We may not have the course you’re looking for. If you enquire or give us a call on +1 7204454674 and speak to our training experts, we may still be able to help with your training requirements.
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

In today’s digital battlefield, ISO 27001 Certification goes beyond just a luxury! Every year, countless organisations fall prey to devastating security breaches, leaving behind financial losses and tarnished reputations.
But knowing What is ISO 27001 isn’t just about protecting your data. It’s a badge of trust that reassures your clients and stakeholders that their information is in safe hands.
So, ready to take your information security to the next level? Dive into this insightful blog and unlock the full potential of ISO 27001. Discover its benefits, importance, compliance requirements, and much more. Let's commence our breathtaking journey!
Table of Contents
1) What is ISO 27001?
2) Working of ISO 27001
3) The Benefits of ISO 27001
4) The Principles of ISO 27001
5) The 14 Phases of ISO 27001
6) What is Information Security Management Systems (ISMS)?
7) Requirements of ISO 27001
8) Other Supporting ISO Standards
9) Conclusion
What is ISO 27001?
ISO 27001 is a renowned Information Security Management Systems (ISMS) standard, primarily focusing on safeguarding the information security of an organisation. In simple terms, ISO 27001 provides a systematic framework to protect an organisation's confidentiality, integrity, and availability. By implementing this standard, organisations can establish robust defences to effectively safeguard their data from malicious actors.
ISO 27001 Physical Security provides a competitive edge to the organisation's security, offering a complete package of detailed instructions. These instructions focus on creating, applying, maintaining and upgrading the organisation's security.
Creating and executing effective ISMS can vary based on criteria such as organisation’s business goals and requirements, security needs, work procedures, and organisation’s capacity.
The Purpose of ISO 27001
a) ISO 27001 ensures the confidentiality, integrity, and availability of information.
b) It offers a structured framework for managing Information Security risks.
c) It helps organisations comply with legal, regulatory, and contractual requirements.
d) It improves stakeholder trust by demonstrating a commitment to data security.
e) It supports business continuity by mitigating security threats and vulnerabilities.
f) It improves operational efficiency through a systematic approach to information security (InfoSec).
Essentially, ISO 27001 issues a framework for protecting organisational information in an organised and affordable way and can be implemented in any organisation regardless of size.
The Importance of ISO 27001
a) ISO 27001 certification showcases an organisation’s security capability, boosting client trust and reputation.
b) Countries like United Kingdom, Canada, United States, Japan and Australia have mandate for ISO certifications.
c) ISO certifications may be mandatory for running a businesskISO certifications may be mandatory for running a businessiISO certifications may be mandatory for running a businesslISO certifications may be mandatory for running a business ISO certifications may be mandatory for running a businesssISO certifications may be mandatory for running a businesseISO certifications may be mandatory for running a businessiISO certifications may be mandatory for running a businessrISO certifications may be mandatory for running a businesstISO certifications may be mandatory for running a businessnISO certifications may be mandatory for running a businessuISO certifications may be mandatory for running a businessoISO certifications may be mandatory for running a business
d) ISO 27001 provides foundational knowledge for data protection.
e) Compliance with regulatory requirements is a key feature of ISO 27001, influencing business partnerships.
f) The certification ensures high-quality, trustworthy, and stable processes and tools.
g) As a globally recognised standard, ISO 27001 can enhance business potential.
h) Individuals can obtain ISO 27001 certification to demonstrate their ability to audit ISMS.
i) Earning the certification increases hiring opportunities, though passing an exam is required.
Working of ISO 27001
The primary goal of ISO 27001 is to protect an organisation's information systems, confidentiality, integrity and availability. ISO 27001 Physical and Environmental Security aims to achieve these goals through the following ways:
1) ISO 27001 conducts a thorough Risk Assessment across the organisation.
2) It identifies areas of weakness where security breaches could occur.
3) The assessment helps determine necessary actions to prevent security incidents.
So, ISO 27001 Compliance is a very effective process for Risk Management. It works by finding out where potential risks could come from and eliminating them.

Signup for our ISO 27001 Training and learn about the global standard for ISMS.
The Benefits of ISO 27001
There are many advantages of the ISO 27001 certification, such as increased security and reduced operating costs. Some of its other essential benefits are listed below:

Mitigate Risks
From hacking to malware, there are many risks to an organisation's security. In today's world, data is considered the new gold. The difference, though, is pirates in those days wore eye patches, but pirates these days sit behind a computer screen.
a) A data breach can severely damage an organisation’s reputation.
b) The company must bear the cost of fixing the breach and strengthening security.
c) Businesses recognise the financial and reputational risks of security breaches.
d) Organisations adopt ISO 27001 to establish a standardised security framework.
e) Public and private institutions use ISO 27001 to enhance security, regardless of size.
Improves Trust and Reputation
A security breach can jeopardise an organisation, leaking valuable data and damaging its reputation. ISO 27001 ISMS helps prevent such incidents through risk assessments, identifying vulnerabilities early. Trust is key in business, and an ISO 27001-certified ISMS demonstrates effective Security Management.
The certification assures stakeholders that security measures are independently verified, enhancing confidence. External audits validate controls, fostering transparency and continuous improvement in Information Security, making organisations more resilient against cyber threats.
Budget-friendly
ISO 27001 emphasises the principle that prevention is better than cure by proactively addressing information security risks. For an organisation, client data, intellectual data and other internal documents are invaluable.
These are the key points to remember:
a) Breach of data would result in the company bearing the cost.
b) Implementing ISO 27001 is a budget-friendly approach to security.
c) ISO 27001 helps deploy systems and plans for managing security incidents in advance.
d) ISO 27001 systems thoroughly assess the organisation's security needs.
e) A Risk Management plan is produced based on the ISO 27001 assessment.
f) Regular internal audits ensure ongoing compliance.
g) The latest ISO 27001 version ensures up-to-date security measures.
h) The company can effectively manage and mitigate security threats using ISO 27001.
Sign up for our course on ISO 27001 Internal Auditor Course and learn how to perform internal audits and secure ISMS.
The Principles of ISO 27001
There are three vital principles of ISO 27001, the standard for Information Security. Implementing these principles can help in the right utilisation of ISMS effectively to reduce security-related incidents. The three underlying principles of ISO 27001 are described as follows:
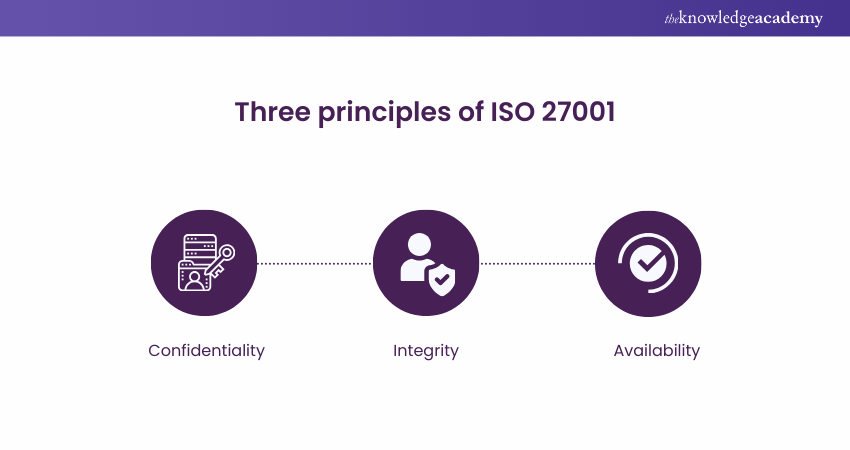
a) Confidentiality: The first and foremost principle of ISO 27001 is keeping information confidential. It doesn’t matter if it’s the organisational information or its of clients and partners; it should remain confidential.
b) Integrity: The second principle is to maintain the integrity of the organisational data. Whether storing in a secure place or moving around, it must be ensured that no one can modify it. However, changes should be made only with proper authorisations, and a backup must be created and maintained for the original data.
c) Availability: The third principle is ensuring data access to the right person. If an authorised person wants access to data, it should be readily available to them. In addition, it is also about securing and preventing access from unauthorised personnel.
The 14 phases of ISO 27001
ISO 27001 has a comprehensive framework helping organisations maintain a secure ISMS and is divided into the following 14 phases:
1) Information Security (InfoSec) policy
2) Organisation of Information Security
3) Risk Assessment and treatment
4) Asset Management
5) Access control
6) Cryptography
7) Physical security
8) Operations security
9) Communications security
10) System acquisition, development and maintenance
11) Supplier relationships
12) Compliance with legal requirements and industry standards
13) Information Quality Management (IQM)
14) Risk Monitoring and review
Sign up for our ISO 27001 Foundation Course and acquire foundational knowledge on ISO 27001 & Information Security.
What is Information Security Management Systems (ISMS)?
The ISMS is a set of right procedures and techniques for managing sensitive information. An effective ISMS can prevent security breaches in advance, mitigating the risks and assuring business continuity.

The Importance of Information Security Management Systems
Implementing ISMS can have a lot of benefits for an organisation from compliance requirements to robust security structure. Let's learn why using ISMS is crucial for an organisation:
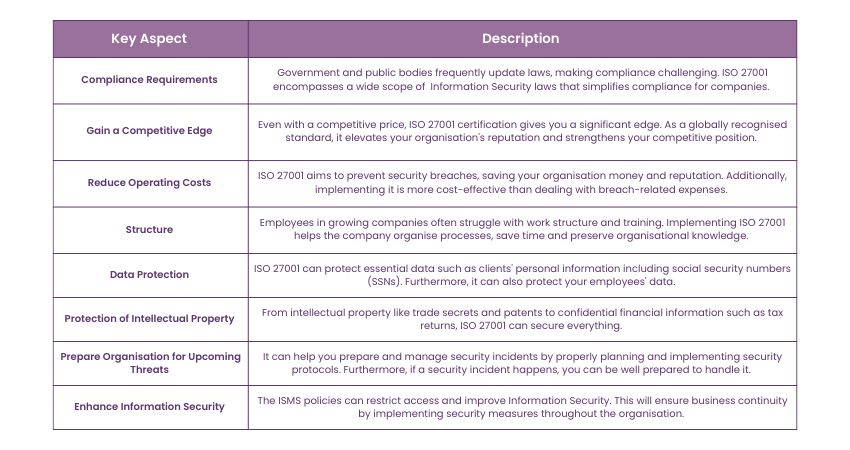
Sign up for our ISO 27001 Lead Implement Training and learn everything about the global standard for information security management systems.
Requirements of ISO 27001
ISO 27001 is divided into two parts:
1) The first includes 11 clauses:
a) Clauses 0-3 covers introduction, terms, references, and scope
b) Clauses 4-10 focuses on compliance requirements.
2) The second part, Annexure A, provides guidelines for 93 control objectives and is optional, addressing Risk Management.
Necessary Requirements
There are many benefits to getting ISO 27001 compliance. In this section, Let's learn about clauses four to ten necessary ISO 27001 Requirements to achieve ISO 27001 compliance:
a) Clause 4
Before defining the ISMS scope, it is necessary to understand the organisation's context. First, identify any internal and external problems. These issues can be anything from a simple regulatory issue to a much more severe issue.
b) Clause 5
This clause primarily focuses on the leadership aspect of an organisation. Effective Information Systems Management is dependent on the Upper Management's commitment. These objectives could be anything from supporting the people who contributed to the ISMS to supplying the resources necessary for the ISMS.
c) Clause 6
It is all about planning the security policy. While planning, you should consider the risks and opportunities involved. The risks can be identified by conducting a risk assessment. It will give a basic idea of how to create a security policy. An organisation's information security goals should rely on risk assessment. These goals should also align with the organisation's primary goals and be informed throughout the company.
d) Clause 7
This clause focuses on the support aspect of the ISMS. Proper documentation of information using the ISO 27001 guidelines is essential. Maintaining documentation improves the chances of ISMS success. Other key supporting factors include resources, the ability of employees, knowledge, and dialogue.
e) Clause 8
This clause is all about the operations and processes necessary to implement Information Security. The Upper Management should focus on the processes like planning, risk assessment and mitigation to implement the organisation's security policy.
f) Clause 9
Perhaps the most important requirement of ISO 27001 is performance evaluation. It involves tracking, evaluation, and analysis of the ISMS. You can evaluate other performance-related metrics with internal audits. The Upper Management should frequently evaluate the performance of ISMS.
g) Clause 10
Once the performance evaluation is completed, you will have to look at ways to improve it. Anything that hinders the performance of the ISMS should be removed with proper measures. This will further improve the performance and ensure business continuity.
How to Fulfil These Requirements and Achieve ISO 27001 Compliance?

Getting an ISO Certification like ISO 27001 is a big commitment and requires a lot of work. However, once certified, its benefits can outweigh the efforts. It involves an extensive review of the organisation's ISMS and whether it can fulfil the specific requirements of ISO.
The process involves a third-party review done by an authorised Auditor. This Auditor often an ISO 27001 Lead Auditor will thoroughly check the ISMS and test whether it can comply with the standard. Based on the assessment, the Auditor will suggest changes that can amplify an ISMS's effectiveness. These suggestions will also help achieve ISO 27001 compliance. Once all the requirements are fulfilled, your organisation will receive ISO 27001 Certification from the authorised body.
Advance your Cybersecurity proficiency with our ISO 27002 Training Register now!
Other Supporting ISO Standards
ISO 27001 Framework is considered an important standard among the ISO 27000 Standards. It specifies what is necessary to achieve and how to achieve it. Many frameworks have been developed to overcome this problem and give more guidelines. There are many supporting Standards available for ISO 27001. These standards capitalise on areas that ISO 27001 doesn’t explain in detail. Some of these Standards are listed below:
a) ISO 27002: It provides recommendations to implement the Annex A controls list. Apart from this, it also provides guidelines on how to apply these controls.
b) ISO 27004: It gives recommendations for the estimation of information security. Plus, it describes how to determine if the ISMS achieved its targets.
c) ISO 27005: It gives suggestions for Risk Management in information security. It is very similar to ISO 27001 and is considered a proper alternative. It explains how to do a risk assessment and mitigate similar risks.
d) ISO 27017: It gives instructions for information security in cloud-based systems.
e) ISO 27018: It gives suggestions for privacy protection in cloud-based systems.
f) ISO 27031: It gives recommendations for ensuring business continuity for information and communication technologies. ISO 27031 is a unique Standard connecting information security and business continuity.
Enhance your information security with the ISO 27001 Policies and Procedures PDF—download today!
Conclusion
ISO 27001 is crucial for strong Information Security Management. It helps organisations protect data, improve security, and build trust with stakeholders and clients. Understanding What is ISO 27001 is vital because it improves security, boosts reputation, and opens new business opportunities. It delivers both operational and reputational benefits while substantially reducing security risks.
Sign up for our course on ISO 27001 Lead Auditor and gain expertise in evaluating and improving Information Security practices
Frequently Asked Questions
What’s the Difference Between ISO 27001 Compliance and Certification?

ISO 27001 compliance occurs when an organisation follows the standard’s best practices without formal verification. While certification involves an accredited body auditing the organisation to confirm full adherence to ISO 27001, leading to a recognised certificate that demonstrates compliance.
How Long Will Your ISO 27001 Certification Last?

Your ISO 27001 certification is valid for three years. However, to maintain it, your organisation must undergo annual surveillance audits to ensure ongoing compliance. After the three years, a recertification audit is required to renew the certification.
What are the Other Resources and Offers Provided by The Knowledge Academy?

The Knowledge Academy takes global learning to new heights, offering over 3,000 online courses across 490+ locations in 190+ countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 19 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.
What is The Knowledge Pass, and How Does it Work?

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.
What are the Related Courses and Blogs Provided by The Knowledge Academy?

The Knowledge Academy offers various ISO 27001 Trainings, including the ISO 27001 Foundation, ISO 27001 Lead Auditor, and ISO 27001 Internal Auditor. These courses cater to different skill levels, providing comprehensive insights into ISO 27001 2022 Latest Version.
Our ISO & Compliance Blogs cover a range of topics related to Information Security and Regulatory Standards, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Compliance Management skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 ISO 27001 Foundation
ISO 27001 Foundation
Mon 14th Apr 2025
Mon 16th Jun 2025
Mon 11th Aug 2025
Mon 13th Oct 2025
Mon 8th Dec 2025






 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


