We may not have the course you’re looking for. If you enquire or give us a call on + 1-866 272 8822 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Have you ever wondered how companies stay one step ahead of cybercriminals? The answer lies in their proactive security approach, using Ethical Hacking Tools to identify and fix vulnerabilities before exploitation.
But what exactly makes these tools so vital in the fight against cybercrime? From vulnerability scanners that comb through systems for weak points to password crackers that test the strength of digital locks, each Ethical Hacking Tool plays a vital role.
Ready to discover the top Ethical Hacking Tools that are essential for every Cyber Security warrior? Let’s embark on this journey and uncover the secrets behind these indispensable tools that keep our digital world safe.
Table of Contents
1) Understanding Ethical Hacking Tools
2) Why are Ethical Hacking Tools Important?
3) Top Ethical Hacking Tools
a) Metasploit
b) Wireshark
c) John the Ripper
d) Burp Suite
e) Nmap (Network Mapper)
f) Nikto
g) Kismet
h) Acunetix
i) OpenVAS
j) Ettercap
4) Conclusion
Understanding Ethical Hacking Tools
Ethical Hacking Tools are specialised software applications designed to detect, exploit, and fix security vulnerabilities in computer systems and networks. Utilised by Ethical Hackers or White-hat Hackers, these tools are essential for conducting penetration testing and security assessments with authorised access.
The primary objective is to enhance the security posture of systems by proactively identifying and addressing potential threats. This proactive approach ensures vulnerabilities are mitigated before malicious hackers, known as Black-hat Hackers, can exploit them.
Common tools used by Ethical Hackers include vulnerability scanners, password crackers, and network analysers. These tools collectively help safeguard against cyber threats and improve overall Cyber Security resilience.
Why are Ethical Hacking Tools Important?
Ethical Hacking Tools are crucial for several reasons:
1) Risk Management: They help organisations identify the most valuable and vulnerable parts of their IT ecosystem, making it easier to prioritise and protect critical assets.
2) Regulatory Compliance: These tools assist organisations in adhering to data security and privacy regulations, such as HIPAA and GDPR, ensuring legal compliance and protecting sensitive information.
3) Enhanced Cyber Security: Ethical Hacking Tools help organisations proactively address vulnerabilities, reducing security incidents and lowering cyberattack costs.
Become a Certified Ethical Hacker - join our Ethical Hacking Professional Course and protect systems from cyber threats now!
Top Ethical Hacking Tools
As organisations strive to safeguard their networks, systems, and sensitive data, Ethical Hacking Tools have become indispensable resources for Cyber Security professionals. Some of these common ethical tools for White hat hacking are as follows:
1) Metasploit
The Metasploit Framework is an open-source tool, while Metasploit Pro is a commercial version that offers a 14-day free trial. Metasploit is designed for penetration testing, allowing Ethical Hackers to develop and execute exploit codes against remote targets.
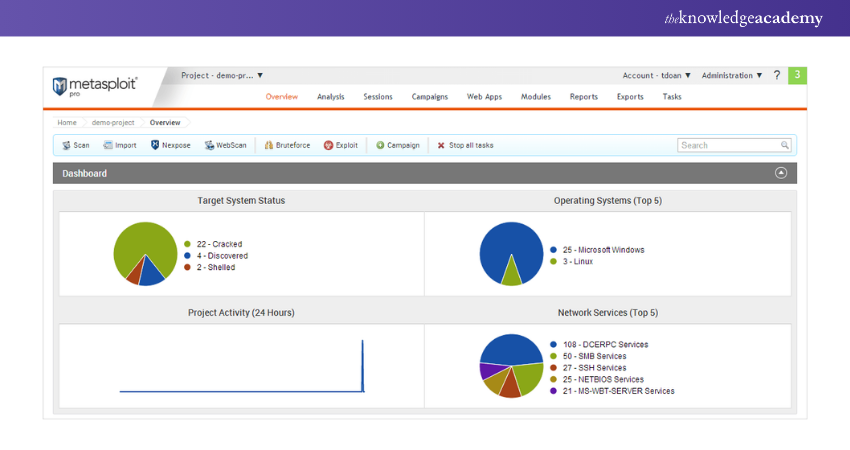
Features:
1) Cross-platform Support: Compatible with various Operating Systems.
2) Security Vulnerability Detection: Excellent for identifying security weaknesses.
3) Evasion and Anti-Forensic Tools: Ideal for creating tools to evade detection and counter forensic analysis.
Become a Metasploit pro and take your Cyber Security expertise to the next level with our Mastering Metasploit Framework Course – join now!
2) Wireshark
Wireshark is an excellent tool for analysing data packets and performing deep inspections of numerous established protocols. It allows users to export analysis results in various file formats, including CSV, PostScript, Plaintext, and XML. Wireshark is a powerful and versatile tool for network analysis and troubleshooting.
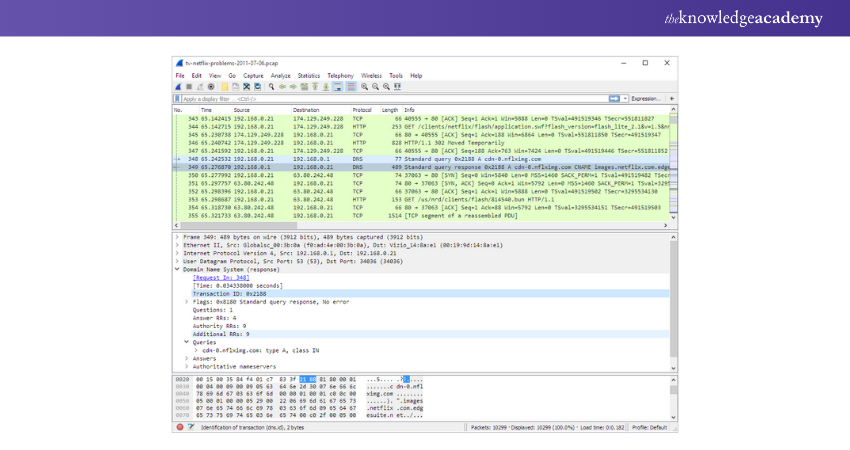
Features:
1) Live Captures and Offline Analysis: Capable of capturing data in real-time and analysing it later.
2) Cross-Platform Support: Compatible with multiple Operating Systems.
3) Customisable Colouring Rules: Facilitates analysis by allowing users to apply colouring rules to packet lists.
4) Pricing: Free to use.
3) John the Ripper
John the Ripper is one of the most popular and effective password crackers available. It is widely used for testing password strength on Operating Systems and for remote password auditing. This tool can auto-detect the encryption type of almost any password and adjust its testing algorithm accordingly, making it highly intelligent and efficient.
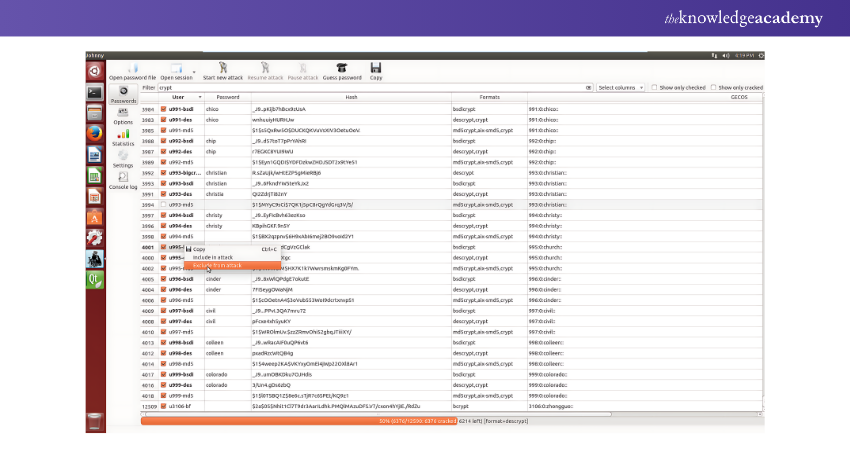
Features:
1) GPU Acceleration: Enhances the speed of password cracking.
2) Incremental Mode: Systematically tests password strength.
3) Community-contributed Rules: Utilises various attack strategies, including dictionary and brute force attacks.
4) Customisable: Supports multiple encryption algorithms for thorough password auditing.
5) Pricing: Free to use.
4) Burp Suite
Burp Suite is a comprehensive tool for web application security testing, widely used for scanning, crawling, and assessing web applications to detect and fix vulnerabilities.
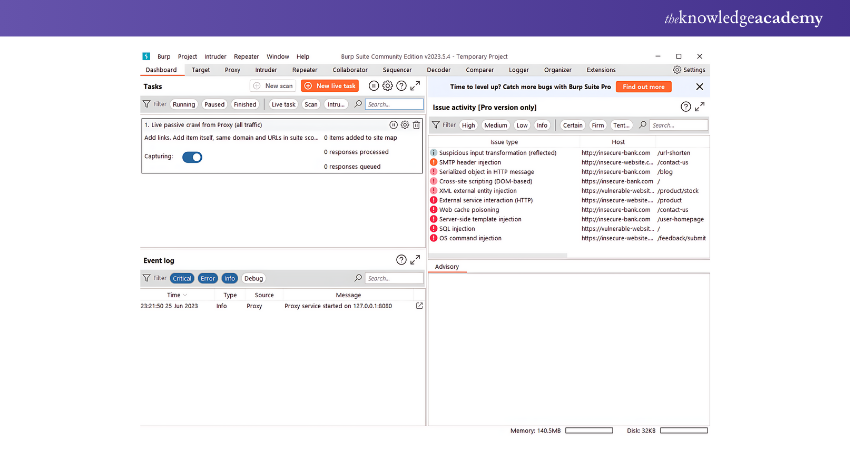
Features:
1) Proxy Functionality: Intercepts and modifies HTTP requests
2) Advanced Scanning Algorithms: Detects a wide range of web vulnerabilities
3) Collaborative Features: Facilitates teamwork in security assessments
4) Pricing: A paid version is available, with a free version offering basic features
5) Nmap (Network Mapper)
Nmap, short for Network Mapper, is a widely used reconnaissance tool in the Ethical Hacking community. It helps gather crucial information about target systems, guiding the next steps in penetration testing. Nmap is cross-platform, compatible with Mac, Linux, and Windows, and is renowned for its ease of use and powerful scanning capabilities.
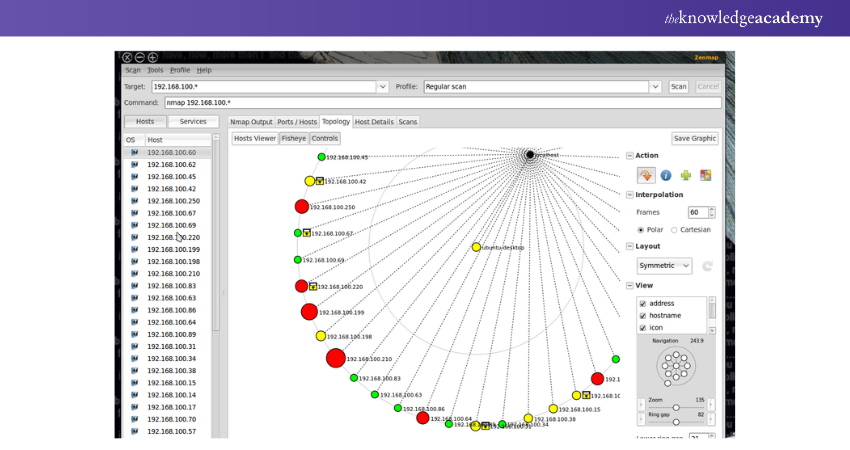
Features:
1) Device Security Auditing: Assesses the security of devices.
2) Open Port Detection: Identifies open ports on remote hosts.
3) Network Mapping and Enumeration: Maps and enumerates network structures.
4) Vulnerability Detection: Finds vulnerabilities within networks.
5) Massive DNS Queries: Executes extensive DNS queries against domains and subdomains.
6) Nikto
Nikto is a web scanner designed to identify outdated software, dangerous CGIs or files, and other issues on web servers. It performs both server-specific and generic checks, capturing received cookies. This free, open-source tool checks version-specific problems across 270 servers and identifies default programs and files.
Features:
1) Open-Source: Free to use and modify.
2) Comprehensive Scanning: Identifies over 6,400 potentially dangerous CGIs or files.
3) Version Checks: Detects outdated versions and version-specific issues.
4) Plugin and File Checks: Examines plugins and misconfigured files.
5) Security Identification: Finds insecure programs and files.
7) Kismet
Kismet is a top Ethical Hacking Tool for testing wireless networks and hacking wireless LANs or wardriving. It passively identifies networks, collects packets, and detects non-beaconing and hidden networks through data traffic analysis.
Kismet functions as a sniffer and wireless network detector, compatible with various wireless cards and supporting raw-monitoring mode.
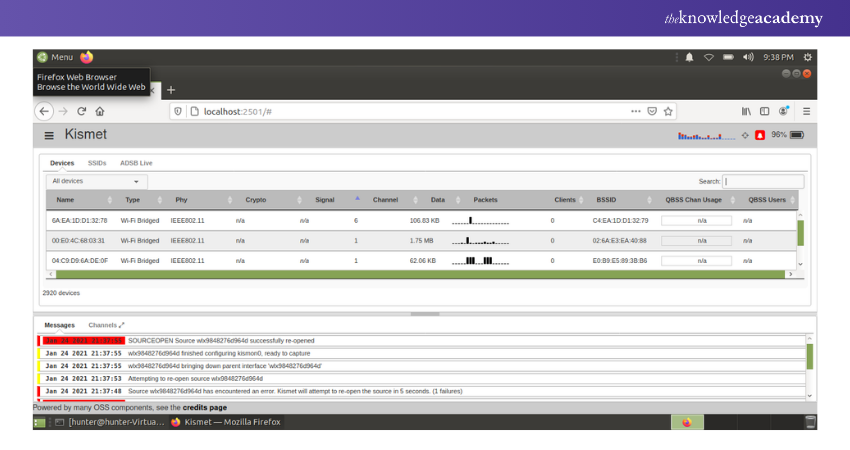
Features:
1) Linux Compatibility: Runs on Linux OS, including Ubuntu, Backtrack, and more.
2) Windows Support: Occasionally applicable to Windows.
8) Acunetix
Acunetix is a fully automated Ethical Hacking Tool that detects and reports over 4,500 web vulnerabilities, including all variants of XSS and SQL Injection. It supports JavaScript, HTML5, and single-page applications, making it ideal for auditing complex authenticated applications.
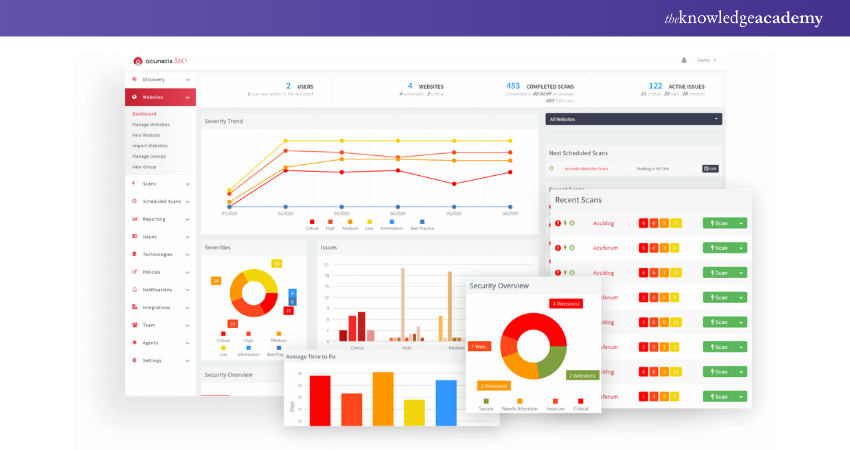
Features:
1) Consolidated View: Provides a unified view of vulnerabilities.
2) Integration: Integrates scanner results with other platforms and tools.
3) Risk Prioritisation: Prioritises risks based on data analysis.
9) OpenVAS
OpenVAS is an open-source vulnerability scanner that provides a comprehensive solution for identifying and managing computer security issues. It supports various network protocols and receives regular updates.
Features:
1) Configurable Scan Profiles: Allows for specific security assessments.
2) CVE Compatibility: Supports Common Vulnerabilities and Exposures.
3) Comprehensive Reporting: Offers detailed analysis through extensive reporting capabilities.
4) Pricing: Free to use.
10) Ettercap
Ettercap is a powerful tool for network sniffing and man-in-the-middle attacks. It allows for the interception, analysis, and modification of network traffic, making it invaluable for security assessments.
Features:
1) Real-time Connection and Session Management: Manages connections and sessions in real-time.
2) Protocol-specific Filters: Provides targeted analysis with specific protocol filters.
3) Plugin Support: Extends functionality through plugin integration.
4) Pricing: Free to use.
11) Maltego
Maltego is a highly effective open-source intelligence and forensics application designed for link analysis and data mining. It helps visualise complex relationships and discover connections across various data sources.
Features:
1) Graphical Representation of Data Relationships: Visualises complex data relationships.
2) Integration with Multiple Repositories: Connects with various data sources.
3) Custom Transforms: Extends functionality with custom transforms.
4) Pricing: Paid version available.
12) Hashcat
Hashcat is a robust password cracking tool that leverages GPU power for efficient password cracking. It supports a wide range of hashing algorithms commonly used in modern encryption.
Features:
1) Support for Multiple Hashing Algorithms: Includes MD5, SHA-1, bcrypt, and more.
2) Advanced Cracking Attacks: Utilises mask and rule-based password cracking techniques.
3) Session Restore: Allows resuming interrupted cracking attempts.
4) Pricing: Free to use.
13) Cain and Abel
Cain and Abel is a versatile password recovery tool that employs multiple methods, including dictionary and brute force attacks. It is renowned for its ability to recover passwords from network protocols and wireless networks.
Features:
1) Cryptanalysis Attacks: Targets various password hashes
2) ARP Spoofing: Sniffs passwords on local networks
3) Wireless Network Auditing: Assesses the security of wireless networks
4) Pricing: Free to use
14) Angry IP Scanner
Angry IP Scanner is a lightweight and user-friendly tool focused on IP address and port scanning. It is renowned for its fast and efficient discovery of active hosts on a network.
Features:
1) Multi-platform Support: Compatible with Windows, macOS, and Linux.
2) High-speed Scanning: Quickly scans IP addresses and ports to identify active hosts.
3) User-friendly Interface: Designed for users of all technical expertise levels.
4) Pricing: Free to use
Join our Cyber Security Awareness Course to stay informed and safeguard your digital world effectively and confidently!
Conclusion
Staying ahead of cybercriminals demands proactive measures, and Ethical Hacking Tools are your best allies. These powerful tools help identify and fix vulnerabilities, fortifying your digital defences. Master these tools to ensure your systems remain secure and resilient. Embrace the power of Ethical Hacking and safeguard your digital future.
Become a cyber guardian by learning Ethical Hacking through our in-depth and hands-on Ethical Hacking Training – sign up now!
Frequently Asked Questions

Careers in Ethical Hacking include roles such as Penetration Tester, Security Analyst, Cyber Security Consultant, Vulnerability Assessor, Security Engineer, Incident Responder, and Red Team Specialist. These professionals identify and mitigate security vulnerabilities to protect systems and data.

Hackers use various techniques, including phishing, malware, ransomware, brute force attacks, SQL injection, Social Engineering, DDoS attacks, and exploiting software vulnerabilities. These methods aim to gain unauthorised access, steal data, or disrupt systems.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Ethical Hacking Training, including Ethical Hacking Professional and Mastering Metasploit Framework. These courses cater to different skill levels, providing comprehensive insights into Ethical Hacker’s Roles and Responsibilities.
Our IT Security & Data Protection Blogs cover a range of topics related to Ethical Hacking, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your IT Security skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Ethical Hacking Professional
Ethical Hacking Professional
Thu 16th Jan 2025
Thu 6th Mar 2025
Thu 22nd May 2025
Thu 24th Jul 2025
Thu 25th Sep 2025
Thu 20th Nov 2025
Thu 18th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


