We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

ISO certified organisations attract better opportunities and embed trust among their users. This is one of the reasons why careers in ISO are in high demand. If you want to start your career in ISO and seek knowledge about the ISO 27001 Interview Questions, you are at the right place. In this blog, you will learn the top ISO 27001 Interview Questions and answers to help you get started in the growing domain of ISO.
Table of Contents
1) Basic ISO 27001 Interview Questions
2) Intermediate ISO 27001 Interview Questions
3) Advance ISO 27001 Interview Questions
4) Conclusion
Basic ISO 27001 Interview Questions
The following basic Interview Questions on ISO 27001 will help you understand the concepts and definitions to gain a thorough understanding of ISO 27001:
1) Define what is ISO 27001.
ISO 27001 is an international standard which helps organisations safeguard sensitive information by systematically addressing the possible threats from an Information Security standpoint. This standard outlines the requirements for creating, implementing, and managing an Information Security Management System (ISMS) within an organisation.
2) What is the motive of ISO 27001?
The primary motive of ISO 27001 is to keep the information and data of an organisation safe. It provides a framework for organisations to protect information assets, manage security risks, and comply with industry-specific regulations. The guidelines and rules under ISO 27001 Access Control Policy help organisations identify and fix security risks such as cyberattacks and data breaches, ensuring a robust framework for safeguarding sensitive information.
ISO 27001 protects the confidentiality and integrity of the information assets, which include sensitive data, systems, processes, and more. Getting certified in ISO 27001 Standards can help the organisation avoid potential threats, ultimately building a strong and secure operating organisational model.
3) What do you mean by ISMS?
Information Security Management System, also known as an ISMS, is a systematic approach that helps an organisation manage and protect its information assets. This approach includes various relevant policies, procedures, and technical measures designed to protect the organisation from threats like unauthorised access, data breaches, and cyberattacks.
The goal of the ISMS is to promote a culture of responsibility and security within the organisation. ISMS helps employees at all levels, including the top management professionals, to stick to the guidelines, ensuring the organisation’s interests and industry regulations are in balance.
4) What is Annex A of ISO 27001?
Annex A of ISO 27001 is a detailed list of controls under the ISO 27001 Standard. Organisations can select the specific control or objective they want to achieve to protect and secure Information Security. There are 14 categories of controls, each addressing a specific aspect of Information Security.
Annex A provides a detailed framework to select and implement controls based on the needs and interests of the organisation. Some of these controls include A.5 Information Security Policy, A.6 Organisation of Information Security, A.7 Human Resource Security, and more.
5) What does Risk Assessment in ISO 27001 Standard mean?
Assessment in ISO 27001 is a fundamental process that helps in identifying, evaluating, and managing Information Security risks within an organisation. The goal of carrying out a Risk Assessment is to systematically identify significant threats, vulnerabilities, and the impact of security incidents on an organisation’s Information Security.
This process also enables organisations to make informed decisions about how to protect their assets, allocate resources and ensure the availability of data. This process basically includes five steps: identification, evaluation, mitigation, acceptance, and monitoring.
Intermediate ISO 27001 Interview Questions
These intermediate ISO 27001 Interview Questions will help you achieve a comprehensive understanding of the key concepts of ISO 27001:
6) What do you mean by ISO 27001 audit?
An ISO 27001 audit is an independent examination of the organisation’s ISMS to assess its compliance with the ISO Standard guidelines. The main focus of an ISO audit is to evaluate the effectiveness of an organisation’s Information Security controls and practices. It ensures that the organisation meet the specified standards that are adequate to secure sensitive and crucial information.
7) Which industries can benefit from the ISO 27001 Standard?
ISO 27001 Standard is widely accepted by a wide range of industries across the globe. Although the principles and requirements for Information Security management are not industry-specific, organisations can adapt to specific controls based on their industry’s needs and regulations. Some of the industries which highly rely on the ISO Standards are:
a) Healthcare industry
b) Finance and Information Technology (IT) industry
c) Government and Public sector
d) Manufacturing and Retail industry
e) Transportations and Logistics industry
8) What are the key principles of Information Security?
The key principles of Information Security are commonly referred to as the CIA Triad, which represents the fundamental goals and objectives of effective Information Security management. The CIA Triad stands for Confidentiality, Integrity, and Availability. These core principles guide the organisation to establish robust practices and frameworks to protect its data and systems from various threats and risks. Here’s what the Triad comprises of:
a) Confidentiality: This principle emphasises the protection of data from unauthorised access. It ensures that the data is accessed by those who are authorised to it or on a need-to-know basis.
b) Integrity: The integrity principle makes sure that the data and system in the organisation are reliable and accurate.
c) Availability: This principle focuses on the availability of information and data within an organisation.
9) Differentiate between ISO 27001 and ISO 27002.
ISO 27001 is an international standard which outlines the requirements for establishing and maintaining ISMS in an organisation. On the other hand, ISO 27002 is a guideline and best practice used to implement specific security controls within the ISMS. Following is a detailed differentiation between the two:
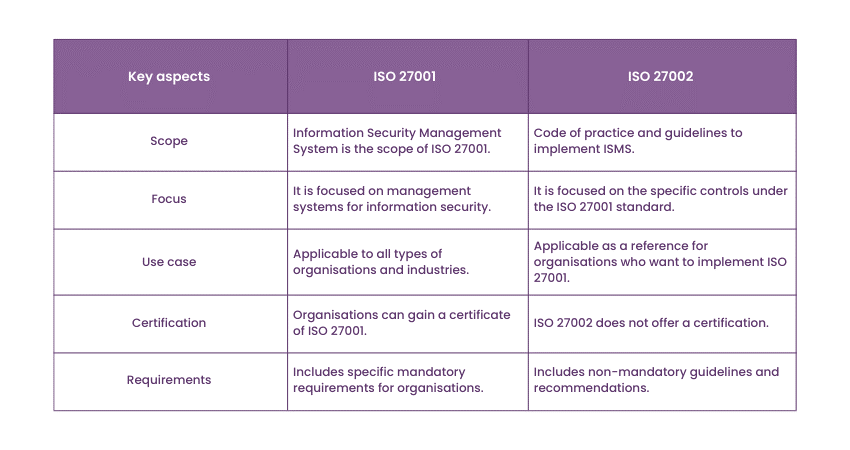
10) Explain the role of Lead Auditor and Lead Implementer.
The role of a ISO 27001 Lead Auditor is to evaluate the organisation’s ISMS and make sure that it is aligned with the ISO 27001 Standard guidelines. Lead Auditor are external to an organisation and conduct an independent audit to assess and recommend areas of improvement. They are also responsible for planning audits, coordinating with audit teams, conducting assessments, and reporting findings to management.
The role of a Lead Implementer is to deal with the internal aspects of ISO 27001 implementation in an organisation. A Lead Implementer is responsible for planning, implementing, and managing the ISMS compliance to meet the ISO 27001 Standards effectively. They play a vital role in implementing ISMS in daily operations and prepare the organisation to attain the ISO 27001 Certification.
Secure your business by registering for our ISO 27001 Training for comprehensive insights into Information Security management.
Advance ISO 27001 Interview Questions
Let us now discuss some of the advanced ISO 27001 Interview Questions and answers to help you gain an advanced understanding of the topics related to ISO 27001:
11) List down the steps involved in implement ISO 27001.
ISO 27001 implementation is an ongoing process which demands commitment and dedication. It includes several key steps to successfully implement the ISMS within an organisation:
Step 1: Define the scope of implementation
Step 2: Build an implementation plan
Step 3: Initiate the implementation process
Step 4: Establish an Information Security policy
Step 5: Define the Risk Assessment procedure
Step 6: Document the ISMS process
Step 7: Implement the controls
Step 8: Monitor and review the performance
Step 9: External standard audits
Step 10: Certification
12) Explain the role of security metrics in monitoring ISO 27001 Compliance and Risk Management.
Security metrics play a crucial role in monitoring ISO 27001 Compliance and effectively managing Information Security threats. Security metrics like access reviews and password policy provide measurable data points into their security posture to effectively implement ISMS and risk management strategy.
Security metrics enable organisations to make informed decisions throughout the lifecycle of implementing and managing the ISO 27001 Standard. By using security metrics, organisations can strengthen their security policies and enhance their ability to protect sensitive information.
13) What strategies can organisations employ to align ISO 27001 with GDPR?
ISO 27001 and General Data Protection Regulation or the GDPR align with each other to ensure compliance with both data security and privacy requirements. Some of the strategies to successfully align ISO 27001 with GDPR are:
a) Identifying a common ground: Organisations need to identify the areas where ISO 27001 and GDPR overlap. Risk assessment, data classification, access control, incident reports, etc., are some of the common areas addressed by both ISO 27001 and GDPR.
b) Data mapping and inventory: It is a crucial strategy to implement necessary controls. Creating a data inventory helps in identifying where data is stored, processed, and transmitted.
c) Risk Assessment: Conducting a combined Risk Assessment for both Information Security risks and data protection risks will help prioritise the activities and allocate resources.
d) Data Protection Impact Assessment (DPIAs): Performing DPIAs for high-risk potential activities as instructed by GDPR guidelines and integrating these activities for ISO 27001 to conduct risk management processes.
14) What are the challenges and best practices for conducting penetration testing within the ISO 27001 framework?
Penetration testing is a crucial component of assessing an organisation’s Information Security and identifying vulnerabilities. However, there are common challenges to conducting penetration testing with the ISO 27001 framework:
a) Scope definition: Organisations need to determine which systems, applications, and assets will be tested and are required to be aligned with the ISMS scope of ISO 27001.
b) Resource allocation: ISO 27001 Penetration Testing required professional testers and resources. Allocating these resources and finding a professional tester might be challenging for organisations.
c) Documentation: Documenting is a time-consuming task. It includes the documentation of penetration testing activities, findings, and the progress of the suggested solution under ISO 27001 Compliance.
d) Adaptation: To address these challenges, organisations need to adapt to some of the practices to successfully implement ISO 27001 and attain a certification.
e) Clear Scope: Clearly define the goals of the penetration test to ensure it aligns with the ISO 27001 ISMS scope. Document the system, applications, and assets to be tested. Organisations need to set clear goals on industry-specific goals.
f) Qualified testers: Engaging with certified and experienced penetration testers will help the organisation save time and use resources efficiently. Ensuring that the tester understands both ISO 27001 Compliance and industry-specific regulations.
g) Documentation: Keeping a record of the penetration testing process, including objectives, methodologies, findings and suggested solutions from day one, will reduce the burden of documenting all the changes at once.
15) List some advantages of implementing ISO 27001.
ISO 27001 has numerous advantages in an organisation, from securing private data to continuously improving the security structure of the organisation. Some of the key advantages of implementing ISO 27001 are as follows:
a) ISO 27001 helps organisations establish a robust framework to improve Information Security from risks of data breaches, cyberattacks, and other potential threats.
b) ISO 27001 helps in accommodating various data protection laws, regulations, and industry-specific standards.
c) ISO 27001 Certification builds customer and stakeholder trust and confidence in the organisation.
d) ISO 27001 enables an organisation to build effective incident response plans and procedures that help in faster and more efficient responses to security incidents.
Conclusion
ISO 27001 is a well-trusted and reliable standard to address Information Security within an organisation. It offers good opportunities for individuals and organisations to enhance their expertise in managing Information Security. We hope that this blog helped you gain a comprehensive understanding of ISO 27001 Interview Questions and answers to start your career in ISO and become a certified professional.
Unlock the power of ISO 27001 with our ISO 27001 Foundation Course. Sign up now for expert-led training!
Frequently Asked Questions
What are the Other Resources and Offers Provided by The Knowledge Academy?

The Knowledge Academy takes global learning to new heights, offering over 3,000 online courses across 490+ locations in 190+ countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 ISO 27001 Foundation
ISO 27001 Foundation
Mon 12th May 2025
Mon 7th Jul 2025
Mon 1st Sep 2025
Mon 10th Nov 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


