We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203 999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
In today's digital landscape, where Cybersecurity threats continue to evolve and become more sophisticated, organisations need advanced tools and technologies to protect their sensitive data and infrastructure. One such innovative solution is Cognitive Threat Analytics, a cutting-edge approach to Cybersecurity offered by CISCO Systems.
But what miracles can this process do? How can it help mitigate cyber threats? Let's find out through this blog. In this blog, you will delve into exploring “What is Cognitive Threat Analytics?” You will also discover its essential features, advantages for customers, and its significance in the realm of Cybersecurity.
Table of Contents
1) What is Cognitive Threat Analytics?
2) Key features of CISCO Cognitive Threat Analytics
3) Advantages of Cognitive Threat Analytics
a) Decreased discovery time
b) Adaptive Security
c) Simple setup and upkeep
d) Enhanced visibility via cloud integration
4) Conclusion
Master IPv6 Protocols with These Essential Interview Questions! Prepare for Your Next IT Interview with Our Expert-Compiled IPv6 Questions and Answers!
What is Cognitive Threat Analytics?
Cognitive Threat Analytics is an innovative Cybersecurity solution manufactured and powered by Computer Information System Company (CISCO) Systems. It uses sophisticated algorithms, Machine Learning (ML) as well as Artificial Intelligence (AI) in predicting and preventing any attack on the data and network infrastructure of an enterprise.
In contrast to previous security systems, Cognitive Threat Analytics uses a more fluid and intuitive method for detecting threats. Therefore, it is always a step ahead of the development of Cybersecurity threats.
Key features of CISCO Cognitive Threat Analytics
The following are the key features of CISCO Cognitive Threat Analytics:

1) Autonomous threat detection
Autonomous threat detection, a pivotal feature of CISCO Cognitive Threat Analytics. It enables automated identification and response to potential threats without human intervention. The system uses advanced Machine Learning algorithms that have been set to monitor the network traffic in real time, being quick to detect any anomalies as they arise.
Through their capability of proactively analysing the patterns, autonomous systems guarantee robust threat mitigation, resulting in a reduced security breach risk. This attribute of early incident detection grants organisations an ability to remain proactive in response to emerging cyber threats. Moreover, organisations are armed with an improved resilience to deal with the constantly evolving online threats.
Embrace the future of connectivity – Upgrade to IPv6 today!
2) Symptomatic approach
Due to the event-based symptomatic method of Cognitive Threat Analytics, CISCO is rethinking the traditional way of threat detection and is looking at indicators of compromise instead of predefined rules. In contrast to the current standards which act on known signatures or patterns, they can detect an aberration inside the network and ignore its origin.
By means of anomaly detection, the technology would be able to identify any unusual patterns or data transfers. Therefore, it can help detect both known and unknown threats, providing organisations with a full range of Cybersecurity protection against sophisticated dangers.
Discover the Key Differences Between IPv4 and IPv6 - Upgrade Your Network Today!
3) Advanced Machine Learning algorithms for threat mitigation
CISCO Cognitive Threat Analytics utilises the capabilities of complex computational algorithms and AI to take Cybersecurity to the next plateau. The system does this by just-in-time analysis of masses of data and re-configuring itself to changing patterns of threats.
Thus, it is always one step ahead of cybercriminals. The platform utilises ML to uncover complicated patterns and breaches within the network, which in turn enhances proactive threat remediation. This upgraded practice enables businesses to face sophisticated cyber-attacks successfully making them more agile.
Improve your IPv6 skills with our IPv6 Basics Course - join today!
Advantages of Cognitive Threat Analytics
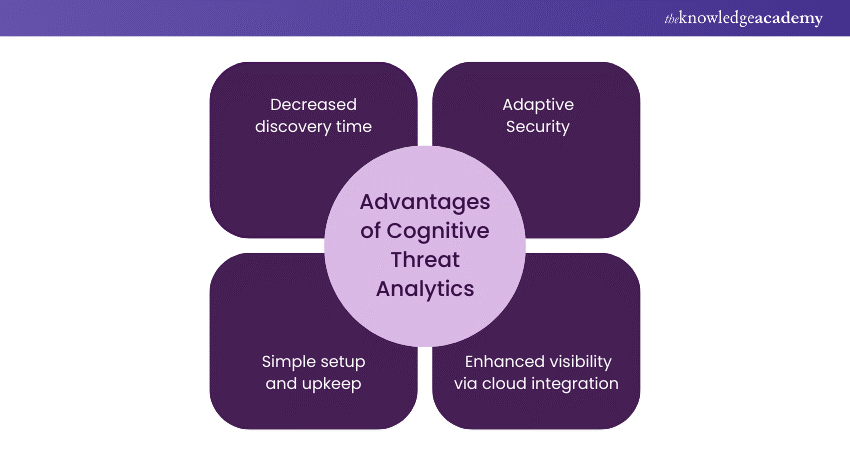
1) Decreased discovery time
Decreased discovery time is one of the major advantages offered by Cognitive Threat Analytics. Autonomous systems in the organisational IT architecture detect the threats. Through autonomous monitoring of network traffic and in-time analysis of the patterns, the smart system quickly identifies and addresses any security threats.
This reduces the time required for breach discovery and further curtails the period of organisational vulnerability. With Cognitive Threat Analytics in place, businesses can protect themselves from risks effectively, thus preventing or decreasing cyberattacks’ consequences on their operations and the integrity of the data.
Discover the Different Types of IPv6 Addresses and Learn How They Impact Your Network's Efficiency. Click to Explore!
2) Adaptive Security
Adaptability is the chief virtue of Cognitive Threat Analytics. It is the capacity to adjust and to be updated in response to Cybersecurity threats. Through advanced algorithms and Machine Learning, the system can improve itself from past errors and adapt its defensive techniques.
This adaptable approach guarantees that organisations are kept safe from continually unpredictable attacker techniques and those relating to continually changing tactics. Using Cognitive Threat Analytics, organisations will be able to continuously adopt a proactive position, a factor that will allow them to defend their data and infrastructure properly.
Improve your Cybersecurity knowledge with our CCNP Security Training - register now!
3) Simple setup and upkeep
Cognitive Threat Analytics powered by CISCO helps to establish a streamlined setup and maintenance process. This helps create one endpoint for Cybersecurity administrations. It is mostly instinctive and automated, so there is a lesser burden on the IT personnel.
Compared to other types of systems, the simple deployment procedures and minimal maintenance requirements ensure that organisations can carry out Cognitive Threat Analytics in a short span of time and without any time-consuming procedures.
The simplicity of the TCB principle not only helps to save time and resources, but also makes it possible for businesses to direct their efforts towards strategic initiatives while keeping vigorous Cybersecurity defences.
Discover the Key Advantages of IPv6 – Boost Your Network's Performance and Security Today!
4) Enhanced visibility via cloud integration
CISCO Cognitive Threat Analytics Enhanced visibility by integrating cloud technologies. By seamlessly integrating with cloud platforms, the system provides organisations with comprehensive insights into their Cybersecurity posture.
Through cloud-based analytics and monitoring tools, organisations gain real-time visibility into network activity and potential threats. This integration facilitates proactive threat detection and response, empowering organisations to stay ahead of evolving Cybersecurity risks while leveraging the scalability and flexibility of cloud technology for enhanced security management.
Ace Your Network Security Interview! Explore Top Network Security Interview Questions and Answers to Boost Your Confidence and Secure the Job!
Conclusion
CISCO Cognitive Threat Analytics represents a paradigm shift in Cybersecurity, offering autonomous threat detection, adaptive security measures, and streamlined operations. With its advanced features and efficient integration, it equips organisations to effectively mitigate evolving cyber threats. Thus, it helps safeguard their data and infrastructure in today's dynamic threat landscape.
Learn how to implement Cybersecurity best practices with our Implementing Advanced CISCO ASA Security - join now!
Frequently Asked Questions

Threat analytics is analysing data to identify Cybersecurity threats, using techniques like Machine Learning to enhance detection and response.

The four stages of threat analysis are Collection, Processing, Correlation, and Action.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various CISCO Training, including IPv6 Basics Course, CISCO Webex Teams Training and Introduction to CISCO Programmability Training. These courses cater to different skill levels, providing comprehensive insights into Cybersecurity Expert: A Beginner's Guide.
Our IT Infrastructure & Networking Blogs covers a range of topics offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your skills, The Knowledge Academy's diverse courses and informative blogs have you covered.
Upcoming IT Infrastructure & Networking Resources Batches & Dates
Date
 Administering Cisco Unified Communications Manager
Administering Cisco Unified Communications Manager
Mon 17th Feb 2025
Mon 21st Apr 2025
Mon 23rd Jun 2025
Mon 8th Sep 2025
Mon 24th Nov 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


