We may not have the course you’re looking for. If you enquire or give us a call on + 1-866 272 8822 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Reverse Engineering is a critical and intricate field, demanding a deep understanding of technology and analytical skills. A career in Reverse Engineering can be extremely rewarding, challenging one's ability to solve complex problems and innovate. Due to the specialised nature of this field, Reverse Engineering Interviews are known for their rigour and depth. But what if you had access to the Top 25 Reverse Engineering Interview Questions? Ready to conquer your Interview?
In this blog, we will explore the Top 25 Reverse Engineering Interview Questions with detailed answers. Let's dive in to learn more!
Table of Contents
1) Reverse Engineering Interview Questions and Answers
a) What is Reverse Engineering?
b) Why is Reverse Engineering necessary?
c) What is a disassembler?
d) Is it possible to Reverse Engineer an executable file without access to its source code? If yes, then how?
e) How does debugging come into play when performing Reverse Engineering?
f) What are the ethical issues that need to be considered when doing Reverse Engineering?
g) Can you give me some examples of how Reverse Engineering is used in real-world applications?
h) What's the difference between hardware and software Reverse Engineering?
i) What kind of tools do you use for Reverse Engineering?
j) What is obfuscation?
2) Conclusion
Reverse Engineering Interview Questions and Answers
In this section, we will look at the Top 25 Reverse Engineering Interview Questions and their corresponding answers. Whether you're a seasoned professional or new to the field, these insights will help you approach your Interview with confidence.
1) What is Reverse Engineering?
Reverse Engineering is a process where a product, device, system, or software is deconstructed to understand its workings in detail. It involves analysing something to discover how it functions or was made, often with the goal of learning from or improving upon it. Here are the steps involved in Reverse Engineering:
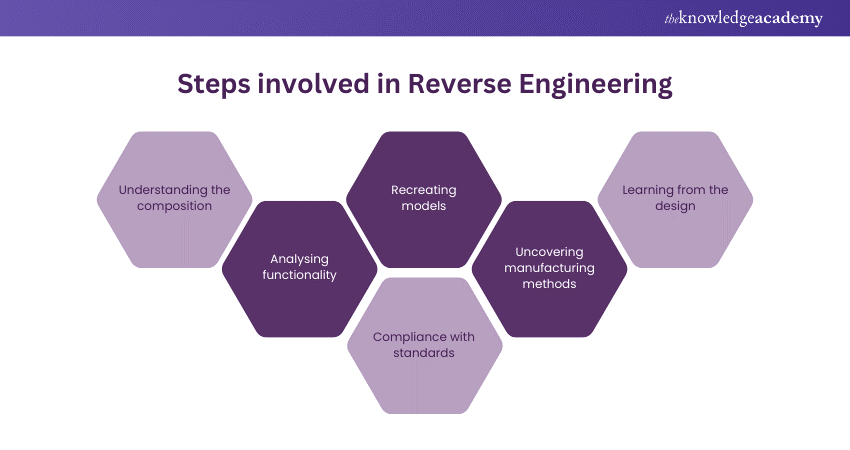
1) Understanding the composition: Reverse Engineering starts with understanding what the item is made of. For physical products, this could mean dismantling them to study their parts. For software, it involves examining the code, often in a compiled form.
2) Analysing functionality: The next step is to understand how the different components work together. In software, this might involve looking at how different functions interact or how data flows through the system. In hardware, it might mean studying circuit diagrams or mechanical interactions.
3) Recreating models: Often, Reverse Engineers try to recreate models or diagrams of the item being studied. This could be a schematic of a circuit board, a flowchart of software processes, or a 3D model of a mechanical device.
4) Discovering the manufacturing process: Understanding how something is made is a key part of Reverse Engineering. This can include techniques used in manufacturing a physical product or programming methodologies for software.
5) Learning from the design: The ultimate goal is often to learn from the original design. This could be to replicate the item, to build something compatible with it, or to improve upon the original design.
6) Compliance with legal and ethical standards: It's crucial to ensure that Reverse Engineering activities comply with legal and ethical standards, particularly regarding intellectual property rights.
Overall, Reverse Engineering is used in a variety of fields, from Software Development to Mechanical Engineering. It requires not only technical skills but also analytical thinking and attention to detail.
2) Why is Reverse Engineering necessary?
Reverse Engineering is necessary for understanding existing systems, enhancing or customising functionality, identifying vulnerabilities for security purposes, or for educational and research activities. It enables innovation and adaptation of technology.
3) What is a disassembler?
A disassembler is a tool used in Reverse Engineering to convert executable programs into assembly code. This helps in understanding the program's operations and logic when the source code is unavailable.
4) Is it possible to Reverse Engineer an executable file without access to its source code? If yes, then how?
Yes, it's possible to Reverse Engineer an executable file without its source code by using disassemblers and decompilers to translate the binary into a higher-level language, which can then be analysed and understood.
5) How does debugging come into play when performing Reverse Engineering?
Debugging is crucial in Reverse Engineering as it allows stepping through the code, examining variables, and understanding the logic and flow. It helps identify errors or points of interest in the software being reverse-engineered.
6) What are the ethical issues that need to be considered when doing Reverse Engineering?
Ethical considerations include respecting intellectual property rights, not using Reverse Engineering for malicious purposes, and adhering to relevant laws and regulations. Ethical practice is essential for maintaining professional integrity.
7) Can you give me some examples of how Reverse Engineering is used in real-world applications?
Here's how you can answer this question: "In my experience, Reverse Engineering is used to analyse competitors' products in the tech industry, to understand and improve cybersecurity by examining malware, and in digital forensics to uncover data from erased or damaged devices."
8) What's the difference between hardware and software Reverse Engineering?
Hardware Reverse Engineering involves analysing physical components and circuitry, while software Reverse Engineering focuses on understanding and replicating software algorithms, code, and functionality.
9) What kind of tools do you use for Reverse Engineering?
You can answer this question like this: "I primarily use tools like Ghidra for disassembling and decompiling, OllyDbg for dynamic analysis, and WireShark for network traffic analysis. These tools help me understand the software's operation and identify areas for improvement or vulnerability."
10) What is obfuscation?
Obfuscation is the technique of making software code or data hard to understand or analyse. It's often used to protect intellectual property or prevent unauthorised Reverse Engineering.
Accelerate your tech journey with our Advanced Technologies Courses – Sign up today!
11) What are some advantages of using Reverse Engineering?
From Software Development to Mechanical Engineering, Reverse Engineering offers several significant advantages across various industries. Let's take a look at some of them:
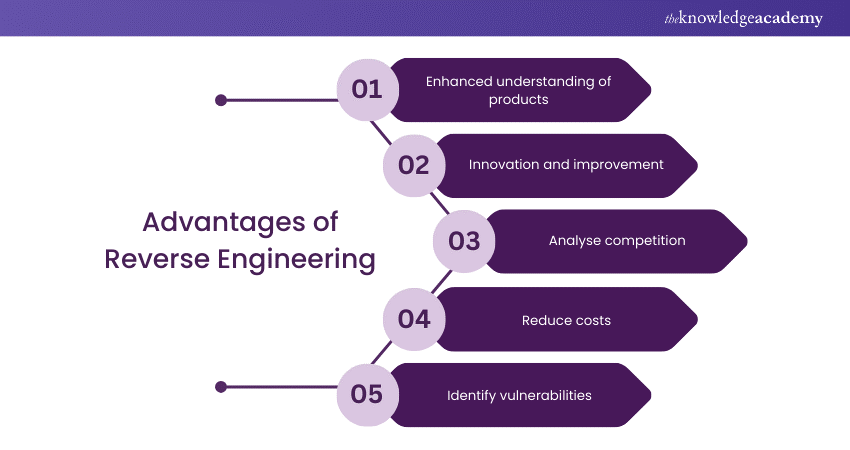
1) Enhanced understanding of products: Reverse Engineering allows engineers and developers to dissect and understand the inner workings of a product or system. This is particularly beneficial when dealing with legacy systems or products for which documentation is scarce or non-existent. By deconstructing and analysing these systems, one can gain insights into their design principles, operational mechanisms, and performance characteristics.
2) Innovation and improvement: One of the most significant advantages of Reverse Engineering is the opportunity it provides for innovation and improvement. By understanding how existing products or systems work, engineers can identify areas for enhancement, efficiency, or performance upgrades. This process often leads to the development of new, more advanced versions of the product or system, driving technological advancement.
3) Analyse competition: In industries where competition is fierce, Reverse Engineering can be a valuable tool for analysing competitors’ products. This analysis can reveal strengths and weaknesses in competitors’ designs, providing crucial insights that can be used to develop superior products and gain a competitive edge in the market.
4) Reduce costs: Reverse Engineering can also lead to cost savings. By understanding the intricacies of a product, companies can identify more cost-effective ways to manufacture or improve it. This might involve finding cheaper materials that don’t compromise quality, simplifying the design for easier production, or enhancing efficiency to reduce waste.
5) Identify vulnerabilities: In the realm of software and cybersecurity, Reverse Engineering plays a crucial role in identifying and patching vulnerabilities. By deconstructing software, security professionals can discover hidden backdoors, security flaws, or unintended features that could be exploited by malicious actors. This process is essential for strengthening the security of software products and protecting them against cyber threats.
Overall, Reverse Engineering offers substantial advantages in terms of gaining a detailed understanding, fostering innovation, competitive analysis, cost reduction, and enhancing security. These benefits make it an invaluable approach in various fields, including manufacturing, Software Development, and Cyber Security.
12) Can you explain the key difference between static and dynamic analysis?
You can answer this question like this, "Static analysis involves examining code without executing it, while dynamic analysis involves running the software and observing its behaviour, both essential for a comprehensive understanding of Reverse Engineering."
13) How do you approach Reverse Engineering in a time-sensitive scenario?
Here's how you can answer this question: In time-sensitive situations, I prioritise the most critical components, use automated tools for quick data gathering, and focus on the key functionalities to streamline the process.
14) How do you approach Reverse Engineering for a software update or patch?
You can answer this question like this: I conduct differential analysis to compare the old and new versions, which helps in understanding the changes, improvements, or fixes introduced in the update or patch.
15) How do you keep up with emerging trends and advancements in the field of Reverse Engineering?
Here's how you can answer this question: "I keep myself updated by following leading industry blogs, participating in online forums and communities, attending relevant workshops and conferences, and continuously experimenting with new tools and techniques in my projects."
16) Can you discuss a particularly challenging Reverse Engineering project you've worked on?
You can answer this question like this: "One challenging project I worked on involved Reverse Engineering a legacy banking system. It was challenging due to the lack of documentation and outdated technology, but through methodical analysis and collaborative teamwork, we successfully updated the system while retaining its core functionalities."
17) How do you approach collaboration and communication in a team during Reverse Engineering projects?
Here's how you can answer this question: "I emphasise open communication and regular status updates to ensure everyone is on the same page. Using collaborative tools like Git for version control and Slack for communication helps maintain a smooth workflow and ensures that all team members contribute effectively."
18) How do you handle situations where the source code is not available for Reverse Engineering?
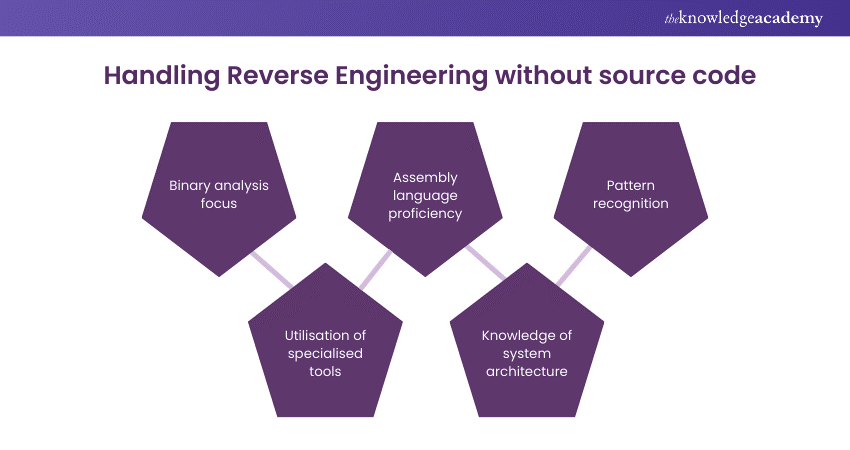
Here's how you can answer this question: "When the source code is unavailable, I focus on binary analysis. This involves using Reverse Engineering Tools like Radare2 for disassembly and Hex-Rays for decompilation. Understanding assembly language and system architecture becomes crucial in these scenarios to infer the functionality from the binary."
19) How do you approach Reverse Engineering for a new software application?
You can answer this question like this: "When Reverse Engineering a new software application, my approach includes a preliminary analysis to understand its architecture, followed by detailed examination using tools like IDA Pro and x64dbg. This helps me identify key areas for deeper analysis."
20) Describe your experience with Reverse Engineering for malware analysis. How do you approach identifying the malicious behaviour of an unknown software application and analysing its techniques for evasion or persistence? Share an example of a time you successfully identified and mitigated a malware threat through Reverse Engineering.
You can answer this question like this: "Debugging is pivotal in Reverse Engineering for understanding the runtime behaviour of applications. I use debuggers like GDB and WinDbg to step through code, analyse variable states, and track down how different parts of the program interact with each other."
Step into the realm of limitless possibilities with our Introduction to Virtualisation Technologies Training – Sign up now!
21) Can you provide insights into your experience with hardware Reverse Engineering?
Here's how you can answer this question: "In my hardware Reverse Engineering projects, I've dealt with diverse electronics, from consumer gadgets to industrial machinery. My focus is on circuit board analysis, component identification, and signal tracing, often requiring meticulous inspection and testing."
22) How do you handle situations where you encounter legal or ethical dilemmas during Reverse Engineering?
Here's how you can answer this question: "In situations involving legal or ethical dilemmas, I always err on the side of caution. I consult with legal experts to understand the implications and ensure compliance with laws and regulations. Ethical practice is paramount, so I avoid any actions that could be considered invasive or infringing on intellectual property."
23) How do you handle situations where you have limited information about the software you are trying to Reverse Engineer? What strategies do you employ to gather additional information and overcome challenges associated with limited data?
You can answer this question like this: "A particularly challenging project involved Reverse Engineering a proprietary communication protocol. It required extensive network analysis and trial-and-error to understand the protocol's structure and develop a compatible interface for our application."
24) Describe your experience with automating tasks in the Reverse Engineering process. What tools and techniques do you use to automate tasks, and how has this improved your efficiency and accuracy?
Here's how you can answer this question: "I believe in leveraging the diverse skills of the team, so I encourage specialisation while maintaining a broad understanding of the project among all members. Regular meetings, clear documentation, and using collaborative platforms like JIRA for task management are key strategies I employ."
25) Explain the importance of obfuscation in Reverse Engineering.
Obfuscation is important as it adds a layer of protection against unauthorised Reverse Engineering. It makes understanding the code more challenging, thus safeguarding intellectual property and enhancing security.
Conclusion
We hope you read and understand everything about Reverse Engineering Interview Questions and their corresponding answers. Mastering these questions not only prepares you for job Interviews but also deepens your understanding of this complex and fascinating field. Remember, continuous learning and practical application are key to success in Reverse Engineering.
Unravel the secrets of technology with our Reverse Engineering Training – Sign up now!
Frequently Asked Questions

Success in a Reverse Engineering Interview requires a blend of technical skills, including proficiency in programming languages like C and Python, familiarity with tools like IDA Pro and Ghidra, and a solid understanding of assembly languages. Additionally, strong analytical and problem-solving abilities, along with keen attention to detail, are crucial for analysing and understanding complex software systems.

Preparation for a Reverse Engineering Interview involves thorough practice with common Interview Questions, staying updated with the latest industry trends and technologies, and hands-on experience with Reverse Engineering projects. Additionally, reviewing fundamental concepts in computer science and software Engineering and practising problem-solving and analytical thinking can significantly enhance your readiness for such Interviews.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, blogs, videos, webinars, and Interview Questions. By tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

Discover Advanced Technologies Courses with The Knowledge Academy, offering Reverse Engineering courses, Virtual Reality training, and LTE Fundamentals training. Designed for diverse skill levels, these courses provide a comprehensive understanding of Advance Technologies methodologies.

The Knowledge Academy’s FlexiPass is a prepaid training voucher that is built specifically for clients and their dynamic needs. It provides access to various courses at a pre-determined price, with robust safety measures. FlexiPass gives clients the added benefit of upskilling on a budget that best fits them.
Upcoming Advanced Technology Resources Batches & Dates
Date
 Reverse Engineering Training
Reverse Engineering Training
Fri 17th Jan 2025
Fri 21st Feb 2025
Fri 4th Apr 2025
Fri 6th Jun 2025
Fri 25th Jul 2025
Fri 7th Nov 2025
Fri 26th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


