We may not have the course you’re looking for. If you enquire or give us a call on + 1-866 272 8822 and speak to our training experts, we may still be able to help with your training requirements.
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.

Using a VPN enables you to mask your IP address for safeguarding your online activities, gaining access to regionally restricted content on streaming platforms, and potentially reducing costs on online purchases by selecting a more advantageous location. Indeed, you might view these services as a universal solution for all your online privacy and security requirements.
Nevertheless, like most things, there's a flip side to it. Understanding the drawbacks and acknowledging the constraints of VPNs can assist you in making well-informed choices concerning your browsing experience, online security, and privacy. This blog explores some Disadvantages of VPNs that it is essential for you to be mindful of.
Table of Contents
1) Disadvantages of VPN
a) Slow connection speeds
b) Increased data consumption
c) Some online services prohibit VPN usage
d) No protection against malware or phishing
e) VPNs don't ensure complete anonymity
f) Your VPN service determines your privacy level
g) VPN usage may be illegal in certain countries
h) Certain providers retain VPN logs
i) Effective VPNs come with a price
j) Bypassing restrictions isn't always Feasible
2) Conclusion
Disadvantages of VPN
The following are the Disadvantages of VPN:
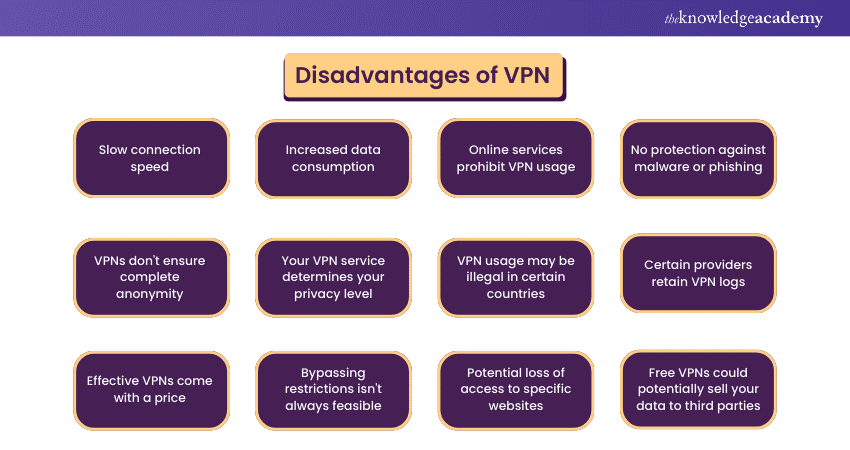
1) Slow connection speed
One of the most frequently reported drawbacks of VPN usage is the diminished connection speeds. VPNs introduce an additional layer of encryption and rerouting, which can slow down internet performance. The extent of this lag becomes particularly noticeable when engaging in activities that demand substantial bandwidth, such as streaming high-definition videos or participating in online gaming. Users may experience frustrating delays, significantly impacting the overall user experience.
To delve deeper into this issue, it's essential to understand that the encryption process, while crucial for securing data, introduces a delay in transmission. This delay is inherent in the technology and varies based on factors such as the encryption protocol, the distance between the user and the VPN server, and the server's workload.
2) Increased data consumption
While VPNs are designed to fortify security and privacy, they come at the cost of increased data consumption. The encryption of data packets before transmission inevitably leads to larger file sizes, resulting in higher data usage. This could pose a significant concern for individuals with limited data plans or those residing in regions with relatively high internet costs.
Elaborating on this point, the encryption process adds overhead to each data packet, making them larger than their non-encrypted counterparts. Consequently, users may reach their data caps more quickly, potentially leading to additional costs or service limitations.
3) Online services prohibit VPN usage
In the ongoing battle against fraudulent activities and to ensure compliance with regional regulations, some online services explicitly prohibit the use of VPNs. This restriction can impede users from accessing certain websites, platforms, or services while their VPN is active. Consequently, individuals may need to toggle their VPN on and off based on online activities, creating a less seamless and user-friendly experience.
Expanding on this point, certain streaming services, online gaming platforms, or financial institutions may detect and block VPN traffic as part of their security measures. This means that users may need to compromise between using a VPN for privacy and accessing specific services prohibiting VPN usage.
Discover the fundamentals of networking with our Introduction to Networking Training – Sign up today!
4) No protection against malware or phishing
Despite the secure tunnel VPNs create for data transmission, it's crucial to recognise their limitations. VPNs primarily focus on encrypting data during transit, offering no inherent protection against malware or phishing attacks. Users must still rely on additional cybersecurity measures, such as antivirus software and vigilant browsing habits, to guard against these prevalent online threats.
While VPNs safeguard the confidentiality and integrity of data as it travels between the user and the VPN server, they do not inspect the content of the data for malicious elements. Therefore, users must complement their VPN usage with other cybersecurity tools to ensure comprehensive protection against various online threats.
5) VPNs don't ensure complete anonymity
Despite the widespread perception that VPNs provide absolute anonymity, the reality is more nuanced. The efficacy of anonymity depends on various factors, including the VPN service provider's policies, the user's online behaviour, and the legal jurisdiction in which the VPN operates. Users should be aware that specific vulnerabilities may compromise the presumed anonymity offered by VPNs.
To delve into this point, it's important to note that VPNs primarily anonymise users by masking their IP addresses. However, other identifying information, such as browser fingerprints or login credentials, may still be accessible to websites and online services. Additionally, the logging policies of VPN providers play a crucial role; if a VPN service retains user logs, the potential for compromising user anonymity increases.
6) Your VPN service determines your privacy level
The level of privacy afforded by a VPN is dependent upon the trustworthiness of the chosen service provider. Some VPNs may log user activities, including websites visited and data transmitted, raising concerns about the confidentiality of user information. To mitigate this risk, users must meticulously research and select a reputable VPN provider with a transparent privacy policy.
Users should consider factors such as the jurisdiction in which the VPN provider operates, as data retention and privacy laws vary between countries. A VPN provider's commitment to a no-logs policy is crucial for users seeking more privacy and confidentiality in their online activities.
7) VPN usage may be illegal in certain countries
While VPNs are generally legal and widely used in many regions, some countries impose strict regulations or outright bans. In these jurisdictions, individuals caught using a VPN may face legal repercussions. Before deploying a VPN, users should familiarise themselves with the laws governing their location to avoid potential legal complications.
To delve deeper into this issue, some countries restrict VPN usage to maintain control over internet access, monitor online activities, or prevent censorship circumvention. Users residing in or travelling to such regions should exercise caution and adhere to local regulations to avoid legal consequences.
8) Certain providers retain VPN logs
Despite the promise of privacy, some VPN providers retain logs of user activities. This practice may be a requirement to comply with legal obligations or, in some cases, a result of less ethical business practices. Users should scrutinise the logging policies of their chosen VPN provider to ensure alignment with their privacy expectations.
Expanding on this, the retention of logs introduces the potential for third-party access to sensitive user information. In cases where a VPN provider is compelled by law to surrender user logs, users' privacy is compromised. Users must opt for VPN providers that are transparent about their logging practices and adhere to a strict no-logs policy.
Establish a strong IT foundation with our IT Fundamentals Training – Sign up now!
9) Effective VPNs come with a price
While free VPN services exist, they often come with limitations and potential risks. Premium VPNs that offer robust security features and reliable performance typically come with a price tag. Users seeking a trustworthy and high-quality VPN experience may need to invest in a premium subscription, making it less accessible for budget-conscious individuals.
Free VPNs may lack the advanced features, server infrastructure, and security protocols that premium counterparts provide. Additionally, free VPNs often rely on alternative revenue streams, such as serving ads or selling user data, to sustain their operations. Users should carefully consider the trade-offs between the cost of a premium VPN and the potential risks associated with using a free service.
10) Bypassing restrictions isn't always feasible
The primary allure of VPNs for many users is bypassing geographical restrictions and accessing region-restricted content. However, not all online platforms can be easily circumvented. Some services employ sophisticated detection mechanisms that can identify and block VPN traffic, preventing the user from accessing the desired content.
Expanding on this, content providers, particularly streaming services, invest in advanced technologies to detect and block VPN traffic. This is done to enforce regional licensing agreements and copyright restrictions. Users should be aware that bypassing such regulations may require efforts, and even then, it may not guarantee access to all restricted content.
11) Potential loss of access to specific websites
Users may inadvertently lose access to certain websites or online services in pursuing enhanced privacy. Some websites block IP addresses associated with VPNs to prevent unauthorised access or potential misuse. Users must weigh the trade-off between privacy and accessibility, considering the specific online activities that are essential to them.
To elaborate, websites employing strict security measures may interpret VPN usage as suspicious behaviour. Consequently, users may face access restrictions or challenges in accessing certain services. This underscores the importance of users evaluating their priorities and determining the level of privacy they are willing to trade for seamless access to online content.
12) Free VPNs could potentially sell your data to third parties
The adage "there's no such thing as a free lunch" rings true in free VPNs. Many free VPN services sustain themselves by monetising user data and selling it to third-party advertisers or other entities. Users opting for free VPNs should exercise caution and thoroughly investigate the provider's business model to ensure their data is not exploited for financial gain.
Expanding on this, the operational costs of providing VPN services are substantial, and free VPNs often seek alternative revenue streams to cover these expenses. Selling user data to third parties is a common practice among free VPNs, compromising user privacy and potentially leading to targeted advertising or other privacy-related issues. Users must carefully assess free VPN providers' privacy policies and business models to make informed decisions about the trade-offs involved.
Learn about security-based and layer-based VPN architectures with our VPN Training today!
Conclusion
Prior to enrolling in a VPN service, it is crucial to comprehend its potential drawbacks and limitations. This knowledge will empower you to make an informed decision that aligns with your online privacy and security requirements. We hope you have understood the Disadvantages of VPN through this blog!
Stay ahead in the digital world with our Cloudflare Training – Sign up now!
Frequently Asked Questions

Using a VPN can lead to slower connection speeds due to the encryption and rerouting processes, hindering activities like streaming and online gaming. Additionally, increased data consumption is common as encrypted data packets are larger. Some online services prohibit VPN usage, impacting accessibility. VPNs also lack inherent protection against malware or phishing, requiring users to rely on additional cybersecurity measures. While often associated with anonymity, VPNs don't guarantee complete privacy, and the level of confidentiality depends on the chosen service provider. Legal considerations should be noted, as VPN usage may be illegal in certain countries.

A prevalent issue with VPNs is the potential for reduced connection speeds, impacting user experience, especially during bandwidth-intensive activities. Additionally, VPNs may encounter compatibility issues with certain online services that explicitly prohibit their usage. Another common problem is the misconception that VPNs provide absolute anonymity; users must be aware that their privacy depends on factors like the VPN provider's policies and jurisdiction. Trustworthiness of the VPN service is crucial as some providers may retain logs of user activities, potentially compromising privacy. Legal considerations also arise, as VPN usage may be prohibited or regulated in certain regions.

Site-to-site VPNs, while providing secure communication between networks, have drawbacks. These VPNs often require substantial configuration and maintenance efforts, making them complex to manage. Compatibility issues may arise between different vendor implementations, posing challenges for seamless integration. Additionally, site-to-site VPNs may be less flexible in adapting to dynamic changes in network topology. The need for dedicated hardware and infrastructure may increase costs. The reliance on a centralised architecture can lead to a single point of failure, impacting the overall network's reliability. Careful consideration of these factors is essential when implementing site-to-site VPNs.

The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, blogs, videos, webinars, and interview questions. To Tailor learning experiences further, professionals can maximise value with customisable Course Bundles of TKA.

The Knowledge Academy offers various IT Support and Solution Courses, including Cloudflare Training, IT Fundamentals Training, and Introduction to Networking Training. These courses cater to different skill levels, providing comprehensive insights into IT Support and Solution methodologies.
Our IT Support and Solution blogs cover a range of topics related to PRINCE2, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your IT Support and Solution skills, The Knowledge Academy's diverse courses and informative blogs have you covered.

The Knowledge Academy’s Knowledge Pass, a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.
Upcoming IT Infrastructure & Networking Resources Batches & Dates
Date
 CloudFlare Training
CloudFlare Training
Fri 29th Nov 2024
Fri 17th Jan 2025
Fri 21st Feb 2025
Fri 4th Apr 2025
Fri 6th Jun 2025
Fri 25th Jul 2025
Fri 7th Nov 2025
Fri 26th Dec 2025







 Top Rated Course
Top Rated Course



 If you wish to make any changes to your course, please
If you wish to make any changes to your course, please


