance your job prospects.
Gain Work Experience
1) Entry Level Jobs:
a) Start with roles such as tech support, network administrator, or security analyst.
b) These positions offer hands-on experience with IT systems and security protocols.
2) Practice Hacking:
a) Use online platforms to practice your hacking skills in a safe, controlled environment.
b) These platforms provide real-world scenarios to test and enhance your abilities.
Build a Portfolio
a) Building portfolio includes detailed descriptions of the projects you have worked on.
b) Clearly list the skills you have used in each project.
c) Display any relevant certifications you have earned.
d) Provide detailed accounts of any penetration tests you have conducted.
e) Highlight specific vulnerabilities you have discovered.
f) Explain the strategies you used to resolve the identified vulnerabilities.
Start Applying for Jobs
1) Identify Opportunities:
a) Start by identifying job opportunities in sectors that require Ethical Hackers.
b) These sectors include private companies, government agencies, and specialised Cyber Security firms.
c) Use job search platforms like LinkedIn, indeed, and Glassdoor to find relevant positions.
2) Networking:
a) Collaborate with professionals in the Cyber Security field through online forums, networking events, and social media platform
b) Networking can help you learn about job openings that may not be advertised publicly.
3) Job Boards:
a) Regularly check Cyber Security-specific job boards and websites.
Necessary Skills for Ethical Hackers
To become a successful Ethical Hacker, here are some of the essential skills:
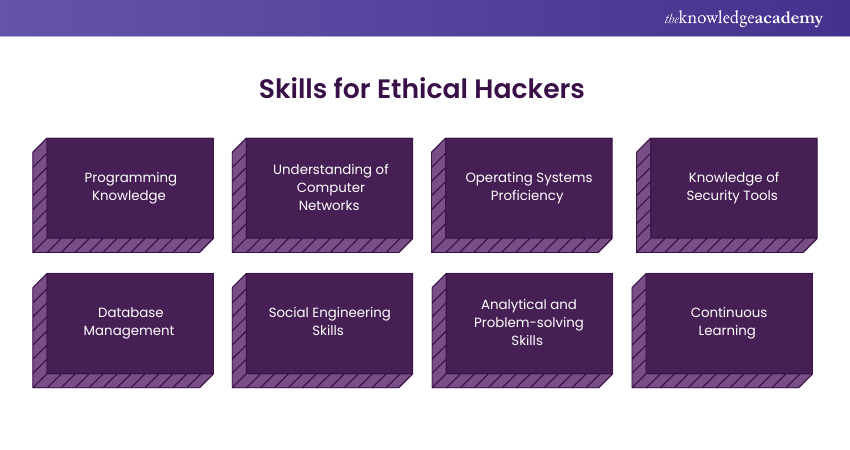
1) Programming Knowledge
Languages:
Expertise in programming languages such as C++, Python, JavaScript, and SQL is crucial. These languages help you understand how software and systems work, enabling you to identify and exploit vulnerabilities.
2) Understanding of Computer Networks
a) Network Protocols:
Knowledge of TCP/IP, DNS, HTTP, and other network protocols is essential. Understanding how data travels across networks helps in identifying potential security weaknesses.
b) Network Security:
Familiarity with firewalls, routers, switches, and intrusion detection/prevention systems is important for securing network infrastructure.
3) Operating Systems Proficiency
Windows and Linux:
Expertise in both Linux and Windows operating systems is necessary. Many servers and systems run on these platforms, and knowing how to navigate and secure them is vital.
4) Knowledge of Security Tools
a) Penetration Testing Tools:
Familiarity with tools like Metasploit, Nmap, Wireshark, and Burp Suite is essential for conducting penetration tests and vulnerability assessments.
b) Cryptography:
Understanding encryption and decryption methods, as well as how to implement them, is crucial for protecting data.
5) Database Management
SQL Proficiency:
Proficiency in database management systems and SQL is important for identifying and exploiting vulnerabilities in databases.
6) Social Engineering Skills
Psychological Manipulation:
Understanding social engineering techniques, such as phishing and pretexting, helps in identifying and mitigating human-related security risks.
7) Analytical and Problem-solving Skills
a) Critical Thinking:
The ability to analyse complex systems and think critically about potential vulnerabilities and solutions is essential.
b) Attention to Detail:
Being meticulous and detail-oriented helps in identifying subtle security flaws that others might miss.
8) Continuous Learning
Staying Updated:
Cyber Security is a constantly evolving field. Staying updated with recent trends, tools, and techniques through continuous learning and professional development is crucial.
Join the Ethical Hacking Professional Course - advance your skills and secure your career today!
Ethical Hacking Tools
Here are some of the most popular tools used by Ethical Hackers:
1) Nmap:
a) Purpose: Network scanning and mapping tool.
b) Description:
Network Mapper (Nmap) is widely used for discovering hosts and services on a computer network. It helps identify open ports, running services, and potential vulnerabilities, making it essential for network assessment.
2) Social Engineer Toolkit (SET):
a) Purpose: Social engineering attacks simulation.
b) Description:
SET is a framework designed for social engineering attacks, allowing Ethical Hackers to simulate phishing, credential harvesting, and other social engineering tactics to assess human vulnerabilities in organisations.
3) Wireshark:
a) Purpose: Network protocol analyser.
b) Description:
Wireshark is a tool for capturing and analysing network traffic in real time. It helps Ethical Hackers inspect packets to identify vulnerabilities and potential security issues within network communications.
4) Burp Suite:
a) Purpose: Web application security testing.
b) Description:
Burp Suite is a comprehensive platform for testing web applications. It includes various tools for scanning, crawling, and exploiting web vulnerabilities, making it essential for Ethical Hackers focusing on application security.
5) Kali Linux:
a) Purpose: Penetration Testing Operating System.
b) Description:
Kali Linux is a specialised Linux distribution designed for penetration testing and Ethical Hacking. It comes pre-installed with numerous tools and utilities that facilitate various hacking tasks, making it a favourite among Ethical Hackers.
6) OWASP ZAP (Zed Attack Proxy):
a) Purpose: Web application security scanner.
b) Description:
OWASP ZAP is an open-source tool used for finding vulnerabilities in web applications. It provides automated scanners and various tools for manual testing, making it a valuable resource for Ethical Hackers.
7) John the Ripper:
a) Purpose: Password cracking tool.
b) Description:
John the Ripper is a fast password-cracking tool that supports various encryption algorithms. It is commonly used to test password strength and recover weak passwords in systems.
8) Aircrack-ng:
a) Purpose: Wireless network security assessment.
b) Description:
Aircrack-ng is a suite of tools used for assessing the security of wireless networks. It concentrates on different aspects of Wi-Fi security, including monitoring, attacking, and cracking WEP and WPA/WPA2 encryption.
9) SQLMap:
a) Purpose: Automated SQL injection tool.
b) Description:
SQLMap is a free tool that automates the process of identifying and attacking SQL injection vulnerabilities in web applications. It helps Ethical Hackers identify database security flaws effectively.
10) Metasploit:
a) Purpose: Penetration testing framework.
b) Description:
Metasploit is a powerful tool used for developing and executing exploit code against remote targets. It provides a vast library of exploits and payloads, allowing Ethical Hackers to simulate attacks and test system security.
Master the Mastering Metasploit Framework Course - enhance your Ethical Hacking skills and boost your career today!
Conclusion
Understanding How to Become an Ethical Hacker opens the door to a rewarding career in Cyber Security. By acquiring essential skills, earning certifications, and gaining practical experience, you can play an important role in safeguarding digital systems. So, start your journey today and contribute to a safer online world!
Try our Ethical Hacking Training and learn to legally bypass the security of systems!
Frequently Asked Questions

A career in Ethical Hacking progresses through stages: education, entry level experience, intermediate certifications, professional roles, advanced expertise, and continuous learning. Each stage builds on the previous one, enhancing skills and knowledge.

Hackers often use programming languages such as Python for scripting and automation, JavaScript for web exploits, C and C++ for system level programming, and SQL for database manipulation. Each language serves specific purposes in Ethical Hacking and penetration testing.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and Interview Questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Ethical Hacking Training, including Ethical Hacking Professional and Mastering Metasploit Framework. These courses cater to different skill levels, providing comprehensive insights into Ethical Hacker Roles and Responsibilities.
Our IT Security & Data Protection Blogs cover a range of topics related to Ethical Hacking, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your IT Security skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Ethical Hacking Professional
Ethical Hacking Professional
Thu 16th Jan 2025
Thu 6th Mar 2025
Thu 22nd May 2025
Thu 24th Jul 2025
Thu 4th Sep 2025
Thu 20th Nov 2025
Thu 18th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


