We may not have the course you’re looking for. If you enquire or give us a call on +61 1-800-150644 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

The history of Cyber Security dates back to the 1970s. During this time, terms such as worms, cyber theft, and viruses did not exist. However, such terms are becoming common in today's world due to increased cybercrimes. Cybercrime costs of organisations are expected to increase to 8.25 trillion GBP annually by 2025. Organisations are using Cyber Security measures to minimise these costs.
However, do you know how and why Cyber Security came into the picture? This blog will help you understand the history of Cyber Security and its current state. You will be able to learn about the following topics:
Table of Contents
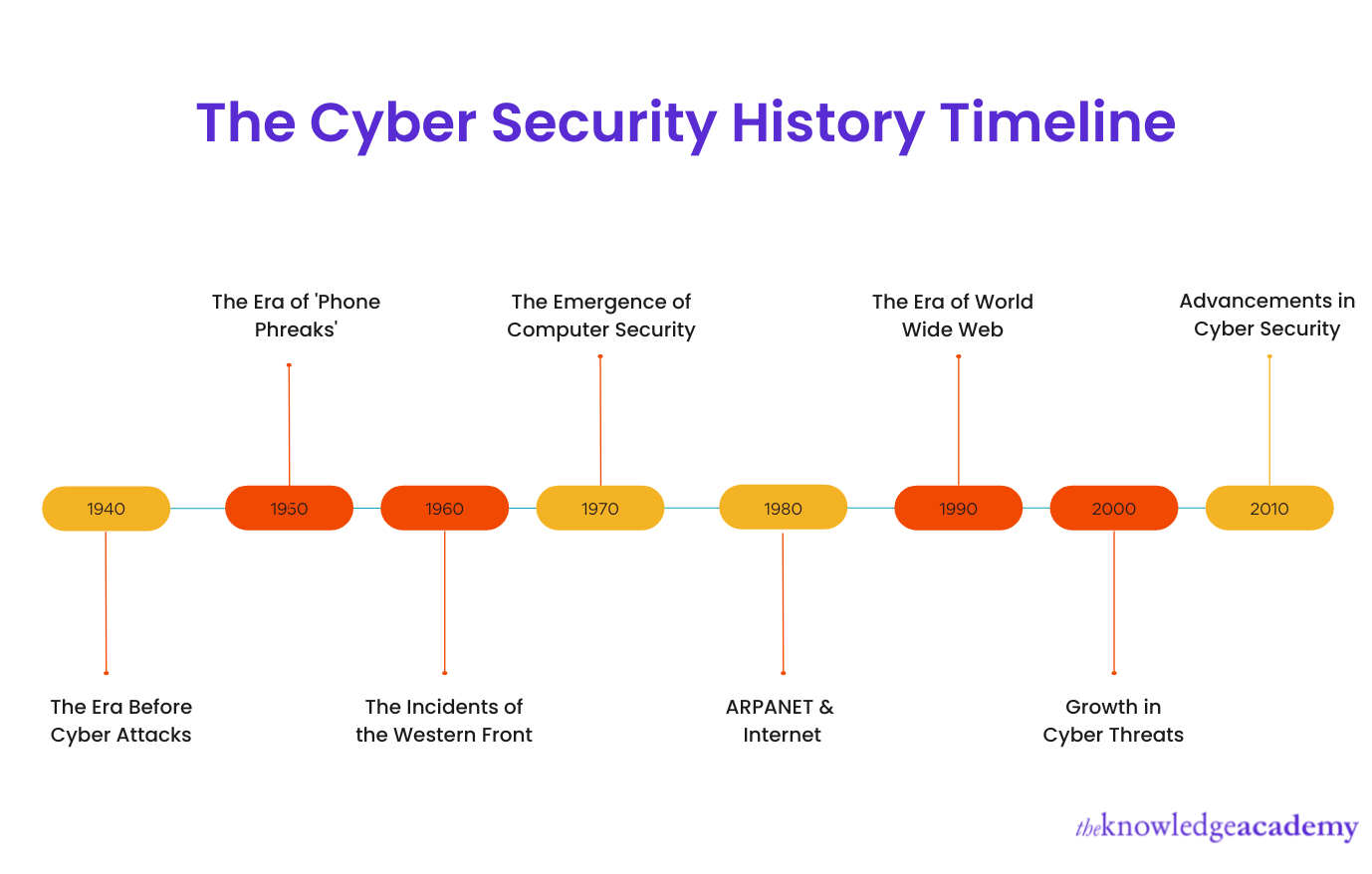
1) 1940s: The era before cyberattacks
2) 1950s: The era of ‘phone phreaks’
3) 1960s: The incidents of the Western Front
4) 1970s: The emergence of Computer Security
5) 1980s: ARPANET and Internet
6) 1987: The emergence of Cyber Security
7) 1990s: The era of the World Wide Web
8) 2000s: Growth in cyber threats
9) 2010s: Advancements in Cyber Security
10) The Future of Cyber Security
11) Conclusion
Do you want to learn how to reduce Cyber Security risks? Do it right away by signing up for the CCNA Cyber Security Operation Training!
1940s: The era before cyberattacks
Carrying out cyberattacks was complex for about two decades after introducing the world's first digital computer in 1943. Access to vast electronic machines was restricted to a few people as only a few knew how to use them, so the threat was almost non-existent. Interestingly, computer pioneer John Von Neumann initially proposed the idea of underlying computer viruses in 1949 when he proposed that computer programs can reproduce.
1950s: The era of “phone phreaks”
Early telephones share a technological foundation with computers in terms of the origins of hacking. “Phone Phreaks” first appeared in the late 1950s. The name refers to the techniques employed by "phreaks," or individuals keen on how phones function. They disrupted the protocols that permitted telecommunication experts to operate on the network remotely to place free calls and avoid paying long-distance charges.
Unfortunately for the phone companies, there was no way to stop the phreaks, and the practise gradually faded in the 1980s. The phreaks, which included pioneers in technology like Steve Wozniak and Steve Jobs of Apple, had grown into a community and even published newsletters. The stage was set for digital technologies.
1960s: The incidents of the Western Front
The Massachusetts Institute of Technology student publication published the first-ever reference to malicious hacking. Even by the middle of the 1960s, most computers were massive mainframes kept in temperature-controlled, safe environments. Access remained restricted, even for programmers, due to the high expense of these devices.
However, some people with access, frequently students, made early attempts at hacking. The attacks had no advantages at this point from a business or geopolitical standpoint. Most hackers were curious troublemakers or people looking to improve current systems by making them run faster or more efficiently.
Many large corporations invested in technologies to store and manage data and systems as computers became smaller and cheaper. Keeping them under lock and key became unnecessary as more individuals required access to them, and then passwords were introduced.
1970s: The emergence of Computer Security

With a research effort on ARPANET, the internet's forerunner (The Advanced Research Projects Agency Network), Cyber Security as we know it today, got its start in 1972. Creeper, a computer software developed by researcher Bob Thomas, could traverse the ARPANET network while leaving a breadcrumb trail wherever it went. 'I'm the creeper; catch me if you can,' it declared. The email was created by Ray Tomlinson, who also designed the program Reaper, which pursued and eliminated Creeper. Reaper was the first computer worm and the first self-replicating program. It was also the first instance of antivirus software.
As more businesses began to use the phone to establish remote networks, addressing these developing technologies' vulnerabilities became more crucial. Each connected piece of hardware created a fresh "entry point" to be secured.
Governments realised the importance of security as their reliance on computers and networking developed and that illegal access to data and systems might have disastrous consequences. The period from 1972 to 1974 saw a sharp rise in discussions on computer security, primarily in academic works.
The Ark, a computer at the Digital Equipment Corporation used for creating operating systems, was hacked by 16-year-old Kevin Mitnick in 1979, and copies of the software were generated. He was arrested and imprisoned for the first of several cyberattacks he would carry out over the following few decades. He now owns and operates Mitnick Security Consulting.
Take the Cyber Security Risk Management course to learn about modern cyberattack techniques.
1980s: ARPANET and Internet
The whole of the 1980s had seen a surge in cyberattacks. Hackers started invading the movie ‘War Games’ which portrayed a fictional story where a hacker uses nuclear weapon systems. With the increase of hackers and cybercriminals, people gradually started getting aware of “cyber” as a concept. The emergence of the internet and the gradual rise in technology usage made people understand its benefits.
One such malware which got public attention was the Vienna virus (a program that corrupts files on an infected device). Similar threats started emerging, but Vienna had gained particular importance by not what it did but how it was stopped.
In the mid-1980s, Bernd Fix, a German Cyber Security expert, discovered that the Vienna Virus infected his device. He, in return, coded a piece of antivirus software that helped find and remove the Vienna virus. This is known to be one of the first examples of modern antivirus software.
Commercial antivirus first appeared in 1987, despite conflicting statements about who invented the first antivirus product.
1990s: The era of the World Wide Web
The year 1990 witnessed the following events:
a) Polymorphic viruses were developed during this time. Polymorphic viruses were codes that reproduced themselves without altering the original algorithm. This made it hard to detect polymorphic viruses.
b) One of the British computer magazines, PC Today, published an edition including a free disc. This disc included a DiskKiller virus that infected numerous computers at a time.
c) European Institute for Computer Antivirus Research (EICAR) came into existence.
d) Microsoft introduced Internet Explorer with Windows 95, which remained the most widely used web browser for almost 20 years.
e) Computers became more affordable and widely available; this increased public awareness, and people could access the internet easily through private systems.
f) Users adopted email as a form of new communication and started using services like Microsoft Outlook, considered one of the rapid messaging services.
g) A virus started spreading through Outlook inboxes called Melissa virus, which came into existence in 1999. It started spreading rapidly in cyberspace, causing severe damage.
2000s: Growth in cyber threats
The 1990s laid the foundation for the modern internet, with its related dangers and security measures. However, the development of our modern cyberspace began in the 2000s. More households and companies worldwide had access to the internet, giving fraudsters more hardware and software vulnerabilities to take advantage of than ever before. Additionally, there was more to steal as data was being stored digitally on a larger scale.
A new method of infection emerged in 2001; users no longer needed to download files. Simply viewing an infected website was sufficient since malicious actors exchanged clean pages for infected ones or "hid" malware on trusted websites. Along with the attacks on instant messaging services were worms that spread through IRC (Internet Chat Relay) channels.
The dissemination of malware remained the primary objective of cybercriminals, and a new technique started to be deployed in the early 2000s and is still in use today. Email attachments drew heightened attention from users, and some email services even scanned files to look for security threats. Hackers recognised they could mislead users into leaving the comparatively secure environment of their email services and accessing a web page the hacker had set up to get around these barriers.
According to computer magazine c't, Zero-day threat detection rates fell from 40–50% in 2006 to barely 20–30% in 2007, as criminal organisations actively began to invest in professional cyberattacks.
2000: OpenAntivirus Project was the first available open-source antivirus engine.
2001: The first-ever open-source antivirus engine to be commercialised was ClamAV.
2001: Avast releases free antivirus software, providing everyone with an all-inclusive protection solution. I The effort increased Avast's user base in five years to more than 20 million.
Hacking of credit cards in the 2000s

Cyberattacks started becoming increasingly focused in the 2000s or the new millennium as they became known in popular culture. The first known instance of a series of data breaches aimed at credit cards occurred during this time. These started between 2005 and 2007 when Albert Gonzales created a cybercriminal group to arrange credit card systems. The group performed attacks that leaked confidential information from approximately 45.7 million cards.
This attack caused a giant retailer a loss amounting to £210.51 million. This led to the company keeping funds aside to compensate the affected victims. Gonzales was taken to prison and imprisoned for 40 years.
2001- CodeRed spreads through a buffer overflow when a program writes too much data to the "buffer" area of memory, resulting in a surge that overwrites adjacent memory addresses. As a result, the worm was able to infect additional computers and conduct focused DDoS (Distributed Denial of Service) attacks. This worm was lifeless; thus, traditional antivirus programs that examined files for malware failed to detect it.
2003- The newly created department of Homeland Security created the National Cyber Security Division, the US government's first official task force devoted to Cyber Security. It was established in response to the rising number of cyberattacks and a lack of power for prevention.
2007- When Apple introduced the iPhone, every user had access to a portable internet-connected computer that was more powerful than the one used to land Apollo 11 on the moon. Smartphones pose a severe Cyber Security risk since their vast number substantially expands the attack surface that hackers may exploit.
2010s: Advancements in Cyber Security
The 2010s saw many high-profile hacks and attacks that started to influence nations' national security and cost businesses millions of dollars. With the development of new cyber warfare methods, rising concerns over personal data privacy, and the enormous risks posed by corporate data breaches. The decade of the 2010s saw several significant changes.
2012: 2012 saw the online publication of more than 400,000 credit card numbers by the Saudi hacker 0XOMAR.
2013: Edward Snowden, a former CIA agent who worked for the US government, copied and disclosed sensitive data from the National Security Agency (NSA).
2013-2014: Three billion customers' accounts and personal information were compromised when malicious hackers entered Yahoo. Yahoo was later fined £28.60 million for failing to disclose the information.
2017: A ransomware called WannaCry infects 230,000 computers in one day.
2019: The New Zealand stock market had to be briefly shut down because of several DDoS attacks.
The disruption of Iran's nuclear program by a complex family of worms, which interfered with enriched uranium used for uranium enrichment, is regarded as the first instance of malware being weaponised on a large scale. It was one of the earliest cases of espionage-related cyberattacks.
Next-generation Cyber Security uses various techniques to boost the identification of new and unknown threats while reducing the frequency of false positives. Usually, it includes the following:
1) Multi-factor authentication (MFA)
2) Network Behavioural Analysis- using behavioural inconsistencies or abnormalities to detect malicious files
3) Threat intelligence and update automation
4) Real-time protection- also known as background guard, resident shield, on-access screening, and auto-protect
5) Sandboxing- developing a test environment that is isolated so you may run a suspicious file or URL
6) Forensics- attack replaying to assist security teams in effectively preventing future breaches
7) Back-up and mirroring
8) Web application firewalls (WAF)- preventing SQL injection, file inclusion, cross-site scripting (XSS), and cross-site forgery
Do you wish to discover threats and vulnerabilities before infiltration professionally? You can now sign up for the CompTIA Cyber Security Analyst CySA+ Certification course for expert training and assistance!
The privacy debate
When Russia and America inspected one other's cyber defences, a different conflict—the fight for online privacy—was starting to begin. Public awareness of data gathering increased in the early 2010s. Companies like Facebook and Google were gathering massive amounts of customer data. They used it to target advertising on their platforms or sold it to outside advertisers.
Internet users now purchase apps and other software products to protect their online privacy. Search engines and browsers that prioritise privacy were becoming more popular. The use of VPNs has become prevalent. People started to understand for the first time that they could limit the data-gathering tactics of large corporations rather than waiting for ineffective governments to interfere.
The Future of Cyber Security
It is not unexpected that there were many high-profile security breaches throughout 2020 across various industries. Cyber Security started becoming a problem for many organisations, and things started worsening in terms of growth due to massive data breaches. Organisations could not eliminate the danger of a cyberattack, but they started using various evolving technologies and procedures to ensure minimal risks.
The special discipline of Cyber Security will keep developing as technology develops at an increasing rate. Because of this, Cyber Security will keep evolving and getting more complex. To continue to be successful, businesses must be ready for unavoidable future improvements. The demand for qualified experts in the area and the emergence of new prospects make the future of Cyber Security careers extremely bright. It's time for IT workers to think more deeply about Cyber Security and adapt to the new changes in the technological environment.
Conclusion
Cyber Security offers many benefits: cybercriminals and businesses have fewer chances of getting hacked if they properly implement Cyber Security policies. Businesses should focus on having a well-built security system to detect and prevent attacks. Hope, this blog has given you insights into the Cybersecurity history along with a detailed understanding of Cyber Security history timeline.
You can register in Cyber Security Training courses to improve your Cyber Security skills helping you advance your career in the field of Cyber Security.
Frequently Asked Questions
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 17th Jan 2025
Fri 7th Mar 2025
Fri 23rd May 2025
Fri 18th Jul 2025
Fri 12th Sep 2025
Fri 12th Dec 2025







 Top Rated Course
Top Rated Course




 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


