We may not have the course you’re looking for. If you enquire or give us a call on 44 1344 203 999 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Picture this: you're attending a CCNA Interview and being asked questions like, “How do you configure a router?” or “What steps would you take to secure a network?” Stepping into the world of CCNA interviews can feel like navigating a maze, but with the proper preparation, you can find your way with ease. Our blog on “Top 73 CCNA Interview Questions and Answers” is your ultimate guide to mastering the interview process.
With our carefully curated list of CCNA Interview Questions, you’ll be ready to tackle any challenge that comes your way. This blog is designed to help you understand the core concepts and provide clear, concise answers. Let's dive in and land your dream job!
Table of Contents
1) CCNA Interview Questions and Answers for Beginners
2) CCNA Interview Questions and Answers for Intermediates
3) Advanced and Scenario-based CCNA Interview Questions and Answers
4) Conclusion
CCNA Interview Questions and Answers for Beginners
Here is a list of the top 20 CCNA Interview Questions along with their answers:
1) What is a MAC Address?
Answer: A Media Access Control (MAC) address is a unique identifier assigned to a Network Interface Card (NIC) by the manufacturer. It is a 48-bit hexadecimal value used for communication at the data link layer of the Open Systems Interconnection (OSI) OSI model.
2) What is the Difference Between a Switch and a hub?
Answer: A Hub, operating at the physical layer of the Open Systems Interconnection (OSI) model, broadcasts data to all connected devices. Conversely, a Switch functions at the data link layer, establishing dedicated connections for more efficient and secure communication.
3) Define the Concept of a Subnet Mask.
Answer: A subnet mask is a 32-bit value used to determine the network and host portions of an IP address. It is applied to an IP address to identify the network ID and host ID within that network.
4) What is the Purpose of Address Resolution Protocol (ARP)?
Answer: ARP maps an IP address to a MAC address on a local network. It allows devices to discover and communicate with each other at the data link layer using MAC addresses.
5) What is a Default Gateway?
Answer: The default gateway is the IP address of the router or layer 3 switch that connects a local network to external networks. It is used to forward traffic destined for networks outside the local subnet.
6) What is a VLAN?
Answer: VLAN is the acronym for Virtual Local Area Network, which is a logical grouping of devices on a network, regardless of their physical location. It allows for network segmentation and isolation, enhancing security and Network Management.
7) What is the Purpose of a Domain Name System (DNS)?
Answer: DNS is used to translate human-readable domain names (e.g., www.example.com) into IP addresses. It enables users to access resources on the internet using domain names instead of remembering IP addresses. Understanding DNS is essential for the CCNA syllabus.
8) What is a Router?
Answer: A Router is a network device that connects multiple networks and directs traffic between them based on IP addresses. It operates at the network layer of the OSI model.
9) What is the Difference Between TCP and UDP?
Answer: Transmission Control Protocol (TCP) provides reliable, connection-oriented communication with error-checking and flow control. User Datagram Protocol (UDP) provides faster, connectionless communication without error-checking or flow control.
10) What is the Purpose of Dynamic Host Configuration Protocol (DHCP)?
Answer: DHCP is used to automatically assign IP addresses, subnet masks, default gateways, and other network configuration parameters to devices on a network. It helps eliminate the need for manual IP configuration.
11) What is a Loopback Address?
Answer: A loopback address is a special IP address used to test network connectivity on the local device. Packets sent to the loopback address are not transmitted on the network.
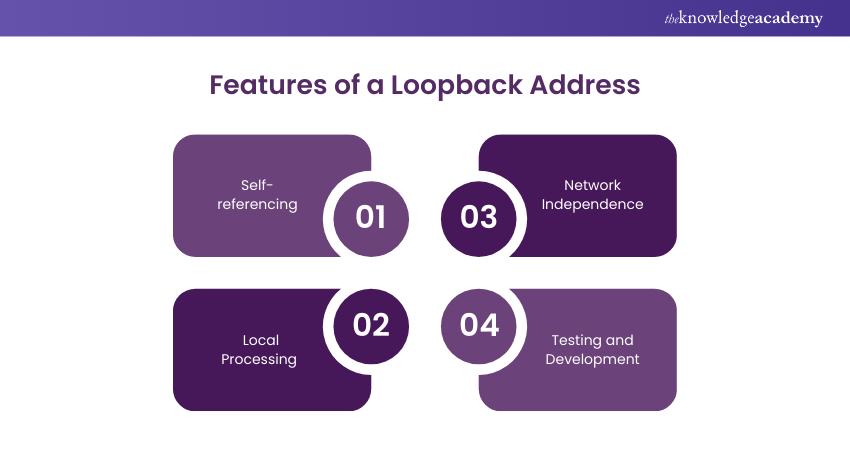
This ensures that the device’s network stack is functioning correctly without involving external networks.
12) What is the Difference Between a Static and Dynamic Routing Protocol?
Answer: A Network Administrator manually configures network routes in static routing. On the other hand, dynamic routing protocols allow routers to exchange routing information and automatically adjust routing tables based on network changes.
13) What is ICMP?
Answer: Internet Control Message Protocol (ICMP) is a network protocol used for diagnostics and error reporting in IP networks. It includes functions such as ping (to test network connectivity) and traceroute (to trace the path of packets across a network).
14) What is a Broadcast Domain?
Answer: A broadcast domain is a logical division of a network in which all devices receive broadcast messages. Devices within the same broadcast domain can directly communicate with each other using MAC addresses. This concept is crucial for the network engineer job description.
15) What is the Purpose of Network Address Translation (NAT)?
Answer: NAT is used to translate private IP addresses to public IP addresses for communication over the internet. It allows multiple devices to share a single public IP address and provides an added layer of security.
16) What is the Difference Between Half-duplex and Full-duplex Communication?
Answer: Data can be transmitted in both directions but not simultaneously in a half-duplex communication. Only one device can send data at a time. On the other hand, in full-duplex communication, data can be transmitted simultaneously in both directions, allowing for faster communication.
17) What is the Spanning Tree Protocol (STP)?
Answer: STP is a network protocol that prevents loops in a switched network by creating a loop-free logical topology. It determines the best path for traffic and disables redundant paths to avoid network loops.
18) What is the Purpose of the Access Control List (ACL)?
Answer: ACLs control network traffic by filtering packets based on specified criteria. They permit or deny traffic based on source/destination IP addresses, protocols, ports, or other criteria.
19) What is a Default Route?
Answer: A default route is a routing entry used when no specific route exists in the routing table for a particular destination. It directs packets to the default gateway for further routing.
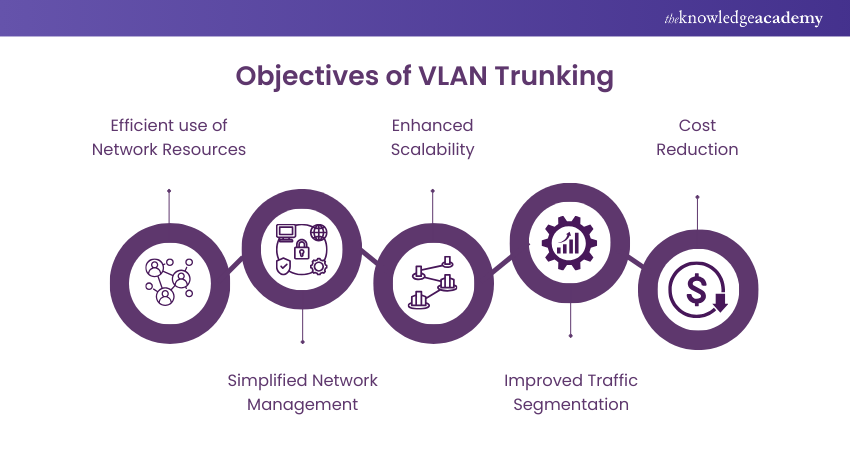
20) What is the Purpose of VLAN Trunking?
Answer: Virtual Local Area Network (VLAN) Trunking allows multiple VLANs to be carried over a single physical link between switches.
Start your journey to becoming a Cisco Certified Network Associate with our CCNA Training!
21) What is Latency?
Answer: Latency is used to describe the delay of time between when a network device receives a data frame and when the network device resends this data frame out towards another network segment.
22) What Causes Network Congestion?
Answers: Network congestion occurs when an excessive number of users attempt to utilise a shared bandwidth simultaneously. This phenomenon mostly occurs in larger networks that lack the efficient practice of network segmentation.
23) Explain how Cut-through LAN Switching Works.
Answers: In Cut-through LAN switching, upon receiving a data frame, the router quickly forwards it to the next network segment after analysing the destination address without delay.
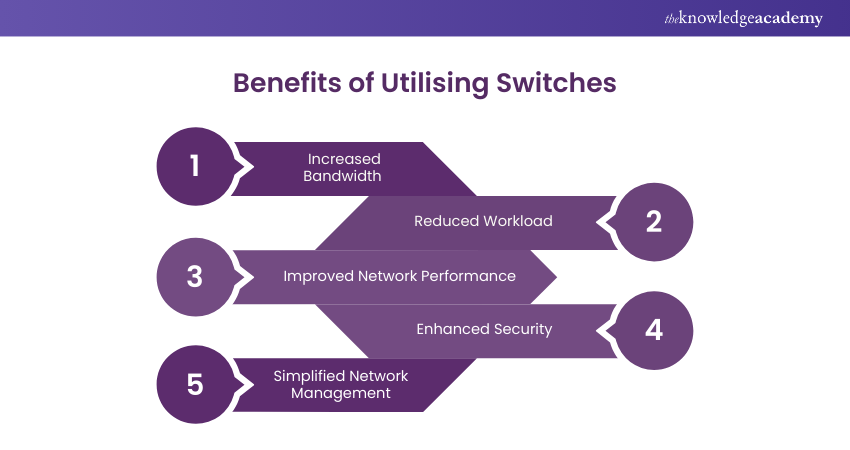
24) Explain the Advantage of Using Switches.
Answer: Utilising a Switch offers a more efficient data transmission method in comparison to broadcasting data across all ports. Switches transform the incoming signal into a frame. This is followed by accessing and decoding the destination address and finally directing the frame to the corresponding port.
25) What do Data Packets Consist of?
Sample Answer: Within a Data Packet, many components are available, including details about the sender, information regarding the recipient, and the actual data being transmitted. Additionally, each Data Packet is tagged with a numeric identification number, which not only defines its sequential order but also defines it as a specific packet number.
26) What are the Different Types of Passwords Used in Securing a CISCO Router?
Sample Answer: There are five distinct password types available, including enable secret, virtual terminal, console, and auxiliary.
27) Define Data Packets.
Answer: A Data Packet serves as a compact data unit bundled for transmission across a network. Also known as Network Layer Packages, they play a crucial role in the operation of the IP protocol as they sum up essential IP information within each packet. Data Packets contain a wealth of critical information, including email messages, web data, and Voice-over-IP (VoIP) calls. This knowledge supports effective management of various network topologies, including ring network topology. Each Data Packet has a unique numeric identification number that not only defines its order but also assigns it a unique packet number.
28) Define MTU.
Answer: The Maximum Transmission Unit (MTU) is the largest frame or packet size a network device can handle, typically set at 1500 bytes by default, matching the Ethernet standard. In data transmission, Transmission Control Panel (TCP) uses the MTU to determine the maximum packet size for efficient communication.
CCNA Interview Questions and answers for Intermediate
Interviews for CCNA job roles within the Information Technology (IT) field will mandatorily assess your knowledge and understanding of technical terms and concepts across various difficulty levels, including those related to CCNA Router Configuration Commands Guide. Let’s look at the top CCNA Interview Questions
29) What is the Difference Between a hub, a Switch and a Router? Explain Their Respective Functions in a Network.
Answer: A Hub is a simple networking device that connects multiple devices in a network, but it operates at the physical layer (Layer 1) and does not perform any intelligent data forwarding.
A Switch operates at the data link layer (Layer 2) and forwards data within a local network based on MAC addresses.
A Router operates at the network layer (Layer 3) and forwards data between different networks based on IP addresses.
30) What is the Purpose of Subnetting, and how Does it Help in Network Design and Addressing?
Answer: Subnetting allows the division of a large network into smaller subnetworks, known as subnets. It helps in network design and addressing by:
a) Efficiently utilising IP address space.
b) Enhancing network performance by reducing network traffic.
c) Improving Network Security by creating isolated subnets.
d) Facilitating Network Management and troubleshooting.
31) Explain the Process of IP Address Allocation in IPv4. What are the Different IP Address Classes, and how are They Used?
Answer: In IPv4, IP addresses are allocated based on different address classes:
a) Class A addresses have the first octet reserved for network identification and can support a large number of hosts.
b) Class B addresses allocate the first two octets for network identification and are suitable for medium-sized networks.
c) Class C addresses allocate the first three octets for network identification and are typically used for small networks.
d) Class D addresses are reserved for multicast addresses.
e) Class E addresses are reserved for experimental purposes.
Sign up for our Cisco Meraki Training and master the latest in cloud-managed networks – boost your professional growth and confidence!
32) What is the OSI Model? Describe the Seven Layers and Their Functions?
Answer: The Open Systems Interconnection (OSI) model is a conceptual framework that standardises network protocols. Its seven layers and their functions are as:
a) Physical Layer: Deals with the physical transmission of data over the network.
b) Data link Layer: Provides error-free data transmission between adjacent devices.
c) Network Layer: Handles logical addressing and routing of data between networks.
d) Transport Layer: Ensures reliable data delivery and manages end-to-end communication.
e) Session Layer: Establishes and maintains communication sessions between applications.
f) Presentation Layer: Formats and encrypts data for proper representation and security.
g) Application Layer: Provides network services to applications and end-users.
33) What is VLAN Pruning, and how Does it Work?
Answer: VLAN Pruning is a technique used to optimise VLAN traffic within a network. It prevents unnecessary broadcast traffic from being forwarded to switches that do not have any ports belonging to the respective VLAN.
VLAN Pruning operates by allowing the VLAN information to be shared among Switches through VLAN Trunking Protocol (VTP). When a Switch receives a broadcast, it checks the VLAN membership of the port and prunes any VLANs that are not active on the receiving switch, thus reducing unnecessary broadcast traffic.
34) What is the Purpose of a DHCP Relay Agent?
Answer: A Dynamic Host Configuration Protocol (DHCP) relay agent is used to forward DHCP messages between DHCP clients and DHCP servers located on different networks.
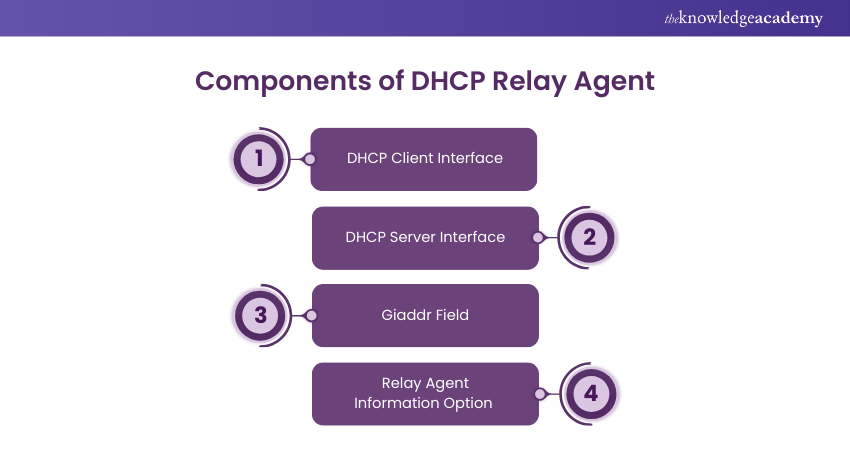
When a DHCP client sends a DHCP Discover message, the relay agent intercepts the broadcast, encapsulates it in a unicast packet, and forwards it to the DHCP server. The DHCP relay agent helps extend the reach of DHCP servers and allows clients in different network segments to obtain IP configuration information dynamically.
35) What is the Purpose of VLANs? How do They Enhance Network Segmentation and Security?
Answer: VLANs divide a single physical network into multiple logical networks, enhancing network segmentation and security by performing the following:
a) Isolating network traffic, limiting broadcasts, and improving network performance.
b) Providing logical grouping of devices regardless of their physical location.
c) Enabling easier Ntwork Management and scalability.
d) Enhancing Network Security by controlling access between VLANs and implementing VLAN-based policies.
36) What is the Difference Between Static NAT and Dynamic NAT?
Answer: Static NAT and Dynamic NAT are both methods of translating private IP addresses to public IP addresses for communication with external networks. The main difference between them is as follows:
a) Static NAT: It maps a private IP address to a specific public IP address on a one-to-one basis. It provides a direct and fixed translation between private and public IP addresses.
b) Dynamic NAT: It maps a private IP address to an available public IP address from a pool of addresses. The mapping is performed dynamically as needed, allowing multiple private addresses to share a limited number of public IP addresses.
37) Describe the Different NAT Types and Their Functionalities.
Answer: NAT is a process that translates private IP addresses to public IP addresses and vice versa. Different types of NAT include Static NAT, Dynamic NAT, and Port Address Translation (PAT).
Static NAT maps one private IP address to one public IP address, dynamic NAT maps multiple private IP addresses to a pool of public IP addresses, and PAT maps multiple private IP addresses to a single public IP address using different ports.
38) What are Some Common WAN Technologies Used for interconnecting Remote Locations?
Answer: Common WAN technologies include the following:
a) Leased lines: Dedicated, point-to-point connections provided by service providers.
b) Multi-Protocol Label Switching (MPLS): A protocol for efficient data forwarding in WANs.
c) Point-to-Point Protocol (PPP): A protocol for establishing a direct connection between two nodes.
d) Frame Relay: A packet-switched technology that uses virtual circuits.
e) Virtual Private Network (VPN): Provides secure remote access over public networks.
39) What is the Difference Between a Static IP Address and a Dynamic IP Address? When Would you use Each Type?
Answer: A static IP address is manually assigned and remains constant, ideal for servers and critical infrastructure. In contrast, a dynamic IP address is automatically assigned by a DHCP server and can change over time, commonly used for client devices like computers and smartphones
40) What is a MAC Address, and how is it Different From an IP Address?
Answer: A MAC address is a unique identifier assigned to a network interface card (NIC). It is a hardware-based address and operates at the OSI model’s data link layer. MAC addresses are represented as a combination of six hexadecimal pairs, separated by colons or hyphens. Unlike IP addresses, MAC addresses are assigned by the manufacturer and are typically permanent.
41) Explain the Concept of VLAN Tagging and its Significance in a Network.
Answer: VLAN tagging is a method used to identify and differentiate VLAN traffic. It involves adding additional information, known as a VLAN tag or VLAN header, to Ethernet frames. VLAN tagging is significant because it enables the switch to distinguish between different VLANs and ensures that traffic is delivered to the appropriate VLAN members, even when multiple VLANs share the same physical network infrastructure.
42) What is the Purpose of a Subnet Mask, and how is it Used in IP Addressing?
Answer: A subnet mask is a 32-bit value used to divide an IP address into a network portion and a host portion. It helps determine which part of an IP address represents the network and which part represents the host.
By comparing the subnet mask with an IP address, devices can identify the network to which the IP address belongs and determine if the destination IP address is on the local network or a remote network.
43) What is Open Shortest Path First (OSPF), and how Does it Work?
Answer: OSPF is a link-state routing protocol used to determine the best path for routing IP packets within a network. It operates by exchanging Link-State Advertisements (LSAs) among routers to build a complete map of the network topology.
OSPF routers exchange information about their connected links, including their state, cost, and bandwidth. With this information, OSPF calculates the shortest path to each network destination using Dijkstra's algorithm. The OSPF routing table is then built based on this calculation, allowing routers to make informed routing decisions and dynamically adapt to changes in the network topology.
44) Explain the Concept of VPN and its Benefits.
Answer: A Virtual Private Network (VPN) is a secure and encrypted connection that allows remote users or branch offices to connect to a private network over a public network, such as the internet. It creates a virtual tunnel between the user/device and the private network, ensuring that data transmitted over the connection remains secure and private. The benefits of VPN include:
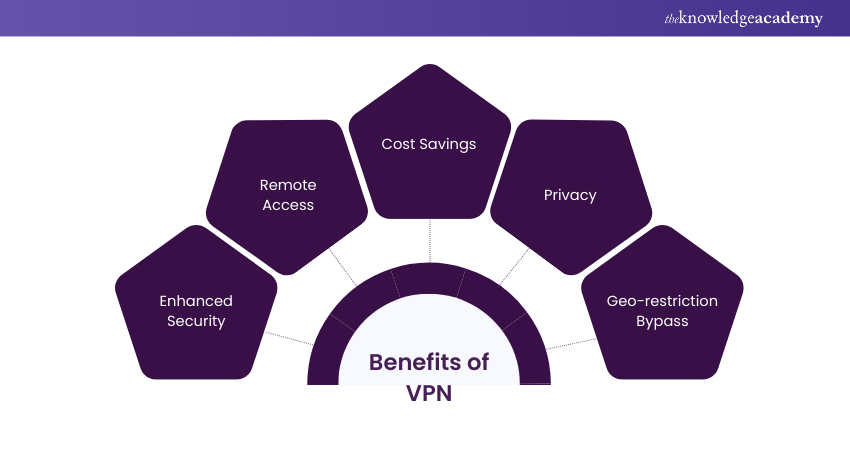
a) VPNs use encryption protocols to protect data from interception and unauthorised access.
b) VPNs enable users to securely access private network resources from anywhere, providing flexibility and mobility.
c) VPNs eliminate the need for dedicated leased lines, as they utilise existing internet connections, resulting in cost savings.
d) VPNs mask the user's IP address, making it difficult for others to track their online activities.
e) VPNs can bypass geographic restrictions, allowing users to access region-restricted content or services.
45) How Does DHCP Work?
Answer: DHCP is a network protocol used to automatically assign IP addresses and network configuration parameters to devices on a network. Its purpose is to simplify network administration and eliminate the need for manual IP address configuration.
DHCP works by using a DHCP server to lease IP addresses to client devices, along with other network configuration details such as subnet mask, default gateway, and DNS server addresses.
46) What is the Purpose of the Spanning Tree Protocol (STP) in Switching? How Does it Prevent Network Loops?
Answer: STP is a protocol that prevents network loops in Ethernet networks by ensuring only one active path exists between devices. It elects a root bridge and determines the shortest path to it, blocking redundant paths to avoid broadcast storms and network instability.
47) What is the Purpose of VLAN Trunking and how Does it Work?
Answer: VLAN Trunking enables multiple VLANs to be transmitted over a single physical link between switches, allowing devices on different switches to communicate as if on the same VLAN. It tags Ethernet frames with VLAN IDs using protocols like IEEE 802.1Q, ensuring switches can identify and forward traffic to the correct VLANs.
48) Explain the Three Sources of Signal Degradation on a Data Link.
Answer: The three sources of signal degradation on a data link are attenuation, interference, and distortion. Attenuation is a result of the resistance within the medium. Interference is due to external noise introduced into the medium. Distortion occurs because of the reactive characteristics of the medium, which react differently to various frequency components of the signal.
Learn how to design, configure, and troubleshoot complex networks – join our GNS3 Training now!
Advanced and Scenario-based CCNA Interview Questions and Answers
Understanding how to approach and solve practical networking scenarios will demonstrate your problem-solving skills and knowledge in real-world networking situations. Here is a list of some CCNA Interview Questions and answers at an advanced level:
49) You are Troubleshooting a Network Connectivity Issue Between two Hosts on the Same Subnet. What Steps Would you Take to Identify and Resolve the Problem?
Answer: In this scenario, it is better to start by verifying the physical connections and ensuring that both hosts are on the same subnet with the correct IP configurations. It is important to check if there are any firewall rules or access control lists blocking the traffic. Additionally, tools like ping, traceroute, and ARP can be used to diagnose and isolate the issue.
50) A User Reports That They are Unable to Access a Specific Website From Their Computer. What Could be the Possible Causes, and how Would you Troubleshoot the Issue?
Answer: There could be several causes for this issue. It could be a DNS problem, a network connectivity issue, or a firewall blocking access. To troubleshoot, you must check the DNS settings on the user's computer and ensure that it can resolve the website's domain name. Then, you must verify the network connectivity by pinging the website's IP address. If necessary, you must also check the firewall settings to ensure that access to the website is not blocked.
52) You Have Been Assigned to Configure a new VLAN on a Switch. What Steps Would you Take to Create and Implement the VLAN?
Answer: To create and implement a new VLAN, the following steps must performed:
a) Access the Switch's configuration mode
b) Create the VLAN using the appropriate command
c) Assign the VLAN to the desired switch ports using the interface configuration mode
d) Verify the VLAN configuration using show commands
53) A Company Wants to Implement a Redundant Network Design for High Availability. How Would you set up Redundant Links Between Switches and Prevent Network Loops?
Answer: To set up redundant links between switches and prevent network loops, a protocol like STP must be used. STP allows for automatic detection and disables redundant paths, ensuring that there is only one active path at any given time. By configuring STP on the switches, it will calculate the shortest path to the root bridge and block any redundant paths, thereby preventing network loops.
54) A Remote Employee is Unable to Establish a VPN Connection to the Corporate Network. How Would you Troubleshoot the Issue?
Answer: To troubleshoot the VPN connection issue, one must take steps like the following:
a) Verify the remote employee's internet connectivity and ensure they can reach the VPN server
b) Check the VPN client configuration on the employee's computer and ensure the correct settings are entered
c) Verify the VPN server configuration, including IPsec or SSL settings, and ensure the correct ports are open on firewalls
d) Check for any Network Address Translation (NAT) or firewall rules that may be blocking the VPN traffic
e) Analyse VPN logs for any error messages or indications of connectivity issues
55) A Network Switch has Experienced a Power Outage and has Rebooted. However, Some Devices Connected to the Switch are Unable to Obtain an IP Address. How Would you Troubleshoot This DHCP Issue?
Answer: To troubleshoot the DHCP issue, one must Perform the following operations:
a) Verify that the DHCP service is running on the server and check for any error messages
b) Confirm that the DHCP scope and address pool are properly configured with available IP addresses
c) Check if the switch ports connecting the affected devices are configured as access ports in the appropriate VLAN and are not in a shutdown state
56) A User Complains About Slow Network Performance. What Steps Would you Take to Troubleshoot and Resolve the Issue?
Answer: In this scenario, it is important to check the network utilisation and bandwidth usage. One must also investigate for any network congestion, faulty cables, or switches. Additionally, the network traffic must be analysed using tools like packet captures and network monitoring tools to identify any bottlenecks or abnormal behaviour.
57) A Network Device is Continuously Rebooting. What Could be the Possible Causes, and how Would you Address the Issue?
Answer: Possible causes for continuous reboots could include power supply issues, hardware failures, or software bugs. To address the issue, you must first check the power source and ensure it is stable. Then, inspect the device for any loose connections or faulty components. One must update the device's firmware or replace any faulty hardware if necessary.
58) A Company is Planning to Implement a Wireless Network. What Factors Would you Consider in Designing a Secure and Efficient Wireless Network?
Answer: When designing a secure and efficient wireless network, factors to consider include the following:
a) Network coverage and signal strength
b) Security protocols and encryption methods
c) Access control mechanisms
d) Interference from neighbouring wireless networks and non-Wi-Fi devices
e) Scalability and capacity planning for multiple devices
f) Network segmentation and VLAN configurations
g) Physical placement and deployment of access points
59) A Network Administrator Wants to Implement Quality of Service (QoS) to Prioritise VoIP Traffic on the Network. How Would you Configure QoS to Achieve This?
Answer: To prioritise VoIP traffic using QoS, you must:
a) Identify the VoIP traffic by assigning it a specific Differentiated Services Code Point (DSCP) value.
b) Configure QoS policies on network devices (routers, switches) to classify and mark the VoIP traffic using the DSCP value.
c) Implement traffic shaping or prioritisation mechanisms based on the marked VoIP traffic to ensure it receives the required network resources.
60) A Network Device is not Receiving an IP Address From the DHCP Server. How Would you Troubleshoot and Resolve This DHCP Issue?
Answer: To troubleshoot and resolve the DHCP issue, one must opt for the following strategies:
a) Verify the physical connectivity between the device and the network.
b) Check if the DHCP server is running and has available IP addresses in its pool.
c) Inspect the DHCP configuration on the server and ensure it is properly configured with the correct scopes and options.
d) Verify that the device is configured to obtain an IP address automatically (DHCP client) and that there are no conflicting static IP configurations on the device
61) A Network Switch is Exhibiting High CPU Utilisation. What Could be the Possible Causes, and how Would you Mitigate the Issue?
Answer: High CPU utilisation on a Switch could be caused by high network traffic, excessive broadcast/multicast traffic, spanning tree recalculations, or software bugs. One must identify the root cause using monitoring tools or logging features on the switch to mitigate the issue. Then, take steps like optimising network configurations, implementing traffic filters, upgrading switch firmware, or redistributing network load to alleviate the CPU load.
62) A Network Administrator Wants to Provide Secure Remote Access to the Internal Network. How Would you Implement This Using VPN Technology?
Answer: To provide secure remote access to the internal network using VPN technology, one must do the following:
a) Set up a VPN server, such as Cisco AnyConnect or OpenVPN, on the network.
c) Configure the appropriate authentication and encryption protocols to establish a secure connection.
c) Define user access policies and assign user credentials for authentication.
d) Ensure firewall rules allow VPN traffic to reach the internal network.
e) Educate and guide remote users on how to configure and connect to the VPN server using VPN client software.
63) A Network Administrator Wants to Segment the Network to Enhance Security. How Would you Implement Network Segmentation Using VLANs?
Answer: To implement network segmentation using VLANs, you must perform the following:
a) Identify the logical grouping of devices and determine the VLANs required.
b) Configure VLANs on Switches and assign specific switch ports to each VLAN.
c) Enable VLAN Trunking between Switches to carry multiple VLANs.
d) Implement VLAN Access Control Lists (VACLs) or firewall rules to restrict inter-VLAN communication as needed.
e) Verify connectivity and test the segmentation by ensuring devices in different VLANs cannot communicate by default.
64) A Company Plans to Upgrade its Network Infrastructure to Support Faster Network Speeds. How Would you Upgrade the Network From Fast Ethernet to Gigabit Ethernet?
Answer: To upgrade the network from Fast Ethernet to Gigabit Ethernet, one must opt for the following:
a) Replace the existing Fast Ethernet switches and network interfaces with Gigabit Ethernet switches and compatible network cards.
b) Update the cabling infrastructure to support Gigabit Ethernet.
c) Reconfigure the network devices with appropriate VLANs, IP addressing, and QoS settings.
d) Perform thorough testing to ensure proper connectivity and performance after the upgrade.
Join our CCNP Collaboration Training to stay updated with the latest collaboration technologies and best practices.
65) A Company Plans to Implement a Wireless Network with Multiple Access Points. How Would you Configure Seamless Roaming for Wireless Clients?
Answer: Here's how to configure seamless roaming for wireless clients:
a) Ensure all access points are configured with the same wireless network name (SSID) and security settings.
b) Enable a common authentication method (e.g., WPA2-Enterprise with 802.1X) to allow clients to authenticate against a centralised authentication server.
c) Configure the access points to use the same channel and non-overlapping frequency bands to minimise interference.
d) Adjust the signal coverage and power levels of the access points to provide sufficient overlap for seamless client handoffs between access points.
66) A Network Administrator suspects a network device may have a faulty NIC. How would you verify and troubleshoot the issue?
Answer: To verify and troubleshoot a NIC, one must do the following:
a) Test the suspected NIC by connecting it to a different device or connecting a known working NIC to the device.
b) Verify the NIC drivers and firmware are up to date.
c) Check for any physical damage or loose connections on the NIC.
d) Monitor the device's network traffic and error logs for any indications of NIC-related issues.
Note: If necessary, replace the NIC with a known working one and retest the connectivity.
67) A Network Administrator Wants to Monitor Network Traffic and Analyse Performance. How Would you set up Network Monitoring and What Tools Would you use?
Answer: To set up network monitoring and performance analysis, one must perform the following:
a) Deploy network monitoring tools such as Wireshark, SolarWinds, or PRTG to capture and analyse network traffic.
b) Configure network devices (routers, switches) to export NetFlow or SNMP data to the monitoring tools.
c) Set up monitoring thresholds and alerts for network devices, bandwidth utilisation, latency, and other performance metrics.
d) Implement packet capturing and analysis on specific network segments or devices to troubleshoot issues or detect anomalies.
68) How would you configure link aggregation using EtherChannel?
Answer: To configure link aggregation using EtherChannel, you must do the following:
a) Identify the switch ports that need to be aggregated.
b) Configure the same parameters (such as speed and duplex mode) on each of the ports.
c) Create an EtherChannel group and assign the desired protocol.
d) Enable the EtherChannel on the switch ports and ensure they are part of the same VLAN.
e) Verify the EtherChannel configuration using show commands and test the link aggregation for increased bandwidth and redundancy.
69) How Would you Configure Inter-VLAN Routing Using a Layer 3 Switch?
Answer: To configure inter-VLAN routing using a Layer 3 switch you have to do the following:
a) The VLANs must be created on the Layer 3 switch.
b) Assign the VLAN interfaces (SVIs) with IP addresses, one for each VLAN.
c) Enable routing on the Layer 3 switch.
d) Configure VLAN Access Control Lists (VACLs) or implement firewall rules to control traffic between VLANs.
e) Ensure that the devices on each VLAN have their default gateway set to the IP address of the corresponding VLAN interface on the Layer 3 switch.
70) Define CDP and its Functions.
Answer: Cisco Discovery Protocol (CPD) stands as a pivotal Layer 2 networking protocol in the world of Cisco devices. It operates in a media-independent and network-independent manner, providing an invaluable service by allowing the discovery of Cisco devices across a network. It plays a crucial role in the efficient management of Cisco devices by not only locating them but also assisting in their configuration. This protocol paves the way for systems to gain insights into one another through various network-layer protocols. Some of its important functions include the following:
a) Collecting information: CDP serves as an information gatherer aboutneighbouring devices that are directly connected to it and improves network visibility.
b) Identifying adjacent Cisco Devices: It excels in pinpointing adjacent Cisco devices in the network topology and contributes to network mapping and troubleshooting.
c) Detail extraction: CDP goes beyond basic discovery by extracting a wealth of information, including port numbers, IP addresses, router and switch models, interface specifics, iOS version details, and device ID-hostnames. This comprehensive data helps in configuration and monitoring.
d) Inventory management: One of its key roles is simplifying the task of maintaining an up-to-date list of Cisco network devices. This not only ensures accuracy but also streamlines Network Management.
e) Sharing vital data: CDP doesn't just keep insights to itself; it actively shares crucial information about other directly connected Cisco equipment. This includes data like the operating system version and IP addresses, which further enhance network intelligence and help in efficient resource allocation.
Learn to design, install, and support networks for organisations by signing up for our CCNA Certification now!
71) What is Routing?
Answer: Routing involves identifying the optimal path for data to travel from its source to its destination. This task is performed by a device called a router, which operates at the network layer.
72) What is BootP?
Answer: BootP, short for “Boot Program,” is a protocol primarily used to boot diskless workstations connected to a network. Additionally, a diskless workstation can use BootP to ascertain its IP address and the IP address of the server PC.
73) What is PoE?
Answer: Power over Ethernet (PoE) is a technology that enables network cables to transmit electrical power, allowing devices such as IP cameras and wireless access points to receive both data and power through a single cable. This simplifies installation and eliminates the need for separate power sources.
Conclusion
With these top CCNA Interview Questions and Answers, you’re now equipped to tackle your interview with confidence and clarity. Dive deep into these questions, understand the concepts, and be ready to impress your interviewer. Best of luck on your journey to becoming a certified networking professional!
Level up your networking skills with Cisco Packet Tracer Course - sign up now!
Upcoming IT Infrastructure & Networking Resources Batches & Dates
Date
 CCNA Certification
CCNA Certification
Mon 31st Mar 2025
Mon 21st Jul 2025
Mon 17th Nov 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


