We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Proxies are a helpful tool that can provide additional security for your computer. These are configured as web filters or firewalls, which can help safeguard your device against internet threats such as malware. This extra layer of security becomes even more valuable when used with a secure web gateway or other email security products. With this setup, you can filter traffic based on its level of safety or your network's capacity to handle traffic, making your online experience safer and more secure.
But What is a Proxy Server? Fret not for the following blog will help you answer the question. A Proxy Server is an intermediary between a client device and a destination server on the internet, forwarding requests and relaying responses to the client. Read this blog to gain an understanding of What is a Proxy Server.
Table of Contents
1) Understanding What is a Proxy Server?
2) How does a Proxy Server operate?
3) What are the types of Proxy Servers?
4) Benefits of a Proxy Server
5) Conclusion
Understanding What is a Proxy Server?
A Proxy Server is a crucial intermediary between clients and servers. It manages and regulates client requests for specific resources or services on a server. Different types of Proxy Servers are utilised based on the purpose of the client's request.
The primary goal of these servers is to ensure that the direct connection between the client and the server remains secure. Proxy Servers hide the client's IP address when they request other servers, ensuring anonymity and privacy, which is a necessary part of cyber security.
a) Internet client and Internet resources: Proxy Servers serve as an intermediary between Internet clients and servers, effectively shielding the internal network from requests made by clients to access data stored on the server. Doing so helps keep the client's original IP address hidden while accessing data from the server, ensuring greater security and privacy.
b) Protects true host identity: A Proxy Server is one method to mask outgoing internet traffic. A Proxy Server works as a mediator between the user's device and the internet, making it appear that the traffic is coming from the Proxy Server. This method requires configuration for specific applications, such as HTTP or FTP. Organisations can utilise a Proxy Server to monitor their employees' internet traffic to increase productivity and efficiency. Additionally, it can be used to prevent highly confidential data leakage. Some even use it to boost their website's search engine ranking.

How does a Proxy Server operate?
Each device that connects to the Internet is allocated a distinctive Internet Protocol (IP) address, which acts as its digital "street address." Just as the postal service delivers mail to your physical address, the internet uses IP addresses to route data to the correct device.
A Proxy Server can be an intermediary between your device and the web server you request information from. This intermediary server has an IP address your device recognises, allowing it to funnel your web requests through the Proxy Server first. The proxy then transmits your request to the web server, collects the response, and sends the web page data back to your device so you can view it in your browser.
But a Proxy Server can do more than pass information along. It can also modify the data you send while delivering the expected results. For instance, a Proxy Server can mask your IP address, making the request appear to be coming from a different location. It can also encrypt your data so it is unreadable to anyone who might intercept it in transit. A Proxy Server has the capacity to block access to specific websites based on IP addresses, helping to enhance security and control access.
Ready to dive into the world of Cyber Security? Try our Cyber Security Risk Management Course now!
What are the types of Proxy Servers?
Regarding Proxy Servers, several different types are available, each with its unique features. These proxies provide users with an alternative internet address to use. Knowing the details of each proxy type will help you make an educated judgment based on your specific needs and use case.
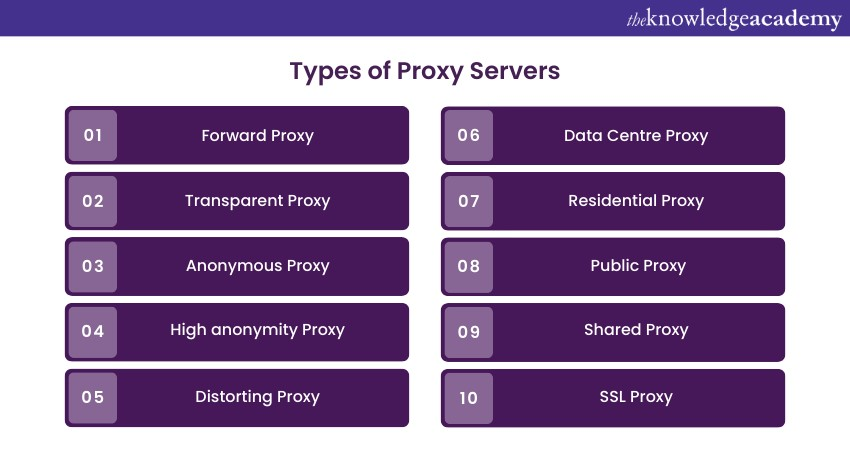
1) Forward Proxy
It is a server between clients and the internet and is utilised to obtain data from groups of users within an inner network. When a request is transmitted, the Proxy Server reads it to determine whether it should create a connection.
Forward proxies are best suited for internal networks that require a single-entry point. They provide IP address security for those within the network and allow for straightforward administrative control. Using a forward proxy may limit an organisation's capacity to cater to the requirements of particular end-users.
2) Transparent Proxy
Transparent proxies are Proxy Servers that can provide users with a seamless and identical experience to what they would have if they were using their home computer. This makes it "transparent" to the user. Users can also be connected to a transparent proxy without their knowledge, known as a "forced" connection.
Transparent proxies are particularly useful for companies that want to use a proxy without informing their employees. The key benefit of using a transparent proxy is that it provides a seamless user experience. However, transparent proxies are more vulnerable to specific security threats, such as SYN-flood denial-of-service attacks.
3) Anonymous Proxy
Anonymous proxies are used to make internet activity untraceable. When users access the internet through an anonymous proxy, their identity and computer information are hidden. It is the best option for users who want complete anonymity while accessing the internet. Anonymous proxies have some drawbacks. Many people view them as underhanded, and users may face pushback or discrimination. Users should be aware that anonymous proxies could cause potential issues despite their benefits.
4) High anonymity Proxy
A high anonymity proxy provides an additional layer of anonymity by removing your personal information before connecting to the target site. This benefits users who require high anonymity, such as employees who do not want their online activities traced back to their organisation. It is important to note that some free high anonymity proxies may be decoys set up to collect users' personal information or data.
5) Distorting Proxy
A distorting proxy is a Proxy Server that conceals its identity while identifying itself as a proxy to a website. It achieves this by changing its IP address to an incorrect one.
Distorting proxies are an ideal choice for those who wish to browse the internet while keeping their location hidden. They can make it appear as if you are accessing the web from a specific country, thus offering the benefit of concealing your identity and that of the Proxy Server. It ensures that your personal information is kept secure even when associated with the proxy. Some websites may automatically block distorting proxies, preventing users from accessing the websites they need.
6) Data Centre Proxy
A corporation provides data centre proxies through a data centre and is not affiliated with the user's internet service provider (ISP). When a user makes a request, it is routed through the Proxy Server in the physical data centre. These proxies are a great option for quick response times and an affordable solution.
They are also ideal for quickly gathering intelligence on an individual or organisation, allowing users to harvest data inexpensively and efficiently. It is important to note that data centre proxies do not offer the highest level of anonymity, which may put users' information at stake.
7) Residential Proxy
Residential proxies provide an IP address associated with a specific physical device. All the online requests you make are then routed through that device.
Residential proxies are flawless for users who must confirm the ads displayed on their website. This helps block cookies suspicious or unwanted ads from competitors or bad actors. Compared to other proxy options, residential proxies are more reliable. They are usually more expensive, so users should carefully evaluate whether the benefits outweigh the extra cost.
8) Public Proxy
Public proxies are available to everyone at no cost. They allow users to access websites while hiding their IP address, thus preserving their anonymity. Public proxies are most suitable for people prioritising cost over security and speed. They are often slow due to the many free users. Using public proxies increases the risk of having one's information accessed by third parties online.
9) Shared Proxy
When using shared proxies, multiple users have access to the same IP address, allowing you to scan the internet from a location of your choice. Shared proxies are a good option for those with a limited budget and do not require a high-speed connection. The main benefit of a shared proxy is its affordability. Since multiple users access the same IP, you may get penalised for someone else's actions, which could lead to your account being banned from a website.
10) SSL Proxy
A Secure Sockets Layer (SSL) proxy provides a decryption layer between the client and the server. This means the data is encrypted in both directions, and the proxy remains hidden from the client and server.
SSL proxies are ideal for organisations that require enhanced protection against potential threats that may be revealed or stopped by the SSL protocol. Additionally, Google prefers SSL servers, so using an SSL proxy with a website may improve its search engine ranking. Contents that are encrypted on an SSL proxy cannot be cached. As a result, when you visit a website multiple times, you may encounter a slower rendition.
Benefits of a Proxy Server
Following are the reasons why organisations and individuals use a Proxy Server:
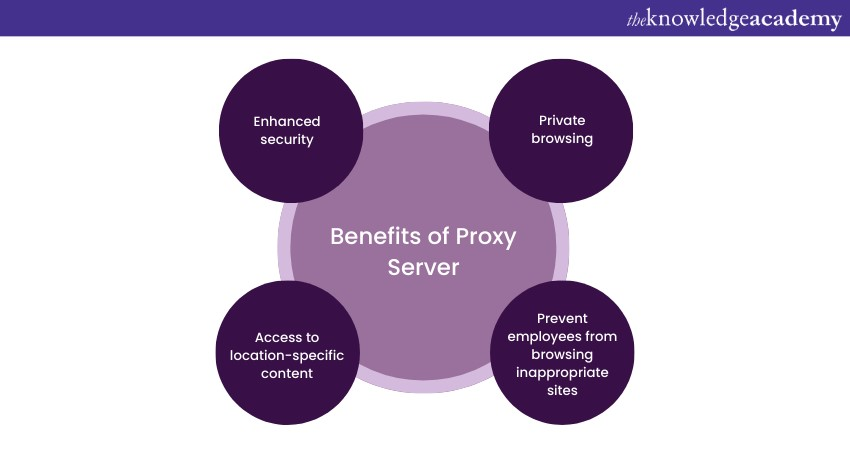
a) Enhanced security: It can act like a firewall between the internet and your system, preventing hackers from quickly accessing your IP address and infiltrating your computer or network.
b) Private browsing: If you want to maintain your privacy while browsing, watching, listening or shopping online, it is highly recommended that you use different proxies. By doing so, you can avoid being bombarded with unwanted ads or having your IP-specific data collected. With the help of a proxy, your site browsing activity becomes well-protected and impossible to track, confirming that your private details stay safe and secure.
c) Access to location-specific content: If you want access to location-specific content unavailable in your country, you can use a Proxy Server with an associated address from another location. This will make it appear that you are accessing the content from that location and allow you to enjoy full access. For example, you can access location-restricted websites by using the local IP address of the location you want to appear in.
d) Prevent employees from browsing inappropriate sites: To maintain a productive work environment, it is essential to prevent employees from accessing inappropriate or distracting websites. By implementing website blocking measures, you can ensure that your employees are not visiting sites that conflict with your organisation's principles or values. Additionally, you can restrict access to websites known as time-wasters and distractions, such as social media platforms like Facebook. These steps can help employees stay focused and on-task, leading to a more efficient and effective workplace.
Ready to explore the world of Cyber Security? Explore our comprehensive Cyber Security Training today!
Conclusion
In conclusion, the Proxy Server is a gateway between you and the internet. Proxy Servers offer varying functionality, security, and privacy levels based on specific needs or company policy. We hope this blog has aided in improving your understanding of Proxy Server, its key features, and benefits.
Unlock the potential of Cyber Security. Explore our Malware Analysis Training and stay ahead of the curve.







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


