We may not have the course you’re looking for. If you enquire or give us a call on 44 1344 203 999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Imagine this: Data is the new gold, and protecting it is essential. So, what’s the ultimate solution for safeguarding it in our data-driven world? Enter the ISO 27001 Information Security Policy—your organisation’s ultimate guide to securing data like never before. This globally recognised standard helps businesses establish a robust security framework, focusing on confidentiality, integrity, and availability. This blog will dive into how this policy can help organisations foster a security-first culture!
Table of Contents
1) What is the ISO 27001 Information Security Policy?
2) What are the Three Principles of Information Security?
3) What is the Purpose of the ISO 27001 Information Security Policy?
4) What Should Your Information Security Policy Framework Include?
5) What are the Requirements for an ISO 27001 Information Security Policy?
6) How to write an ISO 27001 Information Security Policy?
7) Conclusion
What is the ISO 27001 Information Security Policy?
The ISO 27001 Information Security Policy is a compulsory document needed to gain ISO 27001 compliance. It’s used to define the leadership and commitment of an organisation’s top management to the Information Security Management System (ISMS). The Information Security Policy is a high-level policy that establishes the management approach of the organisation, and includes some key elements such as management and leadership. This document can be shared with an organisation's staff to explain their roles and responsibilities and with customers to assure them that you are doing the right thing.
As a part of Clause 5 of the ISO 27001 Framework, you will be asked to clearly define your Information Security policy and objectives. Your Information Security policy should showcase your commitment to any action that will improve the security of your organisation’s sensitive information resources.
The Information Security policy is pivotal in bridging the connection between your top management and the Information Security controls. The ISO 27001 Checklist requires management to ensure that the objectives of the ISMS are compatible with the company's long-term strategic vision (5.2 of the ISO 27001 compliance framework). This is why you should try to keep the Information Security Policy short and easily understandable for your organisation’s upper management.
What are the Three Principles of Information Security?
Confidentiality, integrity and availability (CIA) are the three Information Security principles that protect your data from unwanted access. These principles are explored below:
1) Confidentiality: The confidentiality principle concerns information being protected from unauthorised use, access or disclosure. Information must be accessed only by authorised people and systems, who must know what you're sending them and how it can be used for their respective purposes.
2) Integrity: The integrity principle ensures that data remains accurate and unchanged if it's accessed by anyone with whom you've shared it. This implies that you must keep track of any changes to your data to maintain its consistency with its original form in case another attempt is made to change it.
3) Availability: The availability principle concerns the users' ability to access their data when needed, whether through automatic backups or manual syncing between users or devices.
What is the Purpose of the ISO 27001 Information Security Policy?
An ISO 27001 Information Security Policy is necessary because your organisation processes, stores, and transmits important data and valuable information. To truly understand the value of an Information Security policy, we will break down the data we are protecting into three parts:
a) Customer Data: Whatever an organisation’s product or service is, it is going to be handling customer data bearing some description. The customer data could be customers' personal information, order information or technical information. What’s fundamental is that your customer cares about and wants the information to be protected.
b) Employee Data: Any organisation, irrespective of its size, hosts a number of employees. The organisation naturally has access to all of its employees’ personal information, such as names, addresses, bank details, social security and tax information and much more. Employees care deeply about the safety and protection of their personal information, and an organisation should always look to protect their employees’ best interests.
c) Company Data: Lastly, an organisation has sensitive information that it needs to protect. A company has financial data relating to performance, customer databases relating to customer relationship management, and plenty of intellectual data for other purposes. Therefore, data protection is important for the organisation, and compliance with a security standard is necessary to strengthen its security.
Sign up for our ISO 27001 Lead Auditor Course and safeguard your organisation against cyber threats - register now!
What Should Your Information Security Policy Framework Include?
Your Information Security policy should have the basic ISO 27001 Information Security framework clearly defined. Your Information Security policy framework must include the following elements:
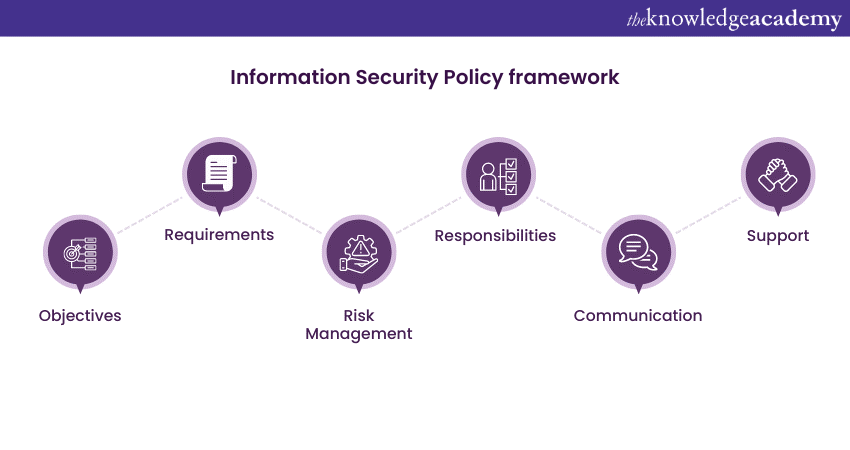
Your Information Security policy should have the basic ISO 27001 Information Security framework clearly defined. Your Information Security policy framework must include the following elements:

1) Objectives: The general objectives to be achieved by Information Security must be defined very clearly in the Information Security policy framework.
2) Requirements: The ISO 27001 Requirements section of your Information Security policy framework must include a reference to the legal, statutory, regulatory and contractual requirements that must be fulfilled.
3) Risk Management: The Risk Management section of your Information Security policy framework should refer to the process used to select the Information Security controls.
4) Responsibilities: This part of the Information Security policy framework must include clearly defined roles and responsibilities for the implementation, maintenance and reporting of the ISMS’s performance.
5) Communication: Next, your Information Security policy framework must define to whom the policy needs to be communicated.
6) Support: Lastly, your Information Security policy framework must showcase its commitment to implement the right resources and improve Information Security.
Though it is not mandatory, if you are a smaller-scale organisation, you may also include the following (for larger-scale companies, these issues are documented separately):
a) The Scope of the ISMS: The scope of ISMS can be defined as part of the Information Security policy so that it does not need to exist as a separate document.
b) Measurement: This section of the Information Security policy has a clear definition of who will measure whether the Information Security objectives of the organisation have been achieved, to whom the results need to be reported and how often, etc.
However, in some larger companies, the ISO 27001 Information Security Policy may merge with the Enterprise Risk Management Policy. Although it is not wrong per se, it is better to separate these policies as different documents as the focus remains much clearer and coherent.
Want to enhance your organisation's security measures? Sign up for our comprehensive ISO 27001 Internal Auditor Course now!
What are the requirements for an ISO 27001 Information Security Policy?
ISO 27001 Latest Version, does not expand too much on the policy, but it does stipulate the following requirements and elements to consider when writing the policy:

a) Adapt the Policy to the Organisation: The policy needs to be adapted to the organisation. This essentially means that one cannot simply copy the policy from a large organisation and use it in a much smaller organisation.
b) Define the Framework for Setting Objectives: The policy needs to define the framework for setting up ISO 27001 physical security objectives. In simpler terms, the policy needs to define how the Information Security objectives are proposed, approved, and reviewed.
c) Establish a Commitment Statement for the Top Management: The policy must demonstrate the commitment of upper management to help fulfil the requirements of all interested parties and continuously improve the ISMS. This is usually done through a statement included as part of the policy.
d) Define Responsibilities for Communication: The policy must be communicated within the organisation and to interested parties, e.g., customers and suppliers, whenever appropriate. The best practice is clearly defining who is responsible for such communication and ensuring they regularly communicate with all relevant parties.
e) Ensure Regular Reviews by Defining the Owner of the Policy: Lastly, the policy must be reviewed on a regular basis (e.g., annually). The owner of the policy should be clearly defined, and the person concerned is held responsible for keeping the policy up to date.
Want to master the art of Information Security Management? Elevate your skills with our ISO 27001 Certification for a safer digital future.
How to Write an ISO 27001 Information Security Policy?
Writing an ISO 27001 Information Security Policy involves several steps to ensure it meets the standard’s requirements and effectively protects your organisation’s information assets. Here’s a structured approach that will get you started:
1) Define the Purpose: State the policy's purpose clearly to outline the organisation’s approach to managing Information Security.
2) Specify the Scope: Specify the policy's scope, including the systems, departments, and processes it covers.
3) Management Commitment: Include a statement from top management expressing their commitment to ISO 27001 compliance and Information Security.
4) Information Security Objectives: Define clear and measurable objectives that align with the organisational goals.
5) Roles and Responsibilities: Outline every role and responsibility of management, employees, and other stakeholders who will play big hands in maintaining Information Security.
6) Policy Framework: Describe the framework for managing Information Security, including risk assessment and continuous improvement processes.
7) Confidentiality, Integrity, and Availability (CIA): Elucidate how the policy ensures information confidentiality, integrity, and availability. This includes data protection measures, access controls, and incident response procedures.
8) Compliance Requirements: It's essential to explain how the organisation will meet regulatory, legal and contractual requirements related to Information Security.
9) Communication and Training: You must specify how the policy will be communicated to employees and how their training on Information Security responsibilities will unfold.
10) Review and Update: You must establish a process for regular review and update of the policy to ensure it remains aligned with any organisational or external changes.
This is the general structure you can follow when writing the policy:
1) Introduction
2) Purpose
3) Scope
4) Definitions
5) Roles and Responsibilities
6) Information Security Objectives
7) Policy Statements
a) Access Control
b) Data Protection
c) Compliance
d) Incident Management
8) Communication and Training
9) Review and Update
Conclusion
All in all, an organisation must include its ISO 27001 Information Security Policy to gain compliance with the ISO 27001 global standard. The policy must be a clearly defined and concise document that outlines the organisational Information Security objectives and establishes roles and responsibilities within the company. A precise Information Security policy helps an organisation comply with the Key Features of ISO 27001 standards and protect its information resources better.
Level up your Cybersecurity expertise with our ISO 27001 Foundation training and gain the skills to protect your organisation today!
Frequently Asked Questions

The 7 P’s of Information Security Management are:
a) Planning
b) Policy
c) Programs
d) Protection
e) People
f) Processes
g) Project Management

Technically, Cyber Security is a subset of Information Security. However, these fields have distinct features and require different skill sets.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various ISO 27001 Courses including the ISO 27001 Foundation Course and the ISO 27001 Lead Auditor Course. These courses cater to different skill levels, providing comprehensive insights into ISO 27001 Framework.
Our ISO & Compliance Blogs cover a range of topics related to ISO 27001, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your ISO knowledge base, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 ISO 27001 Foundation
ISO 27001 Foundation
Mon 10th Feb 2025
Mon 17th Mar 2025
Mon 12th May 2025
Mon 7th Jul 2025
Mon 1st Sep 2025
Mon 10th Nov 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


