We may not have the course you’re looking for. If you enquire or give us a call on +65 6929 8747 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Security threats are on a constant rise. This makes it crucial for organisations to deploy the right tools for protection. Here comes ISO 27001 and SOC 2 to the centre stage, the two premier frameworks in information security. But what sets them apart, and which is right for your needs? Let’s explore this blog to uncover these differences and empower you to choose between ISO 27001 and SOC 2 for a robust compliance strategy.
Table of Contents
1) Understand What is ISO 27001 and SOC 2?
2) Key Differences Between ISO 27001 vs SOC 2
3) Key Similarities Between ISO 27001 vs SOC 2
4) Which One Is Right for You Between ISO 27001 vs SOC 2
5) How to Become ISO 27001 Compliant?
6) How to Become SOC 2 Compliant?
7) Conclusion
Understand What is ISO 27001 and SOC2?
ISO 27001 (also known as ISO/IEC 27001) is a set of standards for an Information Security Management System (ISMS). These standards or requirements represent the most suitable practices for Information Security Management in an organisation. ISO 27001, the Latest Version, provides security across several assets, such as financial information, employee data, intellectual property, and third-party data. ISO 27001 emphasises three key aspects of data security: availability, confidentiality, and integrity. The framework was formulated jointly by the International Electrotechnical Commission (IEC) and the International Organisation for Standardisation (ISO).
On the other hand, Service Organisation Control 2 (SOC 2) describes the organisational controls based on five key principles established by the American Institute of Certified Public Accountants (AICPA). These principles are security, availability, processing integrity, confidentiality, and customer data privacy. Collectively, these principles form a comprehensive framework for data protection.
SOC 2 compliance is divided into two main types: Type 1 and Type 2. Type 1 verifies an organisation’s use of compliant systems and processes at a specific time in contrast to Type 2 that attests compliance over a fixed time.
A Type 1 report typically incorporates all the security controls an organisation uses and attests to their proper design and enforcement. While, a Type 2 report includes everything in a Type 1 report, along with verification that these controls are effective in operation.
Key Differences Between ISO 27001 vs SOC 2
There is a plethora of differences between ISO 27001 and SOC 2. These differences are described in the below sections:
1) Scope
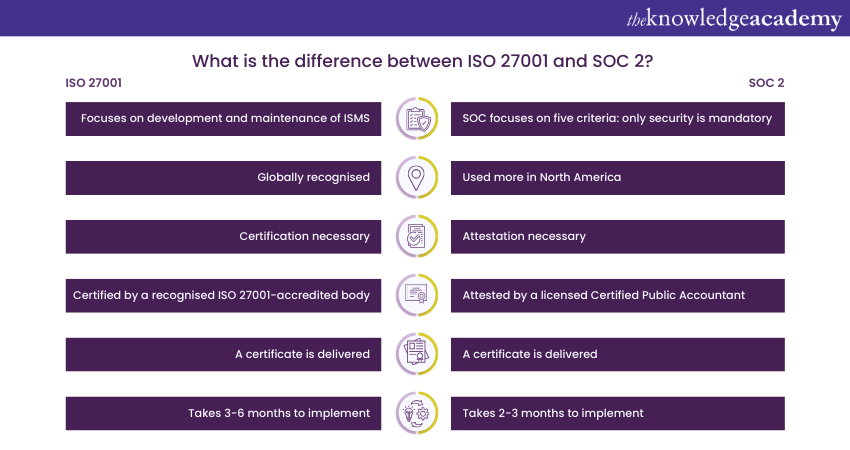
The primary difference between ISO 27001 and SOC 2 lies in their scope. Both frameworks include security control procedures along with their processes, policies, and technologies to protect sensitive data. Based on the recent studies, they share 96% of the same security protocols; however, their implementation approaches differ.
ISO 27001 focuses primarily on maintaining and developing an Information Security Management System (ISMS), to provide a structured approach to managing information security. Moreover, to complies with ISO 27001, organisations must implement security controls, conduct risk assessments, and review their effectiveness regularly. On the other hand, SO offer more flexibility. It consists of five trust service criteria: availability, processing integrity, security, privacy, and confidentiality. Of all these five criteria, only security is important. Organisations have the option to implement internal controls related to other principles.
2) Market Applicability
The market applicability should play a crucial role in your decision to choose between ISO 27001 and SOC 2. While both frameworks have global recognition, SOC 2 is more associated with North America. Conversely, ISO 27001 is a global standard and is more prevalent outside North America.
3) Certification vs Attestation
One of the key differences between the standards is that SOC reports are not generally considered certifications. Since SOC examination services are conducted under the AICPA attestation standards, they are classified as attestation reports. Attestation reports offer an independent auditor's opinion on an organisation's control environment, while a recognised body grants certifications. For SOC 2, the attestation focuses on an organisation's internal controls to meet vital criteria such as security, availability, processing integrity, confidentiality, and privacy. Conversely, an organisation receives certification if its ISMS conforms to the ISO 27001 global standard.
4) Certification/Attestation Process
To achieve certification or attestation under either framework, an external audit is required. However, the process differs in terms of who conducts the audit. For ISO 27001, an accredited certification body must attest to it. On the other hand, for SOC 2 attestation, it can only be performed by a licensed Certified Public Accountant (CPA).
5) External Deliverables
Another notable difference between the two standards is the type and content of external deliverables. The final external deliverable for SOC 2 is a verification report, which includes a service organisation audit result, a statement of the service organisation's management, and a detailed policy description. This description of the organisation details five key components of the system under review: infrastructure, software, people, processes, and data. In addition, the report will include appropriate organisation-level policies and fiduciary service metrics, associated controls, and test results from the auditor's testing.
On the other hand, the external deliverable for ISO 27001 is a one or two-page document that contains relevant information pertaining to the engagement. These include certified organisation’s ISMS scope, in-scope locations, standard certified against, date issued, and date of expiration. Reports are issued at the conclusion of each stage (stage 1, stage 2, surveillance audits, and recertification reviews). However, these reports are primarily for internal use and are not intended as external deliverables, unlike SOC 2 reports.
6) Project Timeline
Once the external audit is completed, both ISO 27001 and SOC 2 certifications can be obtained. The certification process is similar for both frameworks, consisting of three stages. The first stage involves a gap analysis to identify areas of improvement and for the organisation to define its ISO 27001 physical security objectives. The second stage requires the organisation to identify and implement appropriate security controls based on its needs. This step also involves the documentation of practices and the establishment of a method to review and improve processes. The final stage is an internal audit to identify and rectify any issues.
After completing all three stages, an organisation can contact a certification body to arrange for an ISO 27001 or SOC 2 audit. Although the certification process is similar for both frameworks, the time required for implementation varies. The duration typically depends on the work needed to meet the standards. Implementing SOC 2 usually takes two to three months, whereas ISO 27001 can take three to six months.
Another critical distinction is that SOC 2 implements security controls to protect customer data. At the same time, ISO 27001 requires establishing an operational Information Security Management System (ISMS) and the implementation of specific ISO 27001 controls.
Become an expert in ISO 27001 by signing up for our ISO 27001 Certification!
Key Similarities Between ISO 27001 vs SOC 2
Despite many differences, ISO 27001 and SOC 2 additionally have many similarities. Both ISO 27001 and SOC 2 are vital for agencies aiming to evaluate and enhance their data security towards industry standards. It covers important aspects of records protection, together with confidentiality, availability, and integrity.
In reality, those frameworks can paintings effectively in tandem, as they overlap in more than one area and can be carried out together. ISO 27001 allows companies to build an ISMS, at the same time as SOC 2 guarantees the improvement and evaluation of statistics security.
Both certification/attestation approaches require an independent assessor to affirm that the controls meet the Trust Service Principles (TSP) standards (SOC 2) and fashionable requirements (ISO 27001). Additionally, both standards are globally applicable and gain firms with an international presence. Compliance with either popular is valuable for constructing purchaser and marketplace trust.
Obtaining certification in one or both standards sends a positive message to investors and consumers about your company's security posture. Owing to the substantial overlap between the two frameworks, achieving certification in one can help one get closer to fulfilling the requirements of the other. While neither framework is required, achieving SOC 2 certification might assist an organisation in realising many advantages related to ISO 27001 standards.
Become an ISO 27001 Lead Auditor with our comprehensive ISO 27001 Lead Auditor Training – Register today!
Which One Is Right for You Between ISO 27001 vs SOC 2?
This section of the blog will describe the different scenarios and needs for which you should choose either ISO 27001 SOC 2 or a combination of both.
When to Choose ISO 27001?
Choosing between ISO 27001 and SOC 2 depends on your compliance needs and requirements. You will be better suited to opt for ISO 27001 if you are looking to fulfil the following needs:
a) Global Compliance Needs: Attaining certification in a single or both standards gives traders and clients reassurance concerning your agency's protection posture. Because the two frameworks have lots in common, becoming certified in a single lets you get towards pleasurable requirements for the opposite. Getting SOC 2 certified might assist an organisation in realising numerous ISO 27001 benefits even though neither framework is required.
b) Comprehensive Information Security Management: ISO 27001 addresses data safety holistically, addressing people, tactics, and generation. Employ this stage to create an integrated management gadget that includes continuous development, criminal compliance, and hazard management.
c) Third-Party Assurance: ISO 27001 certification demonstrates your commitment to facts security to customers, companions, and regulators. If your stakeholders require tangible proof of your security features, ISO 27001 Certification can offer the warranty they want.
When to Choose SOC 2?
The selection between ISO 27001 and SOC 2 depends broadly to your compliance desires and requirements. Choose SOC 2 if it satisfies the following necessities:
a) Industry-Specific Requirements: SOC 2 is critical for generation and cloud computing organisations. If your commercial enterprise handles sensitive purchaser facts, consisting of in Software as a Service (SaaS) or records hosting, SOC 2 compliance ensures you meet industry-particular standards.
b) Trust and Transparency: SOC 2 focuses majorly on controls related to security, availability, processing integrity, confidentiality, and consumer records privacy. This approach offers your clients the much-wanted warranty to beautify agreement and transparency between you and your clients.
c) US Market Focus: SOC 2 is regularly the preferred choice for corporations operating mostly within the United States, where stringent statistics safety standards are essential.
When to Choose Both?
You might be higher desirable to opt for a aggregate of ISO 27001 and SOC 2 if you are seeking to fulfil the following wishes:
a) Diverse Client Base: If your business caters to a various purchaser base with various compliance requirements, obtaining both ISO 27001 and SOC 2 certifications might be vital. This twin certification method showcases your dedication to assembly both worldwide and industry-unique requirements, thereby accommodating the numerous desires of your customers.
b) Enhanced Security Posture: Integrating ISO 27001's complete framework with SOC 2's centred cognizance on patron records creates a sturdy safety posture. This twin technique not only adheres to generalised safety standards but also meets the specific demands of your industry, accordingly, offering more desirable protection against capability threats.
Unlock the expertise to ensure robust Information Security – join our ISO 27001 Internal Auditor Training and safeguard your organisation with confidence!
How to Become ISO 27001 Compliant?
Becoming ISO 27001 compliant requires scientific technique and a will to strong Information Security practices. Firstly, set up a clean framework outlining your protection goals, guidelines, and methods. Conduct a thorough ISO 27001 to identify threat evaluation to capability vulnerabilities and determine their effect. Create and enforce comprehensive protection controls and measures to mitigate those dangers effectively.
Engage personnel at all tiers, making sure they are aware of their roles and responsibilities regarding Information Security. Regular education and focus programmes are critical. Establish a technique for tracking, analysing, evaluating, and assessing your security processes.
Additionally, conduct internal audits to identify areas for improvement and compliance gaps. Seek certification from an approved certification frame, which involves a final evaluation of your compliance with the ISO 27001 Standard. Continuous development is key; regularly assess your security features and adapt them to emerging threats and changing business desires, ensuring a persistent and evolving commitment to Information Security.
How to Become SOC 2 Compliant?
Achieving SOC 2 compliance is a meticulous system that requires cautious making plans and rigorous implementation of security features. To emerge as SOC 2 compliant, companies need to comply with a dependent method. Begin with an intensive inner evaluation to become aware of capability vulnerabilities and areas for improvement. Then, increase and put in force robust protection rules and tactics that align with SOC 2 necessities, specialising in facts protection, get admission to controls, and incident reaction.
Establishing a documented device for tracking and handling protection incidents is critical. Employee training and attention programmes are essential to ensure each person knows their position in retaining protection requirements. Engaging a qualified auditor skilled in SOC 2 assessments is important. They will conduct an independent assessment, trying your protection controls and methods.
Address any diagnosed weaknesses and refine your protection practices accordingly. Regular monitoring and continuous development are important; keeping SOC 2 compliance is an ongoing commitment to upholding excessive information security, which you should consider together with your customers.
Conclusion
All in all, both standards are efficient compliance efforts for organisations to undertake. Both ISO 27001 and SOC 2 can be used to gain a competitive edge over industry counterparts.
While SOC 2 is easier to implement and less expensive to maintain, it is also less rigorous. On the other hand, ISO 27001 is more rigorous and requires more work to be done, but it is more efficient in terms of protecting organisations from information security threats. While ISO 27001 and SOC 2 both have their differences, they also have their similarities, which enables them to work in tandem.
Secure your future in Cybersecurity with our ISO 27001 Foundation Training – your gateway to mastering Information Security Management Systems!
Frequently Asked Questions

SOX primarily focuses on financial reporting and corporate governance to protect investors, while SOC 2 targets data security to ensure service providers handle customer data carefully. Simply stated, both are important but serve different compliance needs.

SOC 2 certification isn’t mandatory but is highly recommended. It’s a valuable way to demonstrate your commitment to data security and build client trust. While not required by law, many businesses choose SOC 2 to fulfil industry expectations and gain a competitive edge.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various ISO 27001 Training Courses, including the ISO 27001 Foundation, ISO 27001 Lead Auditor, and ISO 27001 Internal Auditor Training. These courses cater to different skill levels, providing comprehensive insights into the Detailed Overview on ISO 27001 Gap Analysis.
Our ISO & Compliance Blogs cover a range of topics related to information security and regulatory standards, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your compliance and certification skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 ISO 27001 Foundation
ISO 27001 Foundation
Mon 10th Feb 2025
Mon 17th Mar 2025
Mon 12th May 2025
Mon 7th Jul 2025
Mon 1st Sep 2025
Mon 10th Nov 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


