We may not have the course you’re looking for. If you enquire or give us a call on + 1-866 272 8822 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Crafting the perfect Cyber Security Resume goes beyond listing skills and experiences. It’s about strategically showcasing your prowess in defending against cyber threats. How can you highlight your ability to secure information, implement measures, and respond to breaches effectively? This blog will guide you through each essential step to ensure your resume meets industry standards and catches hiring managers' eyes.
Are you struggling with where to start? Don't worry! From creating a professional header to listing your skills and achievements, we'll cover everything you need to know. You’ll learn how to present your technical expertise and strategic thinking in a way that highlights your value to any organisation. Ready to transform your Cyber Security Resume into a powerful career tool? Let’s dive in!
Table of Contents
1) Decoding Cyber Security Resume
2) How to Write a Cyber Security Resume?
3) Common Responsibilities Listed on Cyber Security Resumes
4) Top Skills for Cyber Security Resumes
5) How to Impress with Your Cyber Security Work Experience?
6) How to Add CISSP to Your CV?
7) How to Add CISSP to Your LinkedIn?
8) Cyber Security Resume Example
9) Conclusion
Decoding Cyber Security Resume?
A Cyber Security Resume is a document that professionals in the Cyber Security field use to showcase their skills, experience, and training to potential employers. It highlights a candidate’s ability to protect secure information, install and update security software, recover data, train others on security threats, and collaborate with other IT employees.
The primary goal of a Cyber Security Resume is to demonstrate to employers that the candidate possesses the necessary security experience and programming knowledge. Additionally, it should highlight the candidate’s attention to detail, critical thinking, and decision-making skills to excel in the role.
How to Write a Cyber Security Resume?
Crafting a standout Cyber Security Resume involves several key steps. Here’s a complete guide to help you create a professional and impactful resume.
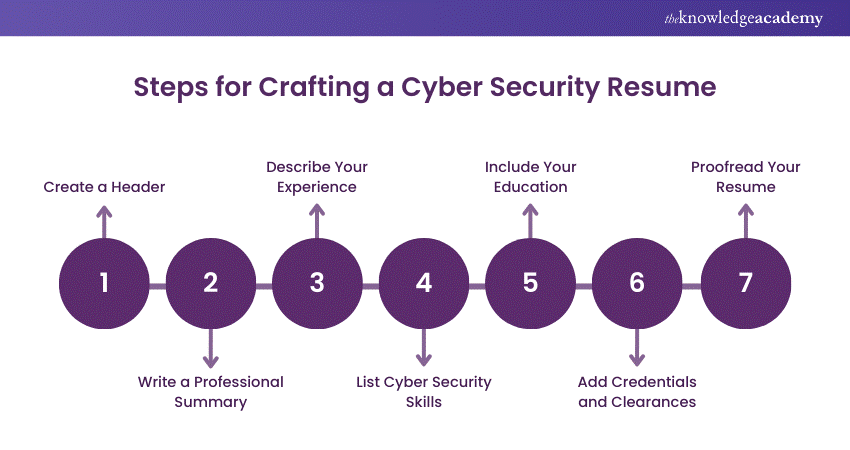
1) Create a Header
Start with a clear header at the top of the page. Use an easy-to-read font and ensure there is enough white space. Include your full name and contact information. You can list your full home address or just your city and state.
Below your location, provide your phone number and email. Additionally, include a link to your professional website or networking profile where employers can learn more about your experience and skills.
2) Write a Professional Summary
Craft a compelling professional summary to grab the hiring manager’s attention and explain why you are the best fit for the job. This should be a two to three-sentence statement highlighting your skills and experience.
A professional summary is ideal for candidates with extensive experience and should mention the skills and achievements that qualify you for the job
3) Describe Your Experience
List your past work experience, focusing on your most relevant job responsibilities and achievements. Present this information in three to five bullet points under each job title, company name, and dates worked. Use active voice to make your information confident and easy to read.
Spell out acronyms on the first reference, as the first person to read your resume might not be a technology expert. Also, Applicant Tracking Systems (ATS), which is used by many employers, might not search for acronyms. If you performed similar duties in multiple jobs, highlight different skills or functions for each role to avoid repetition.
4) List Cyber Security Skills
Employers want to know you have both the hard and soft skills needed for a Cyber Security role. Create a list of technical skills, including computer languages, platforms, and tools you are experienced with. Also, it emphasises the soft skills that are beneficial in Cyber Security roles.
Soft skills can help entry-level candidates stand out if they have fewer hard skills. For experienced candidates with many skills and qualifications, choose only the most relevant ones for the job you are applying for to avoid long lists and blocks of text.
5) Include Your Education
In the education section, list any degrees you have earned, along with the institution you attended and the date of completion. Mention relevant Cyber Security or IT coursework, such as operating systems security, cyber defence, or security design principles.
These details are particularly useful if you’re applying for an entry-level position and have more classroom hours than work experience.
6) Add Credentials and Clearances
To stand out from other candidates, seek out and list additional credentials, certifications, and security clearances in their own sections on your resume. Higher-level and government Cyber Security positions often require clearances like a Personnel Security Clearance or a Facility Security Clearance.
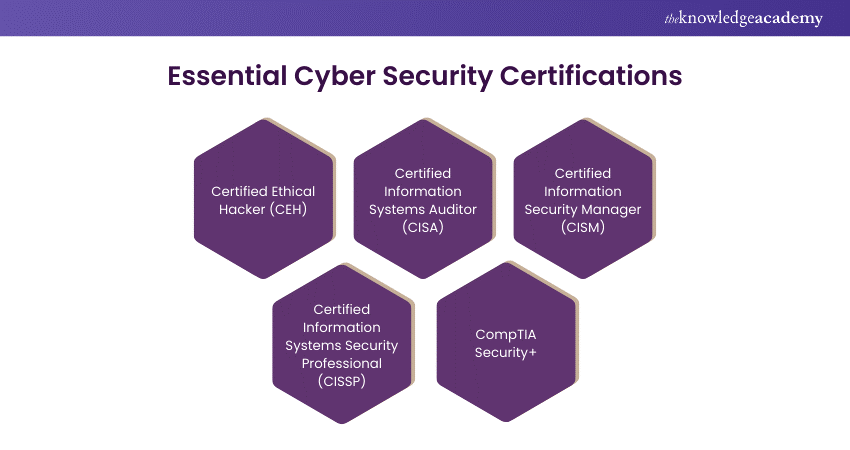
As the Cyber Security field is constantly evolving, employers may also value your commitment to continued education. List all relevant certifications you have obtained, which some companies may prioritise over a college degree. These might include:
7) Proofread Your Resume
After completing your resume, carefully proofread it to ensure correct spelling, grammar, and punctuation. Apply the same attention to detail you use in your Cyber Security work to your resume. Additionally, ask a friend or former colleague to review it for you.
Stay protected from cyber threats - join our comprehensive Cyber Security Awareness Course and secure your digital future!
Common Responsibilities Listed on Cyber Security Resumes
When detailing your work experience, it’s important to highlight the responsibilities that are commonly associated with Cyber Security roles. These might include:
a) Identify and assess potential security vulnerabilities for networks, systems, and applications.
b) Monitor and analyse security breaches, intrusions, and anomalies.
c) Respond to security alerts and incidents.
d) Perform vulnerability assessments and penetration testing.
e) Research and recommend security enhancements.
f) Configure and install security-related hardware and software.
g) Develop and maintain security documentation.
h) Ensure compliance with security policies and procedures.
i) Train users on security policies and procedures.
k) Investigate security violations and incidents.
Top Skills for Cyber Security Resumes
As a Cyber Security professional, you safeguard digital assets, networks, and systems from attacks. This role requires technical expertise, strategic thinking, problem-solving, and strong communication skills. When creating the skills section of your resume, aim to showcase a comprehensive blend of hard and soft skills.
Below are the hard and soft skills that consistently appear on the resumes of accomplished Cyber Security professionals:
Hard Skills:
a) Network Security
b) Vulnerability Assessment and Penetration Testing
c) Incident Response and Management
d) Security Information and Event Management (SIEM)
e) Encryption Technologies
f) Risk Assessment and Management
Soft Skills
a) Analytical and Problem-Solving Skills
b) Attention to Detail and Accuracy
c) Communication and Interpersonal Skills
d) Troubleshooting and Conflict Resolution
e) Critical Thinking and Decision Making
f) Strategic Planning and Execution
Enhance your skills in Cyber Security Risk Management – join our Cyber Security Risk Management Course and lead the field!
How to Impress with Your Cyber Security Work Experience?
Your work experience section is crucial for demonstrating your qualifications and expertise. Here are some best practices for crafting an impressive work experience section.
Best Practices for Your Work Experience Section
The following are the best practices for Your Work Experience Section:
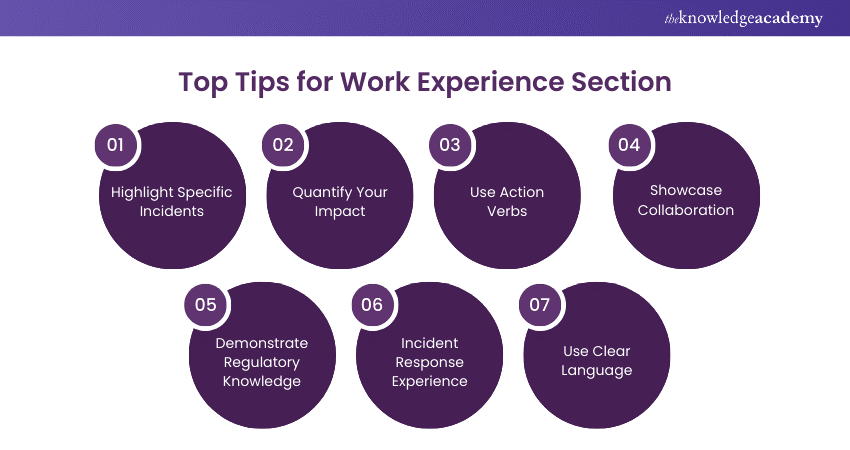
a) Highlight Specific Incidents: Focus on specific security incidents you have handled, emphasising your role in mitigating the threat and preventing future incidents.
b) Quantify Your Impact: Use metrics such as reduced downtime, increased system availability, or reduced response time.
c) Use Action Verbs: Start every sentence with a strong action verb like "developed," "implemented," "monitored," or "led."
d) Showcase Collaboration: Highlight how you work with the IT, legal, and compliance teams to ensure security rules and procedures are followed.
e) Demonstrate Regulatory Knowledge: Demonstrate your awareness of industry legislation and compliance standards, including PCI DSS and HIPAA.
f) Incident Response Experience: Briefly explain your experience with crisis response strategy and execution, including tabletop exercises and post-event analysis.
g) Use Clear Language: Use simple and short sentences and avoid technical jargon that HR, recruiters, and hiring managers may not understand.
Example Work Experiences for Cyber Security
a) Developed and implemented a comprehensive security program for [Company name], reducing security incidents by 50% and increasing employee awareness and compliance by 30%.
b) Conducted penetration testing and vulnerability assessments, identifying and remediating over 100 high-risk vulnerabilities, reducing breach risk by 80%.
c) Led incident response activities for a major cyber-attack, working with internal and external teams to control the breach and minimise its impact on company activities.
d) Implemented multi-factor authentication and data encryption, significantly enhancing data protection and reducing unauthorised access risks.
e) Worked together with cross-functional teams to establish and execute security policies, ensuring compliance with industry standards.
Unlock your potential in Cyber Security with top-notch Cyber Security Training – join now to become a cyber defence expert!
How to Add CISSP to Your CV?
Follow these steps to include in CISSP Certification on your CV:
a) Certifications Section: Under the sub-title of Certifications, enter “Certified Information Systems Security Professional” based on your achievement.
b) Training Provider: List the accredited training provider you studied with, such as The Knowledge Academy.
c) Certification Date: Add the date you obtained your CISSP certification and include the 3-year expiry date.
d) Name Suffix: Add “CISSP” as a suffix to your name at the top of your CV.
How to Add CISSP to Your LinkedIn?
Follow these steps to add your CISSP credential to your LinkedIn profile, ensuring it stands out to recruiters and connections alike:
a) Log in to your LinkedIn account
b) Click on the top Menu
c) Select “Me,” then “View Profile,” and scroll down to “Accomplishments”
d) Click the “Add” or “Plus” sign
e) Choose “Certification”
f) Enter “Certified Information Systems Security Professional” as the Certification Name.
g) For Certification Authority, select “The Knowledge Academy”
h) Input your license number from your certificate.
i) For the Certification URL, you can link to The Knowledge Academy’s CISSP Training.
j) Select the date you qualified and uncheck the “This certificate does not expire” box. Set an expiry date of 3 years for your CISSP Certificate.
k) Optionally, you can add “CISSP” as a suffix to your last name on LinkedIn by editing your profile name.
Cyber Security Resume Example
|
[Name] [email id] | [Phone Number] | LinkedIn: Summary Highly skilled Cyber Security Analyst with three years of experience in reducing security incidents by 25%. Proven track record in vulnerability scans and penetration tests, remediating 75% of weaknesses. Collaborative team player with excellent monitoring and analysis skills, detecting and responding to 93% of security warnings and notifications within 25 minutes. Cyber Security Analyst January 2023 – Present a) Created and implemented a security awareness training program, which resulted in a 60% reduction in security incidents caused by employee error. b) Regular vulnerability checks and penetration tests were carried out, with 80% of security flaws identified and fixed before they could be attacked. c) Worked together with various departments to make sure that security criteria for a new product launch were met, resulting in a smooth launch with no security issues. Security Operations Center (SOC) Analyst 11/2022 – 12/2023 a) Monitored and evaluated security events and records, identifying and reacting to 94% of security alerts and notifications within 25 minutes. b) Investigated and resolved a security breach, lowering the impact on the business by 80% and averting additional damage. c) Set up and upheld security tools and systems, resulting in a 30% improvement in system dependability and availability. Security Analyst 06/2021 – 11/2022 a) Established and carried out security policies, processes, and best practices, leading to a 26% reduction in security-related incidents and breaches. b) Investigated and analysed emerging security risks and vulnerabilities, making suggestions for mitigation and prevention, which were applied and resulted in a 40% reduction in possible threats. c) Assisted in the creation of a security architecture and design, resulting in a 20% boost in system security and reliability. Skills a) Risk Assessment b) Incident Response c) Network Security d) Vulnerability Management e) Data Encryption f) Ethical Hacking g) Compliance (e.g., GDPR, HIPAA) h) Security Operations Centre Education Bachelor of Science in Cyber Security 2018-2021 Courses / Certifications a) CCSP Certification 06/2023 b) Certified Ethical Hacker (CEH) 04/2022 c) CompTIA Cyber Security Analyst (CySA+) 01/2021 |
Boost your career with our Ethical Hacking Training – join now and become a certified hacker!
Conclusion
Your Cyber Security Resume is more than just a list of qualifications; it's your ticket to making a memorable impression in a competitive industry. Thoughtfully present your skills, experience, and certifications to captivate employers and showcase your value. Use these tips to craft a standout resume that meets industry standards and impresses employers. Start now and let your resume shine!
Transform your Cyber Security career with the Certified Cyber Security Professional (CCS-PRO) Course - register today!
Frequently Asked Questions

A personal statement for a Cyber Security CV is a brief summary highlighting your skills, experience, and career goals. It emphasises your expertise in protecting systems and data from cyber threats. This statement helps you stand out to potential employers.

CISSP and Security+ serve different purposes. CISSP is an advanced certification for experienced professionals focusing on security management. Security+ is entry-level, ideal for beginners. CISSP is generally considered more prestigious and comprehensive.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Cyber Security Training, including Certified Cyber Security Professional (CCS-PRO), Cyber Security Awareness and Cyber Security Risk Management. These courses cater to different skill levels, providing comprehensive insights into Spoofing in Cyber Security.
Our IT Security & Data Protection Blogs cover a range of topics related to Cyber Security, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Cyber Security skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Thu 1st Jan 1970







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


