We may not have the course you’re looking for. If you enquire or give us a call on 800969236 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
- Retired : Designing and Implementing Enterprise-Scale Analytics Solutions Using Microsoft Azure and Microsoft Power BI DP500
- Microsoft Azure Administrator AZ104
- Data Engineering On Microsoft Azure DP-203 Certification
- Microsoft Azure Security Technologies AZ500
- Designing And Implementing Microsoft DevOps Solutions AZ400

Today, companies are moving from on-premises infrastructure to Cloud Computing as it is easy to access and manage. Out of the many options available in the market, Microsoft’s Azure has become one of the most popular Cloud platforms. Despite its benefits, some users hesitate to use Azure Cloud due to its security concerns. Thus, it’s crucial to understand Azure Security Best Practices for utilising this platform efficiently.
With such concerns about security, Statista has reported that 21 per cent of the files are not secured across the cloud. Users are looking for a Cloud platform that can offer a better security environment. However, by learning how to utilise tools and features of Azure, you can create, execute, and manage apps across cloud environments, and on-premises infrastructure. Want to know how this can be done? This blog will review the key Azure Security Best Practices that every company should adhere to to protect its assets and data.
Table of Contents
1) What is Microsoft Azure?
2) Working of Azure Security
3) 10 essential Azure Security Best Practices
4) What are Azure Security Tools?
5) Conclusion
What is Microsoft Azure?
Microsoft Azure is a Cloud Computing platform offering various computing, storage, and networking services. It is an open-source technology offering services to businesses, e-commerce, finance, or even tech giants. Azure provides four different kinds of Cloud Computing services:
a) Serverless functions
b) Platform as a service (PaaS)
c) Software as a service (SaaS)
d) Infrastructure as a service (IaaS)
Azure does not require upfront charges, and you do not have to wait long for resources and services. It is ranked second worldwide among popular cloud platforms like AWS, Google Cloud, and others. Azure protects data centres, manages applications, and charges only for the services you use. Due to these features, It is one of the most preferred cloud providers.
What is Azure Security?
Azure provides a wide range of cloud security services that can be modified to meet your requirements. The Azure services include data recovery, access control, data encryption for data in transit and at rest, and data monitoring all seamlessly integrated with Azure Pipelines for streamlined deployment and management processes. These services are compatible with both Windows and Linux.
Why should you consider it?
Many organisations store and access users' confidential information on a day-to-day basis. Using Azure, these organisations can ensure that no one can attack their business system, take over the controls, and gather confidential data.
Azure offers endless services to strengthen and secure your network. Azure will be the first line of defence in case of any security issue.
Moreover, it takes approximately 287 days to find and fix a breach. Organisations worldwide prefer Azure Security as a trustworthy cloud service provider to overcome all these.
Working of Azure Security
The operation of the Microsoft Azure Security infrastructure is demonstrated in the Azure Security document by a shared Security model. This implies that security is a collaborative effort between Azure and the customer, excluding the customer-only environments. Here is a list describing the separation of responsibilities in various Cloud service models:
a) Microsoft Azure handles the physical security of the host, network, and data centre within an IaaS
b) Azure handles the physical security and functionality within a PaaS. The service shares the identity and data infrastructure, manages networks and applications with its users.
c) Microsoft Azure also adopts many roles in operations, physical security and network management within a SaaS. It also shares information about its customers' sensitive data with them.
Train in Azure Security Platform with our Microsoft Azure Training!
15 Essential Azure Security Best Practices
Businesses can meet all their security needs with Azure infrastructure. It is developed from scratch to host millions of customers at once. Additionally, Azure offers a broad range of Security Controls that allow you to adjust your organisation's security needs and deployments. Azure supports all programming languages, operating systems, frameworks, and devices. Customers can use Azure's resources and services if they have an internet connection. However, one should know how to leverage its services and features properly. Here are the top 10 Azure Security Best Practices that you can implement to get the best out of this Cloud Computing Platform:
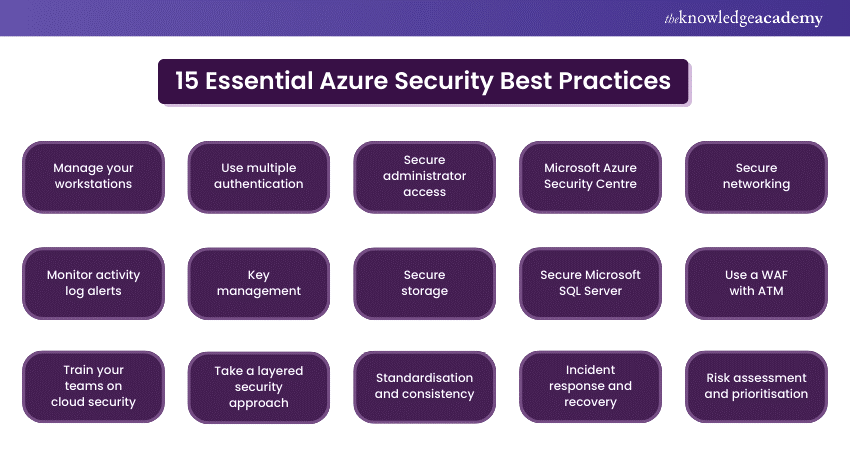
1) Manage your workstations
Individuals require regular access daily across the internet. Consider a situation where they have access to confidential information, and they are simultaneously gaining access to an unknown file from the open internet containing malware. The question then arises about how these unknown accessible files impact their business. The individuals may be easily targeted by hackers who aim to inject malware and gain unauthorised access to confidential data.
A sole solution in this situation would be to utilise workstations dedicated to handling the organisation's daily sensitive and normal tasks. Moreover, Microsoft provides users with Privileges Access Workstations or PAW in Azure, designed to offer complete protection to organisations from every possible security threat. The organisation can also utilise the dedicated workstation to manage its confidential data and administer Azure.
2) Use multiple authentication
It is generally a concern for an organisation’s security to strengthen its authentication process to restrict the actions of hackers from attempting any attacks such as phishing or brute force kinds. It is nearly impossible for any organisation to secure their system to perfection. However, they can work continually to strengthen their security forces gradually with each attempt.
A few fundamental measures now include setting complicated passwords comprising alphanumeric characters and special symbols, coupled with the functionality of Multi-Factor Authentication (MFA). Such security measures help fortify an organisation’s basic authentication process, strengthening it against security threats with time.
Furthermore, Microsoft Azure also offers organisations the flexibility and liberty to utilise their directory service known as the ‘Azure Active Directory’ or AAD. The AAD is built to safeguard its authentication process. It ensures that users accessing the Azure Active Directory administration must also enable their Multi-Factor Authentication and protect their data.
3) Secure administrator access
Organisations must evaluate Azure accounts given administrative privileges frequently at regular intervals.
They also need to remember to block any unnecessary access to such accounts. Now Privileged Identity Management (PIM) is a service of the Azure Active Directory that allows organisations to manage, analyse, and fully control security access throughout their organisation. Users can utilise this facility after a thorough activation process that grants them the rights of a system administrator for a limited time.
Organisations must also remember that identity is generally considered the primary parameter for assessing security levels. Microsoft Azure ensures optimal and industry-standard network security via measures such as core directory services, application access management, and identity protection into a unified solution.
Become a network traffic controller with our Designing And Implementing Microsoft Azure Networking Solutions AZ700 Course.
4) Microsoft Azure Security Centre
Microsoft offers organisations and individuals the Azure Security Centre as the optimal choice for planning, implementing and maintaining their security infrastructures. Though organisations incur an additional service cost to onboard security measures and further maintain their defences, it is ideal for them if industry-standard security is their top priority.
It will benefit them in real-time protection from security threats, Microsoft Defender ATP licensing, compliance benchmarking with Azure CIS and continuous scanning with CVE.
These security protocols help organisations monitor and analyse the configuration of their networks and hosted appliances. The Azure Security Centre essentially serves as a one-stop solution providing the organisation with all the recommendations and necessary suggestions to strengthen the security of their Azure accounts and workspaces.
Some of the key benefits of the Azure Security Centre include the following:
a) Traffic control by setting the configuration of the groups under Azure Network Security.
b) Protect web applications from security threats by providing Web Application Firewalls or WAFs.
c) Malware can be identified and removed by procuring anti-malware software services.
d) Fixing the configuration of the Operating System.
5) Secure networking
The systems and resources directly accessible across the internet are more vulnerable targets for security threats. Thus, it is crucial to ensure that such resources are secured, which can prevent any form of threat from affecting the other resources.
Such as Azure Virtual Machine, facilitating remote desktop connections for enhanced accessibility and collaboration.. With respect to Linux, the Secure Shell or SSH port is always open. Any open ports need to be completely restricted and securely locked to reduce and prevent any access from unauthorised sources or entities. Organisations must take note to always block ports 22, 3389, 5986 and 445, which are the most common ports leading to security attacks,
Furthermore, enterprises and organisations can use the Network Security Group, or NSG, under Azure to restrict access to networks except for any necessary access points. They must also enable firewalls wherever necessary.
Consider the example of the SQL Server Firewall system that is built to work outside an Azure NSG to help apply restrictions to the organisation’s Microsoft SQL Server access. In the case of an accidental misconfiguration in the NSG, the SQL firewall can save the incident and rectify the issues by conducting vulnerability scans for the infrastructure.
6) Monitor activity log alerts
Organisations can leverage their threat detection process with activity logs, where unrecognised events are detected before they can cause severe system problems. So, the enterprise can create activity log alerts which help notify them of security threats. Here are a few examples of such cases that can be deemed helpful for your system’s security infrastructure:
a) Modifications or changes in the network’s security solution, its policy and assignment.
b) Any changes in the Network Security Group, including its deletion.
c) Modifications, including deletions of the Network Security Group Rule.
d) Changes in the SQL firewall and its rules.
7) Key management
An organisation can encrypt its confidential information, such as passwords, into keys. Such keys are considerably secure and act as robust passwords for network security checks. Organisations must ensure that their keys are completely encrypted and carefully safeguarded to prevent any form of misuse and loss of keys.
The management of these security keys is a necessity for Cloud data protection. Now, Azure's key fault facilitates the storage of the organisation’s encryption and security keys in the hardware security modules (HSM). Microsoft processes its keys in the HSM according to the FIPS 140-2 Level-2 standard.
Enterprises can further monitor the usage of these security keys by sending the logs to the Security Information and Event Management or SIEM.
8) Secure storage
Storage security is a priority for any organisation that stores confidential and massive volumes of data. They work to eliminate any risk of data theft by restricting any unauthorised source from accessing data. For example, the disk encryption process uses the BitLocker service on Windows and DM-Crypt on Linux to encrypt the data drives and Operating Systems.
Furthermore, enterprises can configure their storage accounts to use blob encryption, secure transfer, and file encryption. They need to regularly update their security keys in their Azure Storage accounts and set a threshold on the use of Shared Access Signatures for the security of data transfers. Such transfers are also available for access to authorised entities for a few hours only.
9) Secure Microsoft SQL Server
The most common storage service utilised by most organisations is Microsoft SQL Server. An organisation can activate and monitor SQL Server’s firewall, and Azure can detect security threats and attacks. Now, such threats and attacks include SQL Injection, Man-in-the-middle attacks, and Phishing attacks, among others.
The organisation can further strengthen the security policy of its SQL Server firewall and monitor all security logs, information misuse, and any alerts of breaches.
10) Use a WAF with ATM
The Azure Web Application Firewall or WAF is a service that is designed and built atop the Application Gateway Service or AGS. It helps prevent Open Web Application Security Project or OWASP 3.0 attacks against databases in Azure SQL.
Moreover, an organisation can strengthen against attacks by ensuring its components are least accessible throughout the public internet. They can implement the geolocation filter under Azure Traffic Manager or ATM to help lock their web application if it does not require international access. More importantly, an organisation can also make its WAF accept traffic only when it is ready by using the ATM.
Microsoft Azure Security Technologies AZ500 Course can help you master Azure Security Best Practices – register now!
11) Train your teams on cloud security
Security is a joint undertaking in the cloud. Training your teams on cloud security accordingly is the goal of making sure they are aware of the subtleties of Azure's security features and the shared responsibility model. Conducting training sessions on a regular basis will help teams stay in touch with the newly identified security threats and the best methods for eliminating them. Thus, this involves acquainting yourself with the Azure infrastructure, using security tools effectively, and identifying potential weaknesses. Creating a culture of lifelong learning will equip organisations' teams to face incidents safely and develop proactive attitudes toward cloud security.
12) Take a layered security approach
A layering security approach, also called defence in depth, involves having different security controls at various levels of your Azure environment. This ensures that different types of security threats are safeguarded, from DDoS attacks to data breaches. Multiple security mechanisms like firewalls, intrusion detection systems, and data encryption form a solid security posture which evolves sufficiently in the face of new dangers. It’s essential to routinely and consistently check these layers of security for effectiveness against the recently released security threats.
13) Standardisation and consistency
Standardisation and replication of your cloud deployments can help increase security. It deals with the application of well-defined configurations, models, and managerial processes that aim to reduce complexity and the chance of human error. Consistent application of security controls and policies allows all Azure environment parts to be secured with the same rules. It reduces management complexity and makes it more convenient to audit and confirm compliance with regulatory requirements.
14) Incident response and recovery
Having a solid disaster recovery and detection plan which reduces the impact of any security breach is vital. The plan should encompass the measures to be taken in case of a breach, involving how to constrain the threat, assess the damage, and get back to normal operations. Regular drills and simulations will make the team be ready to decide and act promptly and efficiently. A recovery strategy with the use of backups and disaster recovery solutions will also help guarantee business continuity.
15) Risk assessment and prioritisation
Security strategies should include risk assessment and prioritisation as two main elements. It is a process of determining the most critical risks to your Azure deployment and ranking them by the damage potential. By discovering where the weaknesses exist, resources can be allocated more efficiently and redirected to areas that require more protection. This should be an ongoing process that includes periodic reviews to keep track of all new threats and assessments of your cloud environment.
Conclusion
If you have come this far, we are sure you understand the benefits of employing Microsoft Azure Security in your organisation. These 10 Azure Security Best Practices can help you start with Microsoft Azure Cloud security. To use Azure Security, you'll need technical and hands-on experience.
Gain an in-depth understanding of Azure SQL Solutions by joining our Administering Microsoft Azure SQL Solutions DP300 Course today!
Frequently Asked Questions

Azure Security measures streamline regulatory compliance through continuous assessments and a regulatory compliance dashboard, enhancing trust and enabling business expansion by meeting global standards.

Businesses can stay updated on Azure security threats and best practices by utilizing Azure’s operational security guidelines, which are regularly updated to reflect the current cybersecurity landscape.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Microsoft Azure Training, including Microsoft Azure Fundamentals AZ900, Microsoft Azure AI Fundamentals AI900 and Microsoft Azure Security Technologies AZ500 Courses. These courses cater to different skill levels, providing comprehensive insights into Azure Quantum.
Our Microsoft Technical Blogs cover a range of topics related to Microsoft Azure. offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Microsoft Technical skills, The Knowledge Academy's diverse courses and informative blogs have you covered.
Upcoming Microsoft Technical Resources Batches & Dates
Date
 Microsoft Azure Fundamentals AZ-900 Certification
Microsoft Azure Fundamentals AZ-900 Certification
Fri 3rd Jan 2025
Fri 2nd May 2025
Fri 4th Jul 2025
Fri 5th Sep 2025
Fri 7th Nov 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


