We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203 999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Imagine Malware Analysis as a fascinating test match, where your computer’s security is the wicket. Every delivery, whether it’s dynamic, static, or hybrid analysis, is designed to outsmart the opposition—the malware. With the right tools and techniques, you can bowl out the threats, defend your system, and lead your team to victory in the cybersecurity playground. Read below to know more!
Table of Contents
1) What is Malware Analysis?
2) Different Types of Malware Analysis
3) Use Cases for Malware Analysis
4) Four Stages of Malware Analysis
5) Malware Analysis Tools
6) Benefits of Malware Analysis
7) Drawbacks of Malware Analysis
8) Conclusion
What is Malware Analysis?
Malware Analysis examines and understands malicious software to determine its origin, functionality, and potential impact. It involves studying the malware's behaviour, code, and purpose to develop effective defences and mitigation strategies. This analysis helps cybersecurity professionals protect systems and networks from similar threats in the future.
Different Types of Malware Analysis
Malware Analysis is important to understand the ways malicious software operates and the associated methodologies to defend against it. Here are some of the different types of Malware Analysis:
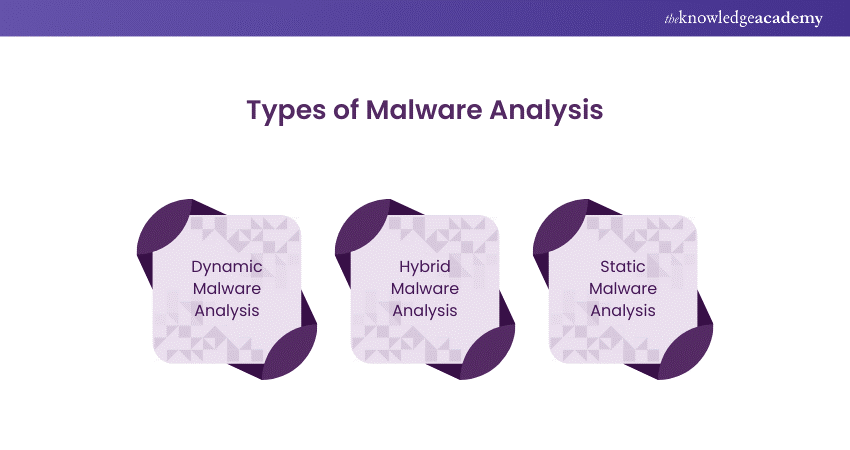
1) Dynamic Malware Analysis
Dynamic Malware Analysis involves executing the malware in a controlled environment to observe its behaviour in real-time. Analysts monitor how the malware interacts with the system, networks, and files, providing insights into its actions and potential damage.
2) Hybrid Malware Analysis
Hybrid Malware Analysis combines dynamic and static techniques to gain a comprehensive understanding of malware. It involves observing the malware's real-time behaviour and analysing its code without execution. This approach provides a balanced perspective on the malware's functionality.
3) Static Malware Analysis
Static Malware Analysis focuses on examining the malware's code without executing it. Analysts study the binary files, disassembled code, and other static features to identify malicious signatures, functionalities, and potential threats. This method is useful for understanding the constructional way of malware.
Transform your investigation skills with Digital Forensics Training - join today!
Use Cases for Malware Analysis
There is a plethora of use cases for Malware Analysis. Below listed are few of those vital applications:
Research on Malware
Malware Analysis enables researchers to discover the inner workings of malicious software. This approach allows them to identify new variants, understand attack techniques, and develop improved security measures.
Threat Alerts and Triage
Security teams use Malware Analysis to assess the severity of threats quickly. This process helps prioritise responses and allocate resources efficiently, ensuring the most dangerous threats are addressed first.
Threat Hunting
Malware Analysis supports proactive threat hunting by providing insights into attackers' tactics, techniques, and procedures (TTPs), further helping security teams detect and eliminate hidden threats.
Detection of Malware
Malware Analysis improves malware detection by enhancing the signatures and heuristics used in security tools, enabling faster identification and blocking of malicious activities.
Incident Response
Malware Analysis is essential during incident response. It helps to identify the scope and impact of a breach, guide containment efforts, and assist in the recovery and prevention of future incidents.
Four Stages of Malware Analysis
Malware Analysis involves multiple stages, each crucial for understanding the nature of the threat and developing appropriate counter-measures. Below are the four primary stages of Malware Analysis:
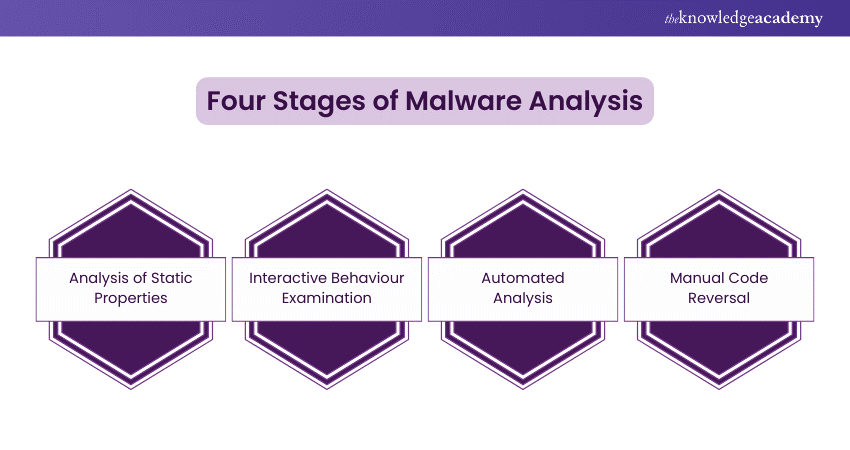
Analysis of Static Properties
During this stage, analysts examine the malware without executing it. They focus on file metadata, strings, and binary signatures to gather initial insights. By analysing static properties, they can identify the malware's structure, potential origin, and intended targets.
Interactive Behaviour Examination
In this stage, analysts run the malware in a controlled environment to observe its behaviour. They monitor how it interacts with the system, noting any changes it makes, such as file creation or network communication. This helps in understanding the malware's functionality.
Automated Analysis
Automated tools are used to quickly analyse the malware's behaviour and characteristics. These tools can scan for known patterns and vulnerabilities, providing rapid assessments. Automated analysis aids in efficiently identifying common malware traits and prioritising threats for further investigation.
Manual Code Reversal
In this final stage, analysts manually reverse-engineer the malware's code to uncover its exact operations. This deep analysis reveals the malware's logic, hidden functions, and any obfuscation techniques used by the attackers. Manual code reversal is critical for crafting specific counter-measures.
Kickstart your forensic journey with Computer Forensics Foundation Training- register today!
Malware Analysis Tools
There are various tools available for effective Malware Analysis, each offering unique features to dissect and understand malicious software. Below are some of the prominent tools used in the industry:
Ghidra
Ghidra is a powerful open-source reverse engineering tool developed by the NSA. It allows analysts to decompile and analyse malware binaries, enabling a deeper understanding of the software’s inner workings.
Fiddler
Fiddler is a versatile web debugging tool that allows analysts to inspect and modify network traffic. It is widely used in Malware Analysis to observe how malware communicates over the network and detect anomalies.
PeStudio
PeStudio is a lightweight, yet robust tool designed for static analysis of Windows executables. It quickly identifies suspicious elements in a file, such as malware indicators, without executing the code, making it a safe option for preliminary analysis.
Process Hacker
Process Hacker is an advanced task manager and system monitoring tool. It is utilised in Malware Analysis to monitor processes, detect hidden activities, and analyse the behaviour of malicious software in real-time.
Limon
Limon is an open-source sandbox tool that provides a controlled environment to execute and analyse malware safely. It helps analysts observe malware's behaviour and effects in isolation, preventing harm to the actual system.
Benefits of Malware Analysis
1) Malware Analysis provides valuable insights that help organisations protect their systems and respond effectively to threats. Below are some key benefits of conducting Malware Analysis:
2) Malware Analysis enables organisations to understand the behaviour and impact of malicious software, allowing them to create effective defences.
3) It helps identify vulnerabilities exploited by malware, improving system security.
4) Analysts can develop signatures and detection methods to prevent future attacks.
5) The process supports incident response by providing insights into the origin and nature of the malware.
Turbocharge your incident response skills with Incident Response Training - register now!
Drawbacks of Malware Analysis
Despite its many advantages, Malware Analysis also presents specific challenges and risks. Below are some of the drawbacks associated with this process:
1) Malware Analysis can be time-consuming and requires significant resources and expertise.
2) The process carries the risk of accidentally executing the malware, which can lead to a system infection.
3) Advanced malware may use obfuscation techniques that make analysis challenging and less effective.
4) Static analysis, in particular, might not reveal the complete behaviour of the malware, leading to incomplete or inaccurate conclusions.
Conclusion
In the intricate world of cybersecurity, proficiency in Malware Analysis is crucial for defending against relentless threats. By understanding its malware tools and stages, you equip yourself with the knowledge to anticipate and neutralise potential attacks. Embrace this guide as your playbook and take your first steps toward safeguarding your digital ecosystem confidently.
Build a lucrative cybersecurity career with Introduction To System And Network Security Training- start today!
Frequently Asked Questions

The general rules for Malware Analysis involve isolating malware in a controlled environment to prevent its spread, combining static and dynamic analysis for a comprehensive understanding, and documenting findings carefully. It’s also crucial to keep backups, use up-to-date tools, and always avoid executing malware on live systems.

Malware Analysis can be time-consuming and complex, which demands specialised skills. If not properly contained, it risks accidental system infection. Advanced malware may evade detection through obfuscation. Static analysis may miss dynamic behaviours, leading to incomplete conclusions.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Cyber Security Training, including the Digital Forensics Training, and Incident Response Training. These courses cater to different skill levels, providing comprehensive insights into Cyber Security Resume: Examples and Template.
Our IT Security & Data Protection Blogs cover a range of topics related to cybersecurity and data protection, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your IT security skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Malware Analysis Training
Malware Analysis Training
Fri 14th Feb 2025
Fri 11th Apr 2025
Fri 13th Jun 2025
Fri 15th Aug 2025
Fri 10th Oct 2025
Fri 12th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


