We may not have the course you’re looking for. If you enquire or give us a call on +1 7204454674 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Today, we live in the digital eco-space where Web Applications are pivotal in Business Operations, communication, and data storage. However, their ubiquity also makes them prime targets for malicious attacks. This is where Web Application Penetration Testing comes into play.
Web Application Penetration Testing mainly focuses on finding security weaknesses in Web Applications. Thus, it is crucial to get familiar with this type of Testing to eliminate all types of malicious activities and protect organisational data. Read this blog to explore the meaning of Web Application Penetration Testing, its importance, methodologies, key steps, and best practices.
Table of Contents
1) What is Web Application Penetration Testing?
2) Importance of Web Application Penetration Testing
3) Web Application Penetration Testing methodologies
4) Top Penetration Testing tools
5) How to perform Web Application Penetration Testing?
6) Conclusion
What is Web Application Penetration Testing?
Web Application Penetration Testing goes beyond traditional Vulnerability Scanning. While Vulnerability Scanning identifies known vulnerabilities in an automated manner. While Penetration Testing seeks to uncover not only known vulnerabilities and undiscovered weaknesses that automated tools might miss.
Further, it controls the actions of an attacker by attempting to exploit these vulnerabilities and gain unauthorised access to the application. Its ultimate aim is to uncover how far an attacker could potentially penetrate the system.
Importance of Web Application Penetration Testing
The widespread use of Web Applications for critical tasks such as financial transactions, data storage, communication, and collaboration makes them prime targets for malicious cyberattacks. This is where Web Application Penetration Testing emerges as a critical line of defence, playing a pivotal role. Want to know how? Here are some reasons why Web Application Penetration Testing is crucial:

Prevents data breaches
Data breaches can have catastrophic consequences for organisations, leading to financial losses, legal liabilities, and severe damage to reputation. Web Application Penetration Testing identifies vulnerabilities that could lead to unauthorised access, data leakage, and the exposure of confidential information. By uncovering these weaknesses before they are exploited, organisations can implement timely measures to mitigate the risk of data breaches.
Safeguards brand reputation
A company's reputation can be its most valuable asset in today’s era. A security breach can tarnish a brand's image and erode customer trust, potentially leading to loss of business and revenue. Web Application Penetration Testing aids in preventing such breaches, demonstrating an organisation's commitment to security and bolstering customer confidence.
Proactive Risk Management
Proactive Risk Management involves identifying vulnerabilities and assessing their potential impact on the organisation. Web Application Penetration Testing goes beyond listing vulnerabilities; it helps organisations understand what could lead to the most severe consequences. This understanding allows organisations to prioritise remediation efforts effectively, focusing on the vulnerabilities that pose the greatest threat.
Strengthens security
Web Applications are complex systems with vulnerabilities arising from coding errors, misconfigurations, or inadequate security measures. Penetration Testing proactively identifies these vulnerabilities, enabling organisations to prioritise remediation efforts and enhance security.
By continually conducting Penetration Testing, organisations can stay ahead of evolving cyber threats. As new vulnerabilities and attack vectors emerge, Penetration Testing helps organisations stay vigilant, adapt to changing tactics, and implement necessary security updates.
Protects user privacy
User privacy is paramount, especially in applications that handle personal and sensitive data. Penetration Testing recognises vulnerabilities that could lead to unauthorised access to user information, ensuring that personal data remains confidential and secure.
Uncovers hidden vulnerabilities
Web Application Penetration Testing aims to expose vulnerabilities that automated tools might overlook. Testers can discover weaknesses that determined attackers could exploit by simulating real-world attack scenarios.
Unlock the power of Cyber Security with our Ethical Hacking and Penetration Testing Training – become the shield against digital threats!
Web Application Penetration Testing methodologies
Web Application Penetration Testing is a multidimensional process that requires careful planning, execution, and analysis. Different methodologies are employed to effectively assess the security of Web Applications, each with its approach, advantages, and limitations. These methodologies with the help of specialised penetration testing tools allow Testers to uncover vulnerabilities, weaknesses, and potential entry points that malicious threats could exploit. Here’s is the list of some methodologies used in Penetration Testing of Web Applications:
Black Box Testing
Black Box Testing, often called External Testing, simulates an attacker with no prior knowledge of the internal workings of the Web Application. Testers approach the application from an outsider's perspective, attempting to identify vulnerabilities and weaknesses solely by observing the application's inputs, outputs, and behaviours. This methodology replicates how an external attacker might approach the application. The following are some advantages of Black Box Testing:
a) Reflects a real-world scenario, as attackers typically lack insider knowledge.
b) Reveals vulnerabilities that can be exploited through publicly accessible interfaces.
c) Identifies user-facing vulnerabilities that can impact the application's user base.
The following are some limitations of Black Box Testing:
a) It may not identify vulnerabilities that require knowledge of the application's internal logic.
b) Limited insight into application architecture may result in overlooking specific vulnerabilities.
c) It relies heavily on Manual Testing, potentially requiring more time and resources.
White Box Testing
White Box Testing, also called Internal Testing or Clear Box Testing, grants Testers full access to the application's source code, architecture, and internal workings. This methodology allows them to comprehensively analyse the application's codebase, making it possible to uncover vulnerabilities that might not be evident through other testing methods. Here are some advantages of White Box Testing:
a) Provides deep insight into the application's code, logic, and architecture.
b) Identifies vulnerabilities that are only visible when reviewing the source code.
c) Uncovers complex vulnerabilities that might not be discovered using other methodologies.
Here are some disadvantages of White Box Testing:
a) It may not fully replicate the perspective of an external attacker.
b) Requires access to the application's source code, which might only sometimes be available.
c) It can be time-consuming and resource-intensive due to in-depth code analysis.
Gray Box Testing
Gray Box Testing is a mixed approach that utilises both White Box and Black Box Testing elements. Testers need to gain more knowledge about the application, such as access to specific code snippets, documentation, or insights into the application's architecture. This approach seeks to balance between simulating real-world scenarios while leveraging some understanding of the application's internals. The following are some advantages of Gray Box Testing:
a) Provides a more comprehensive assessment than Black Box Testing alone.
b) Allows Testers to target specific areas of the application based on limited information.
c) Balances the benefits of both Black Box and White Box Testing methodologies.
The following are some disadvantages of Gray Box Testing:
a) It requires careful planning to determine the Testers' knowledge level.
b) Testers may still need vulnerabilities that require a deeper understanding of the application's internals.
c) It relies on Testers' judgment to strike the right balance between limited knowledge and practical testing.
Top Penetration Testing tools
Here is a list of the top tools used to perform Web Application Penetration Tests:
1) W3af
Web Application Framework 300, or W3af, is a powerful Web Application attack and audit framework that aids in identifying and exploiting vulnerabilities in Web Applications. It offers a user-friendly interface and supports various attacks, including SQL injection, cross-site scripting (XSS), and Remote File Inclusion (RFI).
2) Burp Suite
Burp Suite is a leading web vulnerability scanner and security testing tool used by security professionals to identify, scan, and exploit Web Application vulnerabilities. It provides a comprehensive set of features for Web Application Testing, including manual and automated testing, intercepting proxies, and advanced scanning capabilities.
3) SQLMap
SQLMap is an open-source Web Penetration Testing Tool designed to detect and exploit SQL injection vulnerabilities in Web Applications. It automates identifying SQL injection flaws and extracting sensitive information from databases, making it an essential tool for Web Application Security Testing.
4) Metasploit
Metasploit is one of the most powerful Penetration Testing Tools. It enables security professionals to conduct advanced Penetration Testing, exploit development, and vulnerability research. It provides a comprehensive set of tools for identifying, manipulating, and remediating security vulnerabilities across various systems and applications.
5) Hydra
Hydra is a popular password-cracking tool that allows security professionals to perform brute-force attacks against various authentication protocols, including HTTP, FTP, SSH, and more. It supports multiple attack modes and can be customised to target specific usernames, passwords, and authentication methods.
6) John Ripper
John the Ripper is a fast password cracker designed to help security professionals identify weak passwords and perform password auditing. It supports various password-cracking techniques, including dictionary attacks, brute-force attacks, and rainbow table attacks, making it a versatile tool for password security testing.
7) Skipfish
Skipfish is an automated Web Application Security scanner designed to quickly identify security vulnerabilities in Web Applications. It performs comprehensive security checks, including input validation testing, error handling analysis, and security header verification, to help security professionals identify and remediate vulnerabilities effectively.
8) Ratproxy
Ratproxy is a passive Web Application Security assessment tool that intercepts and analyses HTTP and HTTPS traffic between web clients and servers. It identifies potential security vulnerabilities, such as cross-site scripting (XSS) and SQL injection, by examining the Web Application's behaviour and identifying abnormal patterns in the traffic.
9) Wfuzz
Wfuzz is a Web Application Security Testing tool designed to identify and exploit vulnerabilities in Web Applications through brute-force attacks and fuzzing techniques. It supports various attack modes, including directory brute-forcing, parameter fuzzing, and authentication testing, making it a versatile tool for Web Application Security Testing.
10) Watcher
Watcher is a passive web vulnerability scanner that monitors and analyses HTTP and HTTPS traffic between web clients and servers to identify potential security vulnerabilities. It focuses on detecting common Web Application Security flaws, such as cross-site scripting (XSS), SQL injection, and security misconfigurations, to help organisations improve their Web Application Security posture.
How to perform Web Application Penetration Testing?
Web Application Penetration Testing involves a systematic and structured approach to identifying vulnerabilities and assessing the security of Web Applications. This process is designed to simulate real-world cyberattacks, helping organisations uncover weaknesses that malicious actors could exploit. The following are the critical steps involved in Web Application Penetration Testing:
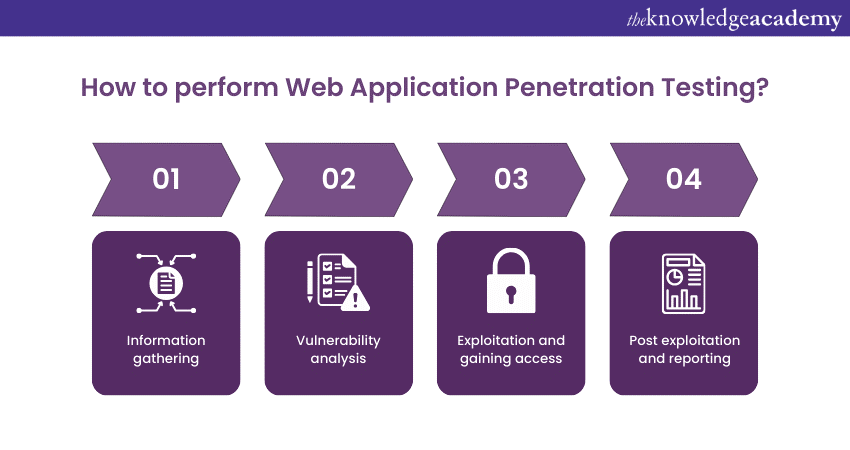
Information gathering
The initial phase involves collecting information about the target Web Application. Testers seek to understand the application's architecture, technologies used, communication channels, and potential attack surfaces. This phase may include domain enumeration, network scanning, and identifying publicly accessible components. While gathering information, Testers utilise tools, including WHOIS databases, DNS enumeration tools, and network scanners.
Vulnerability analysis
In this phase, Testers analyse the information gathered to identify potential vulnerabilities. They scrutinise the application's input fields, authentication mechanisms, session management, and data handling processes. This step aims to discover vulnerabilities like injection attacks, cross-site scripting (XSS), and security misconfigurations. Testers use tools like automated vulnerability scanners, manual code review, and security analysis tools.
Exploitation and gaining access
After identifying vulnerabilities, Testers exploit them to gain unauthorised access to the application or its underlying systems. This step helps them determine the extent to which an attacker could compromise the application's security. Testers aim to access sensitive data, escalate privileges, or execute arbitrary code. To exploit access, they use tools such as exploitation frameworks, scripting languages, and Penetration Testing tools.
Post exploitation and reporting
Once access has been gained, Testers assess the impact of the successful exploitation. They evaluate what actions an attacker could perform with the access obtained, such as data manipulation, lateral movement, or further systems compromise. A comprehensive report is then prepared, describing the vulnerabilities discovered, their potential impact, and recommendations for remediation. Lastly, they provide insights about the attack in the form of a detailed report outlining vulnerabilities, exploitation steps, and recommendations.
Register for our Web Application Testing With PHPUnit Framework Course for a rewarding career in Penetratio0n Testing!
Conclusion
As technology evolves, the tactics of cyber attackers also keep pace with it. New vulnerabilities emerge, and novel attack vectors are constantly developed. This reality underscores the perpetual need for Web Application Penetration Testing. Organisations must recognise that security is not a one-time event; it's a never-ending process that requires continuous monitoring, testing, and improvement.
Learn how to secure your digital fortress by joining our Tools and Techniques of Penetration Testing Course today!
Frequently Asked Questions

A Web Application Penetration Test is a security assessment conducted to identify vulnerabilities and weaknesses in Web Applications. It involves simulating real-world attacks to assess the security posture of Web Applications and ensure they are protected against potential threats and exploits.

Web Application Penetration Testing methods include Black Box Testing, where Testers have no prior knowledge of the system; White Box Testing, with full system knowledge; and Gray Box Testing, which combines elements of both approaches to simulate real-world attack scenarios effectively.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Automation & Penetration Testing Courses, including Tools and Techniques for Penetrating Testing, Fundamentals of Test Automation, etc. These courses cater to different skill levels, providing comprehensive insights into Cyber Security Skills.
Our IT Security & Data Protection Blogs cover a range of topics related to the Fundamentals of Test Automation, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your IT skills, The Knowledge Academy's diverse courses and informative blogs have you covered.
Upcoming Business Analysis Resources Batches & Dates
Date
 Software Testing Automation Course
Software Testing Automation Course
Thu 6th Feb 2025
Thu 3rd Apr 2025
Thu 8th May 2025
Thu 10th Jul 2025
Thu 18th Sep 2025
Thu 6th Nov 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


