We may not have the course you’re looking for. If you enquire or give us a call on +61 1-800-150644 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
AWS Security Token Service (STS) from Amazon Web Services is a vital component today that ensures the safety of temporary security credentials for users and applications by allowing them to access AWS resources securely. It's a way of enhancing security by making medium-term access to credentials instead of long-term ones, thereby reducing the risks of exposing them.
An STS identity in AWS is especially essential when accessing multiple accounts and applying for identity federation. This service helps grant permissions to the users and services, and the principle of least privilege is followed, thus ensuring that you do not grant more access to resources than required.
Table of Contents
1) What is AWS?
2) What is AWS STS?
3) Working on AWS STS
4) Example of AWS STS
5) Use cases for AWS Security Token Service
6) Conclusion
What is AWS?
Amazon Web Services (AWS) is a well-established cloud platform developed by Amazon and used in many organisations globally. It creates more than 200 sophisticated services for users from locations supported worldwide.
AWS offers computing power, storage space, and networking options for businesses to grow and scale. Inventors, institutions, and start-ups use AWS as a platform to host apps, handle databases, deliver content, and do many other things.
The platform provides users with tailored solutions that align with their business scalability without breaking the bank. AWS offers clients a wide range of applications, including those they find perfectly suitable for their tasks.
What is AWS STS?
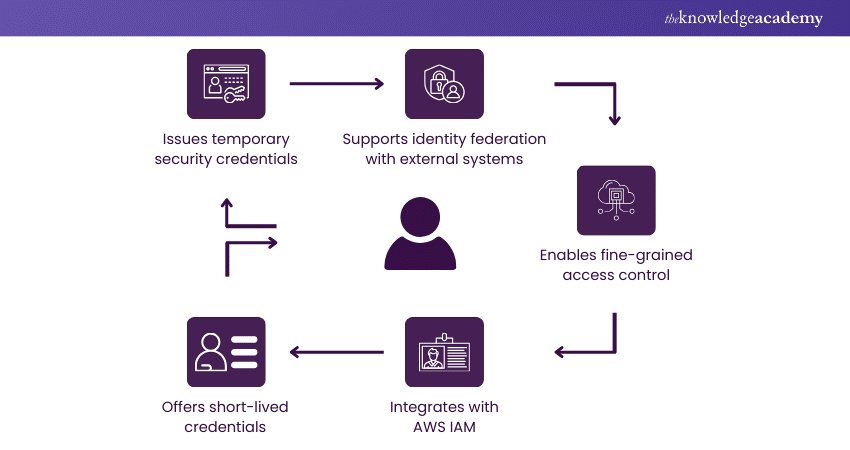
Amazon Web Services Security Token Service (AWS STS) is an integral part of the AWS Identity and Access Management (IAM) set of services. It encourages customers to increase the security of their AWS accounts significantly. AWS STS creates short-living credentials (with restricted permission) that one can use for AWS services interaction, thus lowering the chance of reusing a single credential for an extended period.
This service has proven to be most helpful in cases where the process of granting temporary access to AWS resources is required by users or applications, which often happens in cross-account access setups or when integrating external services.
These credentials issued temporarily by the AWS STS (Security Token Service) can expire after a specific duration that the user sets. They expire after the time set has reached or elapsed, adding another security measure to the Serverless environment.
Generating the temporary security tokens via STS further helps implement the identity federation by allowing the users to authenticate through the external identity providers, which later gives them temporary access to AWS resources as well.
This flexibility and security make AWS STS an irreplaceable and efficient tool for managing security in a fast-changing and scalability-capable cloud environment.
Working of AWS STS
The working of AWS Security Token Service (STS) can be summarised in the following points:
a) Request for temporary credentials: Users or apps ask AWS STF for ephemeral security tokens for authentication and access rights.
b) Authentication: AWS STS determines the requester's identity (IAM user, AWS role switch, or Active Directory Federated Identity Provider) among the specific techniques used for the verification process.
c) Authorisation: Upon verification, AWS STS inspects the policies and permissions relevant to a particular requester to provide the level of access they should have.
d) Temporary credential generation: In particular, STS of AWS provides temporary security credentials, which are a combination of the Access Key ID, Secret Access Key, and Session Token, if authenticity and authority are affirmed.
e) Credential expiry: The time to live parameter of the temporary credential configuration can be set to a few minutes or a couple of hours. After their validity expires, these certifications are no longer valid.
f) Resource access: Users or applications deal briefly with the accessed AWS resources through the intermedia temporary credentials. Such resources and services are S3 buckets, EC2 instances, or DynamoDB tables. Depending on assigned permissions.
g) Periodic renewal: Conversely, the applicant may still require application access beyond expiration. They can request a new temporary set of credentials from AWS STS.
h) Revocation: The STS will be temporarily deactivated and expire automatically if it exceeds the predetermined period. If the user or administrator revokes it, that's how AWS STS can guarantee security and compliance.
Example of AWS STS
Here's an example scenario illustrating the use of AWS Security Token Service (STS) in a cross-account access setup:
a) Scenario: Company A may have several AWS servers and wish to allow developers from one account (Account A) to access resources in another account (Account B) securely.
b) Setup IAM roles: In the ACC. account, a role named IAM is created with access rights to a particular s3 bucket, and its EC2 instance
c) Trust relationship: A trust relationship is enforced between Account A and Account B beforehand. This makes Account A assume the IAM role created in Account B.
d) Assume role API call: Developers in one account (Account A) make an AssumeRole API call to Security Token Service using a temporary cross-account IAM role in another account (Account B).
e) Authentication and authorisation: AWS STS determines the identity of the requester and the role permissions at Account B to see if they align correctly.
f) Temporary credentials generation: When the authentication and authorisation are accomplished, AWS STS generates temporary security credentials specified as {Access Key ID, Secret Access Key, and Session Token} for the developers in Account A.
g) Resource access: Developers apply these credentials in Account B, which allows them to do many things, like uploading files to an S3 bucket or installing EC2.
h) Limited access: The credentials time out after a specific duration, which is normally one hour. At the end of the session, the keys for developers expire, and they must request resultant access if needed.
i) Security: The absence of developers accessing the resources of the stated account (Account B) for restricted periods of time reduces the possibility of unauthorised access. Moreover, AWS STS handles credential digestion, lowering the risk of credential leakage.
j) Revocation: Provisional designations auto expired after their allotted time frame when they can no longer be used, ensuring access is cut off as soon as needed.
Are you interested in mastering elastic compute Cloud with AWS? Then register now for our AWS Associate Solutions Architect Training!
Use cases for AWS Security Token Service (STS)
Let's look at some use cases for AWS Security Token Service to help you understand better:
1) Identity federation
The identity federation mechanism enables users to access AWS resources by taking their existing credentials from outside identity providers (IdP) such as Microsoft, Google, or Facebook.
AWS STS handles the process by assuming an IAM role and creating a temporary security Web identification for an authenticated user. This use case offers several benefits:
a) Single Sign-On (SSO): Users can enjoy AWS access to several other apps with only one (1) set of credentials. When it comes to authentication, this process shall be simplified, and users will have no problems.
b) Centralised Identity Management: Organisations can centralise their identity management, which would help reduce the related overhead and also ensure consistency wherever it is used.
c) Integration with existing systems: By integrating with already available identity providers, organisations can utilise their existing investments in identity management software without further endangering security.
d) Granular access control: Users can access only those AWS resources relevant to their jobs by the least privilege principle. IAM roles can be configured.
e) Enhanced security: The AWS STS temporal credentials are valid only for a limited period. Thus, a safer STS game is to pick up credentials from unethical persons and unauthorised access. Also, federated access for different users can be denied by deactivating their accounts in the identity provider.
2) STS credentials for EC2 instances
AWS STS can present transient security credentials to the instances of Amazon EC2 (EC2 instances), enabling applications running on EC2 instances to get access to other AWS services securely. This use case offers several advantages:
a) Least privilege access: Identical to EC2 instances can be accorded IAM roles with limited access to sources to only the sources they require. This results in fewer accessible remote network points and increased security levels.
b) Dynamic access control: The expiration time of any temporary credentials built by STS in AWS can be configured, allowing administrators to set rules based on their needs. Credentials should also be rotated regularly to diminish any risk of unauthorised access to the network.
c) Integration with AWS services: The EC2 instances can obtain temporary passwords to interface with different AWS services, such as Amazon S3, DynamoDB, and RDS, without a long-lasting one being persistent within their local environment. This particularly facilitates the development process and ensures security.
d) Instance profiles: IAM rules for EC2 instances that use an instance profile are also covered. Instances are no longer rocked with managing credentials directly on EC2 instances but with a cloud process that reduces complexity and enhances manageability.
3) Cross-account access with AWS STS
The cross-account function allows users from one AWS account to access resources in another account atmosphere. STS in AWS can do this by passing on the IAM roles and returning with the temporary central document. This use case offers several benefits:
a) Isolation of Resources: For organisations, AWS accounts can be a tool for separating various business units or projects and enforcing boundaries between resources and processes.
b) Granular access control: IAM roles can be created with the most granular permissions, the granules needed for administrators to control resource access from different AWS accounts.
c) Centralised management: Cross-account access provisioning could be centralised inside AWS Organisations and through the IAM role, thus giving administrators a view into their policies on access control.
d) Auditability and compliance: Multiple account usage information is written in the AWS CloudTrail service so that firms can check and audit the activities as formal procedures, which is the only proof that the law’s requirements are followed.
e) Cost optimisation: Sharing resources across multiple accounts allows organisations to utilise economies of scale and blend unutilised resources to optimise costs.
Conclusion
AWS Security Token Service offers versatile identity and access management capabilities in various scenarios, including identity federation, EC2 instance access, and cross-account access. By leveraging temporary security credentials and IAM roles, organisations can enhance security, streamline access management, and achieve compliance with regulatory requirements in the AWS cloud environment.
Learn more about AWS with our AWS Certification Training – sign up now!
Frequently Asked Questions

In AWS, a Security Token Service (STS) is a web service that provides temporary, limited-privilege credentials for accessing AWS resources securely.

An AWS authentication token is a temporary security credential issued by AWS STS to authenticate and authorise requests to AWS services.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various AWS Certification Training Courses, including the Architecting on AWS - Associate Certification Course, AWS Professional DevOps Engineer Training, and Systems Operations on AWS - Associate Certification Training. These courses cater to different skill levels, providing comprehensive insights into AWS Careers.
Our Cloud Computing Blogs cover a range of topics related to AWS, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Cloud Computing skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming Cloud Computing Resources Batches & Dates
Date
 Introduction to AWS Security
Introduction to AWS Security
Fri 27th Dec 2024
Fri 24th Jan 2025
Fri 21st Mar 2025
Fri 2nd May 2025
Fri 27th Jun 2025
Fri 29th Aug 2025
Fri 3rd Oct 2025
Fri 5th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


