We may not have the course you’re looking for. If you enquire or give us a call on +64 98874342 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

What if you had a toolkit packed with powerful controls to simplify the triple duty of protecting data, managing risks, and dodging cyber threats? Wonder no more because ISO 27001 Annex A controls will help you out! Being the gold standard in securing organisational data, ISO 27001 Controls will muster the muscles of Annex A to strengthen your organisation’s Information Security Management System (ISMS).
This blog dissects everything you need to know about the ISO 27001 Controls, from asset management and cryptography to system acquisition and compliance. So read on and expand the frontiers of information security for your organisation!
Table of Contents
1) What is ISO 27001 Annex A?
2) Differences Between ISO 27001 and ISO 27002?
3) ISO 27001: The top Four Most Failed Controls
4) How to Decide Which ISO 27001 Controls to Implement?
5) How Many ISO 27001 Controls are Present?
6) The 14 Categories of ISO 2001 Controls
7) Who is Responsible for Implementing Annex A Controls?
8) Is it Necessary to Adopt ISO 27001 in an organisation?
9) Conclusion
What is ISO 27001 Annex A?
ISO 27001 is one of the best International Information Security Standards set for Information Security Management Systems (ISMS) and their requirements. The controls enlisted in the Annex are used to ensure asset information security. The standard controls of ISO 27001 are defined/outlined in ISO 27001 Annex A. Based on the scope of your organisation, you are at leverage to select from 114 measures specified in ISO 27001 Annex A – a portfolio for information security controls.
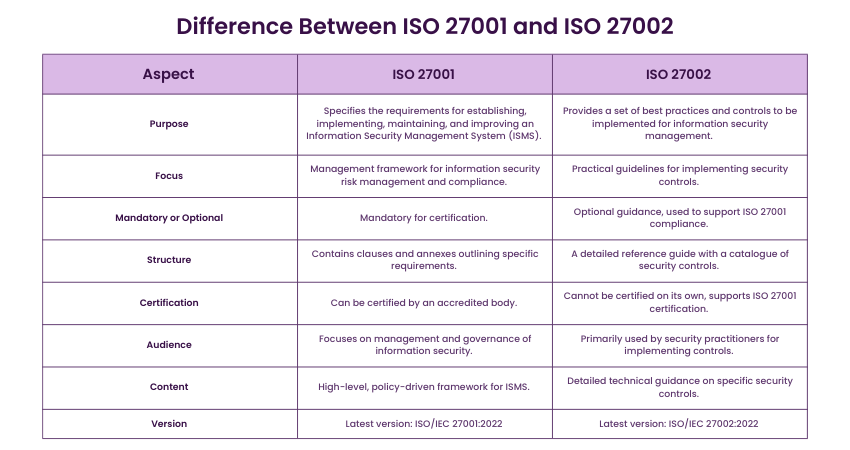
Difference Between the ISO 27001 and ISO 27002 Standards?
ISO 27001 and ISO 27002 are both essential standards in the field of information security, but they serve distinct purposes. While ISO 27001 focuses on establishing an Information Security Management System (ISMS), ISO 27002 provides practical guidance on implementing specific controls. Together, they ensure a robust approach to managing and securing information.
Upgrade your career in Information Security Management, by signing up for our ISO 27001 Training now!
ISO 27001: The top Four Most Failed Controls
Without a structured plan, implementing ISO 27001 can be a major challenge. Various industries encounter some common failed controls as detailed below:
1) Supplier Security: The objective of this control is to protect information assets that your suppliers handle. This control can fail for the following reasons:
a) Not every supplier is risk-assessed
b) Complexity and lack of documentation
c) Inadequately defined supplier criteria
d) Failing to provide proof of compliance
e) Failing to perform supplier checks
2) Operations Security: This control aims to ensure the adequate and secure operation of information processing facilities. The failure of this control can be attributed to the following:
a) Missing details in the documentation
b) Lack of evidence of operations during ISO 27001 audit
c) Change management issue arising from introducing, for example, a new ERP system
d) Improper logging and monitoring of logs
3) Communication Security: This control aims to ensure that the information processed in networks and information processing facilities is properly protected. The reasons for its failure include:
a) Lack of network protection
b) Lack of non-disclosure agreements (NDAs)
c) Lack of secure communication channels for sensitive information
4) Asset Management: This control identifies, protects, and accounts for information assets and defines their ownership and acceptable use. The reasons for its failure include:
a) Using shadow information technology such as free online without knowing how company information is being processed.
b) Lack of awareness about relevant information assets
How to Decide Which ISO 27001 Controls to Implement?
Deciding which Annex A controls to implement helps determine whether an organisation becomes ISO 27001 certified. To assess their Statement of Applicability (SoA) for implementing controls, firms must consider various factors, including:
1) Industry
2) Operations model
3) IT environment
4) Organisational size
5) Technology stack
6) Information-security risks
Suppose a healthcare facility seeks compliance certification pertaining to HIPAA, which is short for the Health Insurance Portability and Accountability Act (HIPAA). In that situation, the organisation will need a comprehensive system for every defined control area in the compliance category.
Please remember that, for example, the supplier relationships category will be relevant only to organisations that collaborate with suppliers. Accordingly, the Physical and Environmental Security category will be irrelevant to a business that relies solely on Cloud-based applications and works remotely.
How Many ISO 27001 Controls are Present?
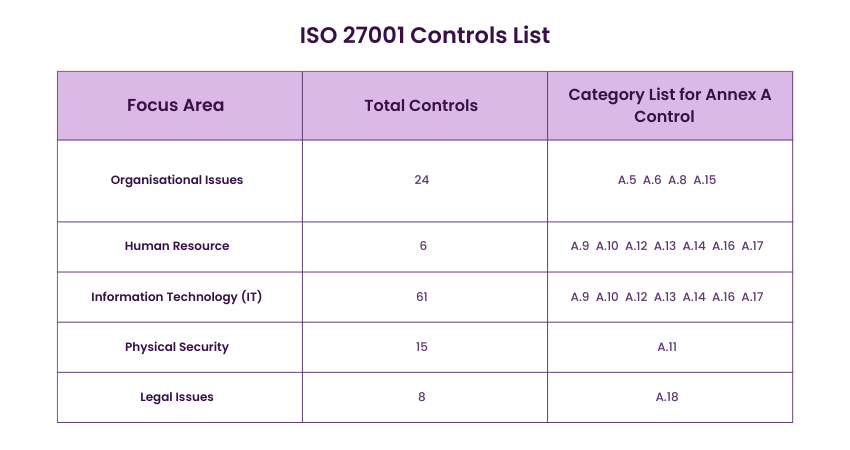
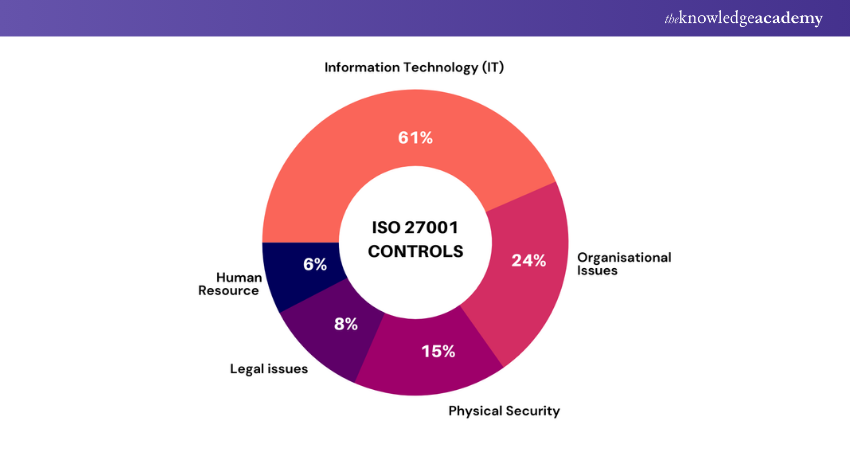
The Controls in Annex A of 27001 are divided into 14 categories. For effective Risk Management, these 14 categories have 114 ISO 27001 Controls outlined as tools. The controls can be applied based on the results of the Risk Assessment of your organisation.
The objective of this framework is to safeguard the integrity, confidentiality, and availability of information.
To understand which areas of organisation the Control sets are related to, check the following list of Annex A controls breakdown.
The 14 Categories of ISO 27001 Controls
The 14 Control Categories of ISO 27001 Annex A can be listed down as follows:
1) Information Security Policies
2) Organisation of Information Security
3) Human Resources Security
4) Asset Management
5) Access Control
6) Cryptography
7) Physical and environmental security
8) Operational Security
9) Communications Security
10) Systems Acquisition, Development and Maintenance
11) Supplier relationships
12) Information Security Incident Management
13) Information Security Aspects of Business Continuity Management
14) Compliance
Each of the 14 categories of Annex A Controls have specific objectives and security areas to improve Information Security. A total of 114 Controls are grouped under the 14 ISO 27001 Annex A categories. Below is the Comprehensive list of the 14 Control Categories:
1) Annex A.5 - Information Security Policies (2 Controls)
Objective:
To keep control over the policies related to Information Security and ensure they are written and reviewed according to the organisational requirements.

2) Annex A.6 - Organisation of Information Security (7 Controls)
Objective:
To manage the framework and assign the roles and responsibilities to be implemented in Information Security.
To establish security guidelines on employees' access, information storage, and processing.
3) Annex A.7 - Human Resource Security (6 Controls)
Objective:
a) To brief the allied parties of the organisation to understand the terms and conditions, responsibilities, and other requirements necessary during the employment tenure.
b) Conduct background verification
c) Execute formal disciplinary processes
d) Adhering to Information Security policies to protect the interests of the organisation
4) Annex A.8 - Asset Management (10 Controls)
Objective:
a) To classify, identify, manage, and prevent information of assets from being exposed.
b) It also helps implement classification schemes, define what can be used, and outline procedures to implement and safely dispose of information and media.
5) Annex A.9 - Access Control (14 Controls)
Objective:
a) Preventing unauthorised access to protect critical information (like PINs and Passwords).
b) Limit and implement Access Control policy and rights and regulate programs with override capabilities.
6) Annex A.10 - Cryptography (2 Controls)
Objective:
a) Maintain the authenticity and confidentiality of vital information to ensure key management and encryption.
b) Outlines Cryptographic policies, keys, usability, and validity period.
7) Annex A.11 - Physical and Environmental Security (15 Controls)
Objective:
a) To prevent and have control over interruptions caused during operations due to unauthorised access. Also, to prevent theft, loss, or damage of assets.
b) Securing transport bays, regular equipment services and maintenance.
c) Defining and implementing a physical security perimeter against potential threats.
8) Annex A.12 - Operational Security (14 Controls)
Objective:
a) To protect facilities from malware
b) Maintain consistency across activity logs
c) Avoid loss of data
d) Reduce disruptions
e) Mitigate technical risks ensuring the integrity of information processing facilities.
This involves creating awareness among users, installing anti-malware software, following backup policies, evaluating risks regularly, documenting the procedures, and monitoring software installations.
9) Annex A.13 - Communications Security (7 Controls)
Objective:
a) To monitor internal and external information transfer.
b) Implement network security and information transfer policies across the organisations’ communication facilities.
10) Annex A.14 - System Acquisition, Development and Maintenance (13 Controls)
Objective:
a) When installing new systems or updating existing systems ensure those Information Security requirements are met across the information system.
b) Ensure that only authorised personnel have the access to the data used for testing.
c) Regulate testing security facilities, establish secure development areas, and avoid misrouting through public networks, and unauthorised disclosures.
11) Annex A.15 - Supplier Relationships (5 Controls)
Objective:
a) Maintain an agreed level of information security with your suppliers and ensure that access to valuable information and assets is protected.
b) Formal risk mitigation agreements requiring regulatory approvals, audits, and ongoing monitoring.
c) Ensures systematic reviews, verifies compliance with information security standards and enhances overall risk management.
12) Annex A.16 - Information Security Incident Management (7 Controls)
Objective:
a) Includes effective and consistent management of information security incidents.
b) Involves rapid incident response in line with established procedures through appropriate management channels.
13) Annex A.17 - Information Security Aspects of Business Continuity Management (4 Controls)
Objective:
To ensure that the information processing facilities are available to confirm the organisations’ continuity plans of Information Security.
14) Annex A.18 - Compliance (8 Controls)
Objective:
Ensure the organisational requirements are met to carry out Information Security to avoid security risks/breaches of a statutory, legal, and contractual nature.
ISO 27001 Compliance involves safeguarding against any implications such as loss or theft to ensure the protection of sensitive information, review and identify the compliance requirements of the information system.
Plan and conduct your Internal Audits by signing up for our ISO 27001 Internal Auditor course now!
Who Implements the Annex A Controls?
Majority of the Controls instituted in the ISO 27001 Annexure may be assumed to be under the jurisdiction of the IT department. However, the standard thoroughly addresses all the three pillars of Information Security:
1) People
2) Processes
3) Technology
Moreover, the IT department does indeed contribute to the assessment and treatment of risk. Now most of the Controls demand the expertise of employees from all departments of the organisation, which entails the creation of a team comprising many departments. This newly made team will be responsible for handling the implementation process of the ISO 27001 Standard.
More importantly, it is generally the responsibility of the Information Security or Infosec Officer to lead the implementation process of the ISO 27001 Controls. They also oversee the organisation’s compliance with the standard’s guidelines and ISO 27001 Physical Security. The organisation are responsible for ensuring the integrity and application of the Controls instituted in the Annexure. Their responsibility owes to the reason that they are the organisation’s first line of defence against a threat or a cyber attack, hence being a shared responsibility
It is vital to note that the organisation’s management also needs to be onboard with the commitment to compliance of the standard as their review of the standard’s implementation is necessary. The review and approval of the ISO 27001 policies and processes also need to be handled by them.
Manage and improve your organisation’s ISMS by signing up for ISO 27001 Lead Implementer Course now!
Is it Necessary to Adopt ISO 27001 in an Organisation?
Here are a few provided Benefits of ISO 27001 Compliance mentioned, from which your organisation can gain significant boost:
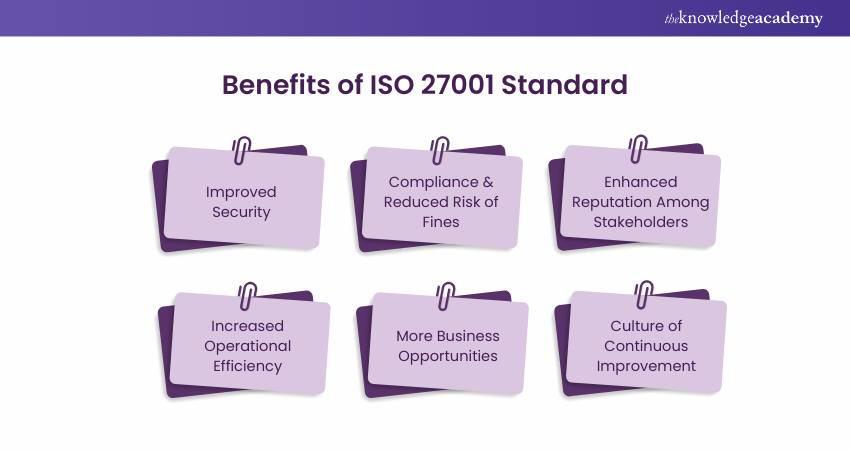
1) All forms of Information Security that includes cloud-based, paper-based, and digital data
2) Centrally managed framework provided to secure all types of information in one place
3) Quick response against security threats
4) High resilience to cyber attacks
5) Cost mitigation to tackle ineffective defence technology
6) Protection of sensitive and confidential information to maintain the integrity
7) Protection against technology-based risks and other threats to ensure the complete safety of the organisation
Download the ISO/IEC 27002 PDF now and enhance your organization's information security practices with the latest standards and guidelines.
Conclusion
In conclusion, mastering the Annex A controls of ISO 27001 is key to building a strong security framework that reliably safeguards your organisation’s information assets. By understanding and implementing these ISO 27001 Controls, as detailed in this blog, you can manage risks effectively, strengthen compliance, and build deeper trust with stakeholders.
Become an expert in ISO 27001 audits. Register in our ISO 27001 Lead Auditor Course today!
Frequently Asked Questions
What is the Difference Between ISO 27001 and SOC 2 Controls?

Here are the two biggest differences between ISO 27001 vs SOC 2 controls:
a) ISO 27001 is internationally recognised, while SOC 2 is more prevalent in the United States.
b) ISO 27001 requires the implementation of all the controls, while SOC 2 enables organisations to choose relevant controls from the five trust services criteria (TSC).
What is the Difference Between ISO 27001 and CIS Controls?

The difference between ISO 27001 and CIS controls are:
ISO 27001 focuses on governance with a comprehensive framework for managing information security risks, offering formal certification. CIS Controls provide actionable security steps and tools for self-assessment but lack certification.
What are the Other Resources and Offers Provided by The Knowledge Academy?

The Knowledge Academy takes global learning to new heights, offering over 3,000 online courses across 490+ locations in 190+ countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.
What is The Knowledge Pass, and How Does it Work?

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.
What are the Related Courses and Blogs Provided by The Knowledge Academy?

The Knowledge Academy offers various ISO 27001 Courses, including the ISO 27001 Foundation Course and the ISO 27001 Lead Auditor Course. These courses cater to different skill levels, providing comprehensive insights into What is ISO.
Our ISO & Compliance Blogs cover a range of topics related to ISO standards, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your ISO knowledge base, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 ISO 27001 Foundation
ISO 27001 Foundation
Mon 17th Mar 2025
Mon 12th May 2025
Mon 7th Jul 2025
Mon 1st Sep 2025
Mon 10th Nov 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


