We may not have the course you’re looking for. If you enquire or give us a call on +44 1344 203 999 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

The world of Cyber Security faces constant challenges from new threats and attack vectors. Among these, the "Whaling Attack" stands out for its precision and targeted nature. Understanding What is Whaling Attack and how it operates can help you strengthen your defences against this specialised cyber threat.
If you're interested in learning more, this blog is for you. Here, you'll discover What is Whaling Attack, how it works, its consequences, and how to protect against it. Let's dive in!
Table of Contents
1) Understanding What is Whaling Attacks
2) How Whaling Differs from Traditional Phishing?
3) How do Whaling Attacks Work?
4) How to Recognise a Whaling Attack?
5) The Consequences of Whaling Attacks
6) Conclusion
Understanding What is Whaling Attacks
A Whaling Attack is a specialised form of phishing that targets high-profile individuals within an organisation, such as top executives, managers, or key decision-makers. These targets are often referred to as "whales" due to their significant value to attackers.
Whaling attacks are especially dangerous because they exploit the authority and influence of these individuals to access sensitive information, including corporate secrets, financial data, and intellectual property.
What is a Whaling Phishing Attack?
Whaling Phishing is a deceptive practice in which cybercriminals craft convincing emails, messages, or websites to deceive high-level targets into revealing confidential information, clicking on malicious links, or downloading malware. These attacks often exploit the trust and authority associated with these individuals, making them more likely to fall victim to the scam.
Examples of Whaling Attacks
In order to provide a clearer understanding of What is Whaling Attack and how it operates, let's explore a few real-world examples:
1) CEO Fraud
In this scenario, an attacker impersonates the CEO or another high-ranking executive and sends an email to the finance department requesting an urgent transfer of funds to a specified account. Due to the apparent authority of the sender, the finance team may comply, resulting in financial loss.
2) Legal Department Scam
In this case, an attacker impersonates the organisation's legal counsel and sends an email to an employee. The email claims that the employee needs to review a sensitive legal document immediately. The employee, fearing legal repercussions, opens the malicious attachment or link. This allows the attacker to get access to the company's systems.
Elevate your defences against digital manipulation with our Social Engineering Training – Sign up now!
How Whaling Differs from Traditional Phishing?
It is important to understand the differences between Whaling Attacks and traditional Phishing schemes. The strategies used in these attacks are completely distinct. Let’s take a closer look at the differences between what is a Whaling Attack and what is a Traditional Phishing attack:
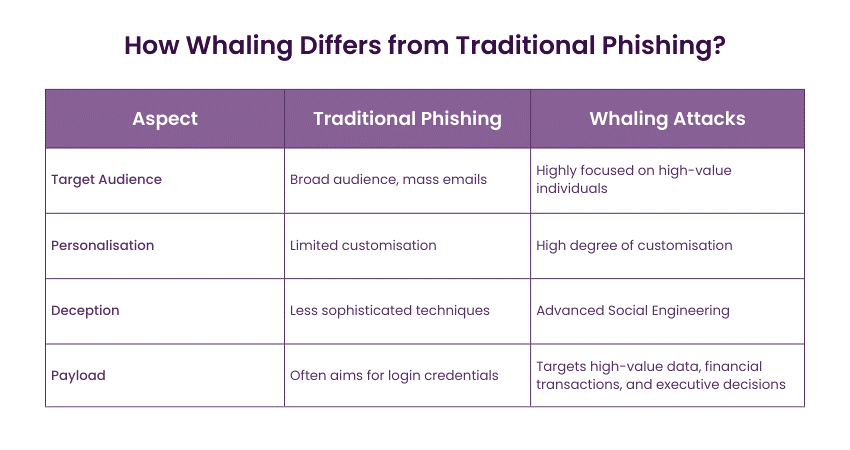
1) Target Audience: Traditional Phishing targets a broad audience. It often sends out mass emails to countless recipients, hoping that some will take the bait. In contrast, Whaling Attacks are highly focused and target specific high-value individuals. This specificity is what sets them apart.
2) Personalisation: Whaling attacks involve a high degree of personalisation. Attackers research their targets, gather information about their professional roles and personal interests, and use this data to craft convincing messages. This level of customisation makes it difficult for the victim to discern the email's malicious intent.
3) Deception: Whaling attacks often rely on Social Engineering techniques to manipulate the target. They might impersonate trusted colleagues, partners, or executives, creating a sense of urgency or authority to deceive the victim. Traditional Phishing attacks tend to be less sophisticated in their approach.
4) Payload: While traditional Phishing might aim to compromise an email account or extract login credentials, Whaling Attacks often have more significant objectives. These attacks can target high-value data, financial transactions, or even executive decisions.
How do Whaling Attacks Work?
Understanding the mechanics of Whaling Attacks is important for bolstering your defences against them. Let’s explore the key aspects of how Whaling Attacks operate:

1) Target Selection: Whaling attackers carefully choose their targets. They focus on high-ranking individuals within organisations, such as CEOs, CFOs, or other executives. These individuals have access to valuable information and the authority to make important decisions.
2) Reconnaissance: Attackers conduct extensive reconnaissance on their selected targets. They gather information from various sources, including social media, company websites, and professional networking platforms. This research allows them to personalise their attacks effectively.
3) Deceptive Messages: Attackers craft convincing messages, such as emails or social engineering campaigns. These messages often appear to come from trusted sources, such as colleagues or superiors and may reference specific projects, events, or internal matters to enhance credibility.
4) Impersonation: Impersonation is a key component of Whaling Attacks. Attackers use the name, title, and contact information of a legitimate individual within the organisation, often a CEO. They instruct the target to take urgent actions, such as transferring funds, sharing sensitive information, or clicking on a malicious link.
5) Emotional Manipulation: Whaling attackers skilfully manipulate the emotions of their targets. They create a sense of urgency in their messages, using phrases like "immediate action required" or "confidential and time sensitive." These emotional triggers make the target more likely to act without questioning the legitimacy of the request.
Understanding these elements of a Whaling Attack is essential for individuals and organisations to recognise and defend against these highly sophisticated and targeted Cyber Security Attacks and threats.
How to Recognise a Whaling Attack?
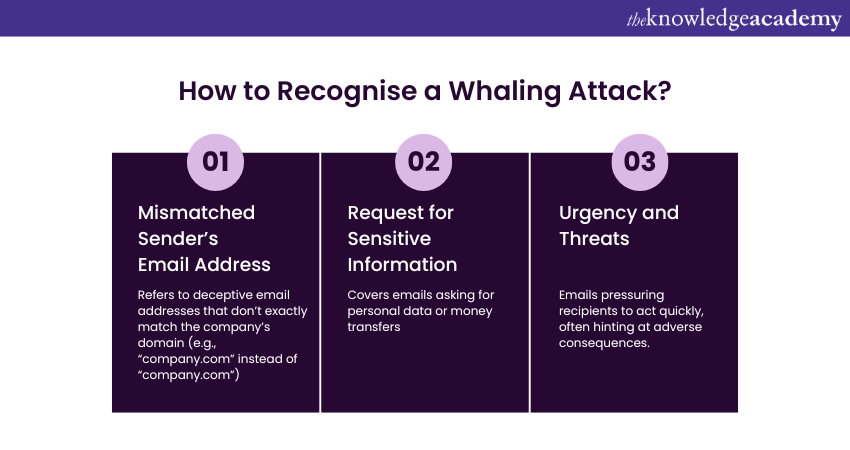
Whaling attacks are significantly more difficult to detect compared to standard phishing attacks because attackers invest considerable effort to make their emails and websites appear legitimate. Here are some common indicators that an email might be part of a Whaling Attack:
1) The sender’s email address is a close but incorrect match to the company’s domain. For instance, attackers may substitute an “m” with an “r” and an “n” (e.g., "rn") to deceive the recipient.
2) The email requests sensitive information or asks for a money transfer.
3) There is a sense of urgency, often accompanied by a subtle threat of negative consequences if the action is not taken immediately.
How to Defend Against Whaling Attacks?
Defending against Whaling Attacks requires a combination of proactive measures and user education. Here are the key strategies to protect against these highly sophisticated and targeted cyber threats:
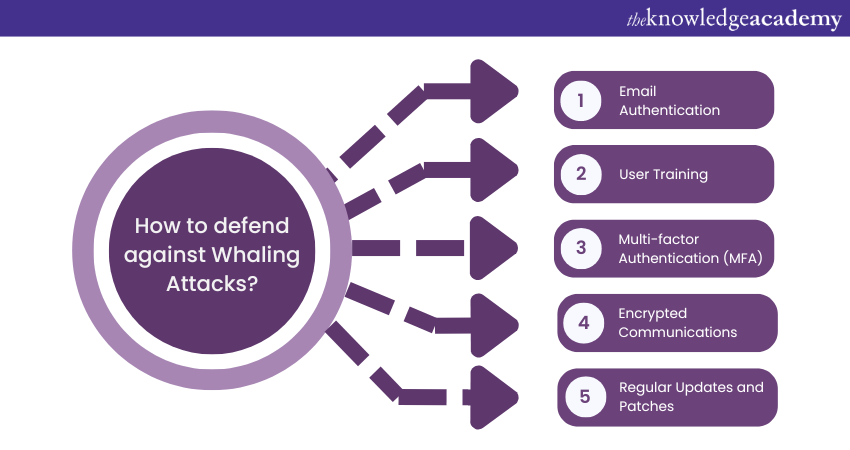
1) Email Authentication: Implement email authentication protocols like DMARC, DKIM, and SPF to verify the authenticity of incoming emails. This helps prevent spoofed domains and addresses.
2) User Training: High-value individuals and employees should receive training on recognising Phishing attempts and suspicious emails. Education is an important element in reducing the risk of falling victim to Whaling Attacks.
3) Multi-factor Authentication (MFA): MFA adds an extra layer of security by requiring multiple forms of verification to access accounts or systems. This makes it more challenging for attackers to gain unauthorised access.
4) Encrypted Communications: Encrypted email communication can protect sensitive information from being intercepted or tampered with during transmission.
5) Regular Updates and Patches: Keep software, operating systems, and security tools up to date to minimise vulnerabilities that attackers could exploit.
The Consequences of Whaling Attacks
Whaling attacks can have severe consequences for both individuals and organisations. Let's explore some of these consequences below:
1) Financial Loss: Whaling attacks can lead to significant financial losses if attackers get access to sensitive financial information or manipulate high-ranking individuals into authorising fraudulent transactions.
2) Data Breaches: High-value data, such as intellectual property, business strategies, or customer data, is often the target of Whaling Attacks. A successful breach can result in data leaks or theft, impacting an organisation's reputation and compliance.
3) Reputational Damage: When a high-profile individual falls victim to a Whaling Attack, it can damage their personal reputation and that of the organisation. Customers, partners, and stakeholders may lose trust in the victim's ability to protect sensitive information.
4) Legal and Regulatory Issues: If a Whaling Attack results in data breaches, an organisation may face legal and regulatory consequences. This includes fines and legal action.
Elevate your Cyber Security expertise with our Certified Cyber Security Professional (CCS-PRO) Course – Sign up today!
Conclusion
We hope you read and understand What is Whaling Attack. Whaling Attacks pose a targeted and sophisticated threat in the Cyber Security landscape. Understanding their nature and employing proactive defence measures is essential for safeguarding high-value individuals and organisations against potentially devastating cyber breaches.
Empower your digital fortress and take control with our Cyber Security Training – Sign up now!
Frequently Asked Questions

Whaling is a type of spear-phishing attack targeting high-level executives. Attackers impersonate trusted entities to trick victims into revealing sensitive information or transferring funds to fraudulent accounts.

If your organisation is under a phishing attack, sensitive data can be compromised, financial losses incurred, and trust damaged. Immediate action is crucial: isolate affected systems, inform stakeholders, and enhance security measures to prevent further breaches.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs, videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.

The Knowledge Academy offers various Cyber Security Courses, including the Certified Cyber Security Professional Course, Cyber Security Awareness Course, and Cyber Security Risk Management Course. These courses cater to different skill levels, providing comprehensive insights into Information Security Risk Management.
Our IT Security & Data Protection Blogs cover a range of topics related to Cyber Security, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Cyber Security skills, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Security & Data Protection Resources Batches & Dates
Date
 Certified Cyber Security Professional (CCS-PRO)
Certified Cyber Security Professional (CCS-PRO)
Fri 6th Dec 2024
Fri 21st Mar 2025
Fri 23rd May 2025
Fri 22nd Aug 2025
Fri 5th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


